kdflnglkdg
Feature Flag Manager
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
200 XP
In this article, we will run a couple of CLI commands that help a forensic investigator to gather volatile data from the system as much as possible. The commands which we use in this post are not the whole list of commands, but these are most commonly used once.
As per forensic investigator, create a folder on the desktop name “case” and inside create another subfolder named as “case01” and then use an empty document “volatile.txt” to save the output which you will extract.
Here I have saved all the output inside /SKS19/prac/notes.txt which help us creating an investigation report.
Table of Content
What is Volatile Data?
There are two types of data collected in Computer Forensics Persistent data and Volatile data. Persistent data is that data that is stored on a local hard drive and it is preserved when the computer is OFF. Volatile data is any kind of data that is stored in memory, which will be lost when computer power or OFF.
Volatile data resides in the registry’s cache and random access memory (RAM). This investigation of the volatile data is called “live forensics”.
System Information
It is a system profiler included with Microsoft Windows that displays diagnostic and troubleshooting information related to the operating system, hardware, and software.
We can collect this volatile data with the help of commands. All we need is to type this command.
It will save all the data in this text file. We check whether this file is created or not by [ dir ] command to compare the size of the file each time after executing every command.
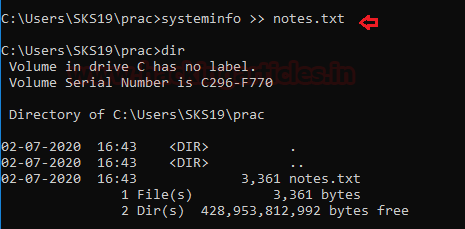
Now, go to this location to see the results of this command. Where it will show all the system information about our system software and hardware.

Currently Available Network Connections
Network connectivity describes the extensive process of connecting various parts of a network. With the help of routers, switches, and gateways.
We can check all the currently available network connections through the command line.
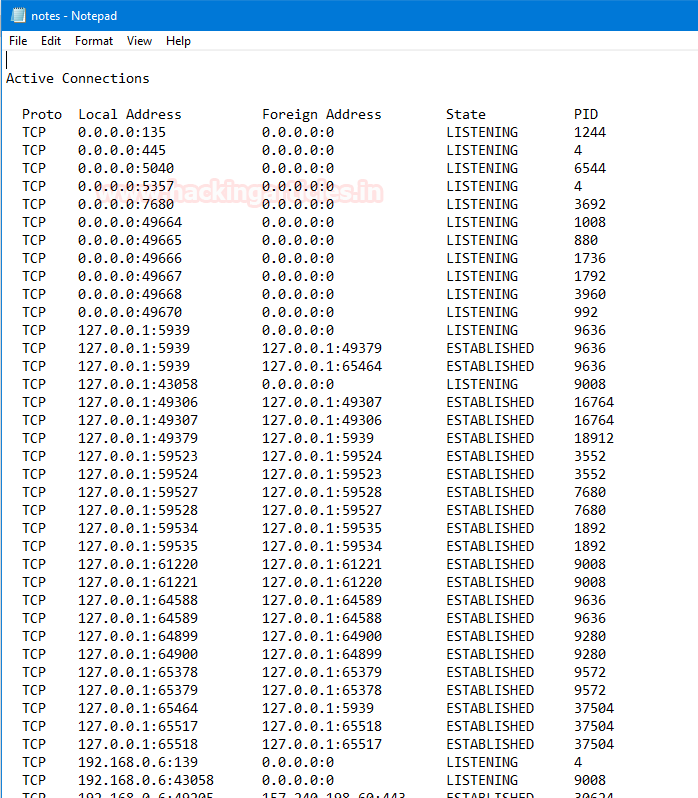
we can check whether it is created or not with the help of [dir] command as you can see, now the size of the get increased.

Now, open that text file to see all active connections in the system right now. It will also provide us with some extra details like state, PID, address, protocol.
Routing Configuration
It specifies the correct IP addresses and router settings. Host configuration: sets up a network connection on a host computer or laptop by logging the default network settings, such as IP address, proxy, network name, and ID/password.
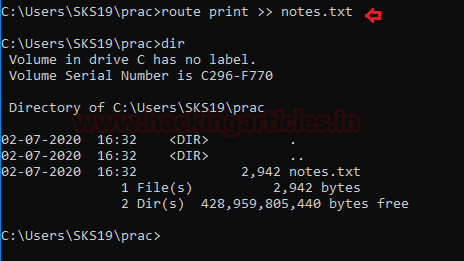
To know the Router configuration in our network follows this command.
We can check the file with [dir] command.
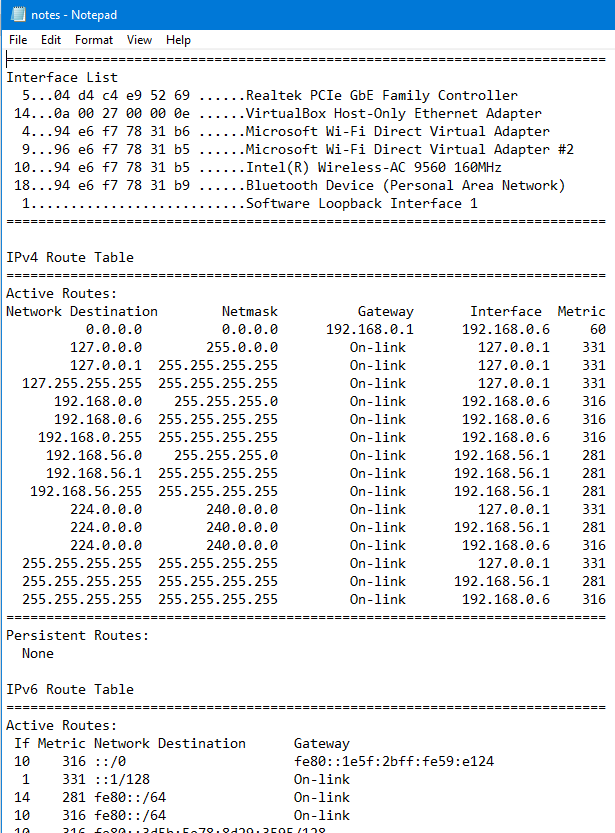
Open the txt file to evaluate the results of this command. Like the Router table and its settings.
Date and Time
To know the date and time of the system we can follow this command. We can also check the file is created or not with the help of [dir] command.

Open that file to see the data gathered with the command.

System Variables
A System variable is a dynamic named value that can affect the way running processes will behave on the computer. They are part of the system in which processes are running. For Example, a running process can query the value of the TEMP environment variable to discover a suitable location to store temporary files.
We can check all system variable set in a system with a single command.
We can check whether the file is created or not with [dir] command.

Now, open the text file to see set system variables in the system.

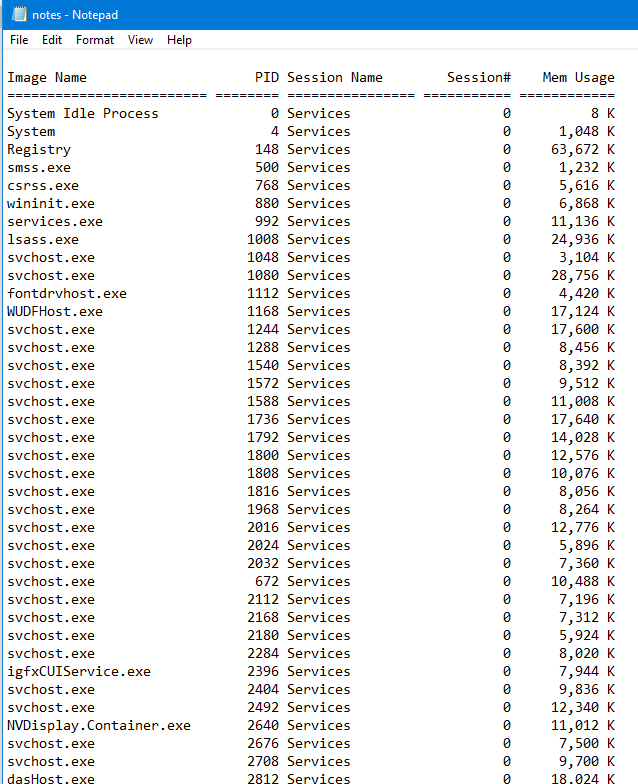
Task List
A Task list is a menu that appears in Microsoft Windows, It will provide a list of running applications in the system. To get the task list of the system along with its process id and memory usage follow this command.
we can also check whether the text file is created or not with [dir] command.

Open the text file to evaluate the details.
Task List with Modules
With the help of task list modules, we can see the working of modules in terms of the particular task. We can see that results in our investigation with the help of the following command.
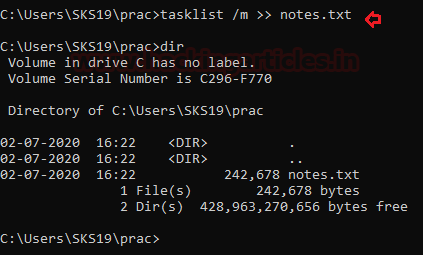
we can check whether our result file is created or not with the help of [dir] command.
Open the text file to evaluate the command results.

Task List with Services
It will showcase all the services taken by a particular task to operate its action. We get these results in our Forensic report by using this command.
we check whether the text file is created or not with the help [dir] command.
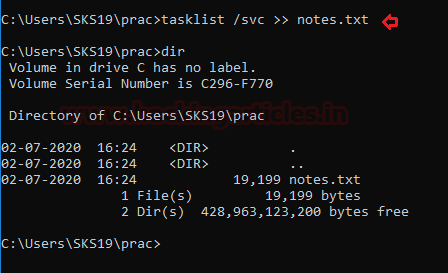
Open this text file to evaluate the results. It will showcase the services used by each task.

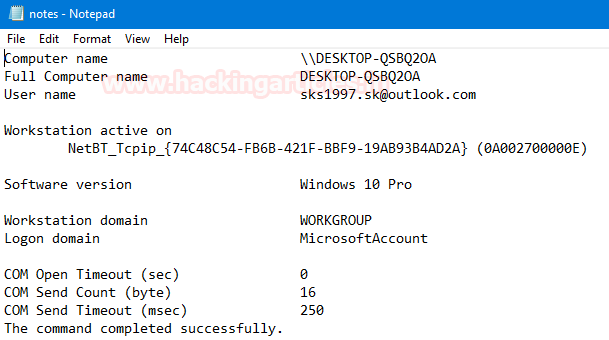
Workstation Information
A workstation is known as a special computer designed for technical or scientific applications intended primarily to be used by one person at a time. They are commonly connected to a LAN and run multi-user operating systems. Follow these commands to get our workstation details.
to check whether the file is created or not use [dir] command.
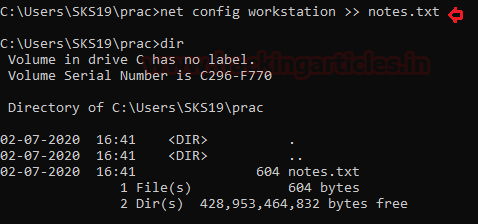
Now, open the text file to see the investigation results.
MAC Address saved in System ARP Cache
There are two types of ARP entries- static and dynamic. Most of the time, we will use the dynamic ARP entries. This means that the ARP entries kept on a device for some period of time, as long as it is being used.
The opposite of a dynamic, if ARP entry is the static entry we need to enter a manual link between the Ethernet MAC Address and IP Address. Because of management headaches and the lack of significant negatives. We use dynamic most of the time. To get that details in the investigation follow this command.
we can whether the text file is created or not with [dir] command.

Now, open the text file to see the investigation report.

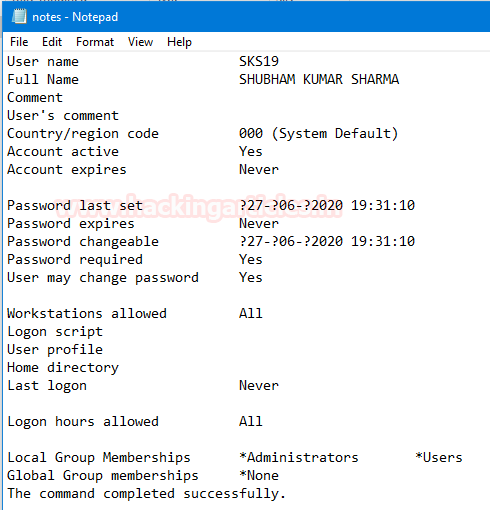
System User Details
A user is a person who is utilizing a computer or network service. Users of computer systems and software products generally lack the technical expertise required to fully understand how they work. To get that user details to follow this command.
we can use [dir] command to check the file is created or not.

Now, open a text file to see the investigation report.
DNS Configuration
DNS is the internet system for converting alphabetic names into the numeric IP address. When a web address is typed into the browser, DNS servers return the IP address of the webserver associated with that name. To know the system DNS configuration follow this command.
we can see the text report is created or not with [dir] command.

Now open the text file to see the text report.

System network shares
A shared network would mean a common Wi-Fi or LAN connection. The same is possible for another folder on the system. By turning on network sharing and allowing certain or restricted rights, these folders can be viewed by other users/computers on the same network services. We can see these details by following this command.
we can also check the file it is created or not with [dir] command.

Now, open that text file to see the investigation report.

Network Configuration
Network configuration is the process of setting a network’s controls, flow, and operation to support the network communication of an organization and/or network owner. This term incorporates the multiple configurations and steps up processes on network hardware, software, and other supporting devices and components. To get the network details follow these commands.
As usual, we can check the file is created or not with [dir] commands.
Now, open the text file to see the investigation report.
As we said earlier these are one of few commands which are commonly used. There are plenty of commands left in the Forensic Investigator’s arsenal.

Author: Shubham Sharma is a Pentester and Cybersecurity Researcher, Contact Linkedin and twitter.
As per forensic investigator, create a folder on the desktop name “case” and inside create another subfolder named as “case01” and then use an empty document “volatile.txt” to save the output which you will extract.
Here I have saved all the output inside /SKS19/prac/notes.txt which help us creating an investigation report.
Table of Content
- What is Volatile Data?
- System Information
- Currently available network connections
- Routing Configuration
- Date and Time
- System Variables
- Task List
- Task List with Modules
- Task List with Service
- Workstation Information
- MAC Address save in system ARP Cache
- System User Details
- DNS configuration
- System network shares
- Network configuration
What is Volatile Data?
There are two types of data collected in Computer Forensics Persistent data and Volatile data. Persistent data is that data that is stored on a local hard drive and it is preserved when the computer is OFF. Volatile data is any kind of data that is stored in memory, which will be lost when computer power or OFF.
Volatile data resides in the registry’s cache and random access memory (RAM). This investigation of the volatile data is called “live forensics”.
System Information
It is a system profiler included with Microsoft Windows that displays diagnostic and troubleshooting information related to the operating system, hardware, and software.
We can collect this volatile data with the help of commands. All we need is to type this command.
Code:
systeminfo >> notes.txtIt will save all the data in this text file. We check whether this file is created or not by [ dir ] command to compare the size of the file each time after executing every command.

Now, go to this location to see the results of this command. Where it will show all the system information about our system software and hardware.

Currently Available Network Connections
Network connectivity describes the extensive process of connecting various parts of a network. With the help of routers, switches, and gateways.
We can check all the currently available network connections through the command line.
Code:
netstat -nao >> notes.txtwe can check whether it is created or not with the help of [dir] command as you can see, now the size of the get increased.

Now, open that text file to see all active connections in the system right now. It will also provide us with some extra details like state, PID, address, protocol.

Routing Configuration
It specifies the correct IP addresses and router settings. Host configuration: sets up a network connection on a host computer or laptop by logging the default network settings, such as IP address, proxy, network name, and ID/password.
To know the Router configuration in our network follows this command.
Code:
route print >> notes.txtWe can check the file with [dir] command.

Open the txt file to evaluate the results of this command. Like the Router table and its settings.

Date and Time
To know the date and time of the system we can follow this command. We can also check the file is created or not with the help of [dir] command.
Code:
echo %date% %time% > notes.txt
dir
Open that file to see the data gathered with the command.

System Variables
A System variable is a dynamic named value that can affect the way running processes will behave on the computer. They are part of the system in which processes are running. For Example, a running process can query the value of the TEMP environment variable to discover a suitable location to store temporary files.
We can check all system variable set in a system with a single command.
Code:
set >> notes.txtWe can check whether the file is created or not with [dir] command.
Code:
dir
Now, open the text file to see set system variables in the system.

Task List
A Task list is a menu that appears in Microsoft Windows, It will provide a list of running applications in the system. To get the task list of the system along with its process id and memory usage follow this command.
Code:
tasklist >> notes.txtwe can also check whether the text file is created or not with [dir] command.

Open the text file to evaluate the details.

Task List with Modules
With the help of task list modules, we can see the working of modules in terms of the particular task. We can see that results in our investigation with the help of the following command.
Code:
tasklist /m >> notes.txt
we can check whether our result file is created or not with the help of [dir] command.
Open the text file to evaluate the command results.

Task List with Services
It will showcase all the services taken by a particular task to operate its action. We get these results in our Forensic report by using this command.
Code:
tasklist /svc >> notes.txtwe check whether the text file is created or not with the help [dir] command.

Open this text file to evaluate the results. It will showcase the services used by each task.

Workstation Information
A workstation is known as a special computer designed for technical or scientific applications intended primarily to be used by one person at a time. They are commonly connected to a LAN and run multi-user operating systems. Follow these commands to get our workstation details.
Code:
net config workstation >> notes.txtto check whether the file is created or not use [dir] command.

Now, open the text file to see the investigation results.

MAC Address saved in System ARP Cache
There are two types of ARP entries- static and dynamic. Most of the time, we will use the dynamic ARP entries. This means that the ARP entries kept on a device for some period of time, as long as it is being used.
The opposite of a dynamic, if ARP entry is the static entry we need to enter a manual link between the Ethernet MAC Address and IP Address. Because of management headaches and the lack of significant negatives. We use dynamic most of the time. To get that details in the investigation follow this command.
Code:
arp -a >> notes.txtwe can whether the text file is created or not with [dir] command.

Now, open the text file to see the investigation report.

System User Details
A user is a person who is utilizing a computer or network service. Users of computer systems and software products generally lack the technical expertise required to fully understand how they work. To get that user details to follow this command.
Code:
net user %username% >> notes.txtwe can use [dir] command to check the file is created or not.

Now, open a text file to see the investigation report.

DNS Configuration
DNS is the internet system for converting alphabetic names into the numeric IP address. When a web address is typed into the browser, DNS servers return the IP address of the webserver associated with that name. To know the system DNS configuration follow this command.
Code:
ipconfig /displaydns >> notes.txtwe can see the text report is created or not with [dir] command.

Now open the text file to see the text report.

System network shares
A shared network would mean a common Wi-Fi or LAN connection. The same is possible for another folder on the system. By turning on network sharing and allowing certain or restricted rights, these folders can be viewed by other users/computers on the same network services. We can see these details by following this command.
Code:
net share >> notes.txtwe can also check the file it is created or not with [dir] command.

Now, open that text file to see the investigation report.

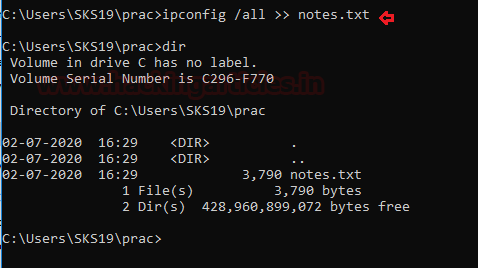
Network Configuration
Network configuration is the process of setting a network’s controls, flow, and operation to support the network communication of an organization and/or network owner. This term incorporates the multiple configurations and steps up processes on network hardware, software, and other supporting devices and components. To get the network details follow these commands.
Code:
ipconfig /all >> notes.txtAs usual, we can check the file is created or not with [dir] commands.

Now, open the text file to see the investigation report.
As we said earlier these are one of few commands which are commonly used. There are plenty of commands left in the Forensic Investigator’s arsenal.

Author: Shubham Sharma is a Pentester and Cybersecurity Researcher, Contact Linkedin and twitter.