robbas11280
Pixel Warrior
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
200 XP
Hey guys, in this tutorial we will learn how we can do Footprinting, Scanning & Enumeration of any website. For to do this used to various tool or website but with the help of this tool we can do almost everything.
About FinalRecon
FinalRecon tool are hosted on Github page and made in python language. FinalRecon tool used to web reconnaissance such as scanning, enumeration and footprinting.
Read out the features of this tool by given below.
- Headers – check server, content-tye, xff and encoding.
- SSLinfo – check security of site.
- WHOIS – lookup information about the domain
- Crawl – fetching the web pages or link from website.
- Dns – check Dns A, AAA and more records.
- Sub – find the sub domain
- Trace – can be used in order for debugging purposes
- Dir – grab the hidden directory.
- Port Scan (PS) – find the open ports.
- Full Scan – contains all above scan
Requirements
Kali Linux ( Tested on 2020.1 )
Lets get started
Installation
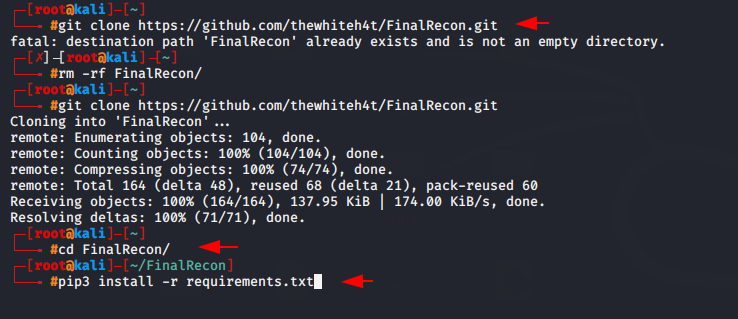
FinalRecon tool are hosted on Github page so you need to download from there by using following commands.
git clone https://github.com/thewhiteh4t/FinalRecon.git1git clone
Loading…
github.com
Go to the directory that is created after cloning.
cd FinalRecon1cd FinalRecon
This tool requires a few things which you can be complete by using following command.
pip3 install -r requirements.txt1pip3 install-rrequirements.txt
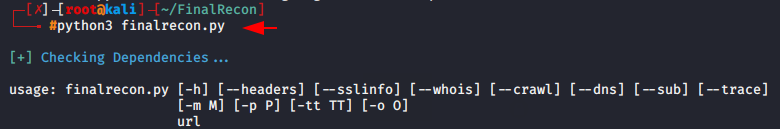
Now you are ready to execute this tool. Just execute the given command.
python3 finalrecon.py1python3 finalrecon.py
Enumerate Headers
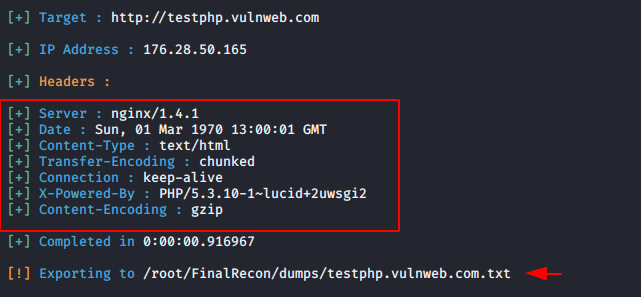
Headers contains the additional information which is used to pass between clients and the server. With the help of this option you can obtain information such as :
- server
- content-type
- encoding
- X-forword-for (XFF)
python3 finalrecon.py --headers http://testphp.vulnweb.com1python3 finalrecon.py--headers http://testphp.vulnweb.com
SSL information
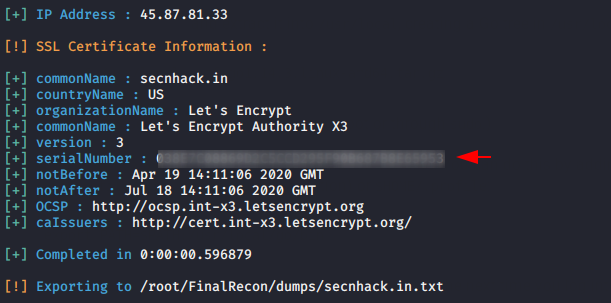
You can check the serial number, version and SSL authority etc.
python3 finalrecon.py --sslinfo https://secnhack.in1python3 finalrecon.py--sslinfo https://secnhack.in
WHOIS – Domain Footprinting
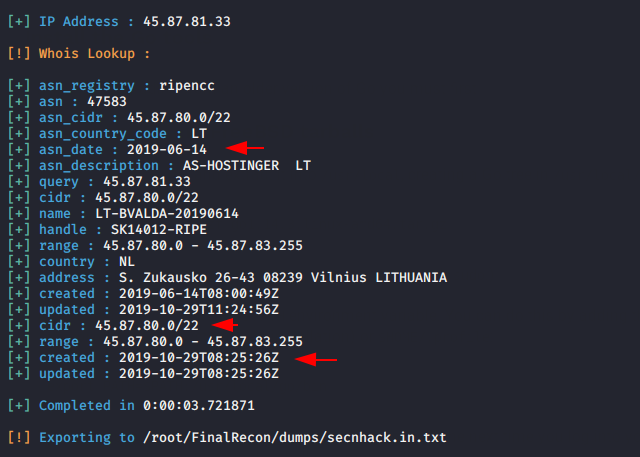
As you know that whenever person or organization register a new domian then the registration information becomes available for everyone. Hence whois is used to grab the information about the website.
python3 finalrecon.py --whois https://secnhack.in1python3 finalrecon.py--whois https://secnhack.in
Crawling – Spider Scan
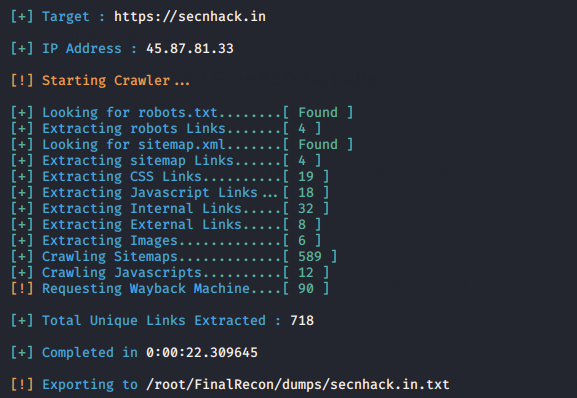
Crawling is a program whose used to fetch the web pages or link from the websites. As you will know that this features are also available in burpsuite but as spider scan.
python3 finalrecon.py --crawl https://secnhack.in1python3 finalrecon.py--crawl https://secnhack.in
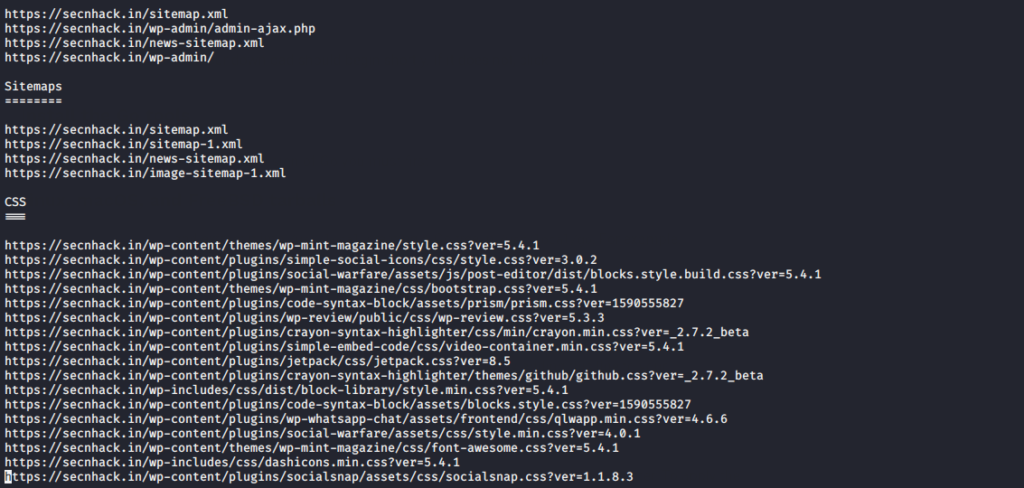
After complete the crawling You can see the results in this directory in detail.
cd /root/FinalRecon/dumps/1cd/root/FinalRecon/dumps/
DNS Footprinting
DNS Footprinting is the process to collecting information about DNS zone data, DNS records and much more.
python3 finalrecon.py --dns http://testphp.vulnweb.com/1python3 finalrecon.py--dns http://testphp.vulnweb.com/
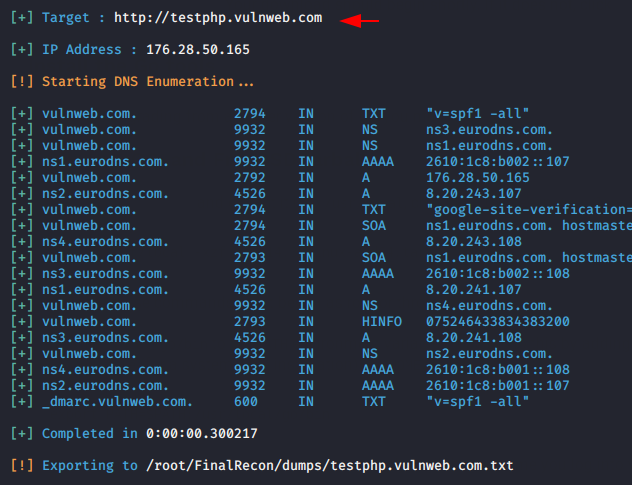
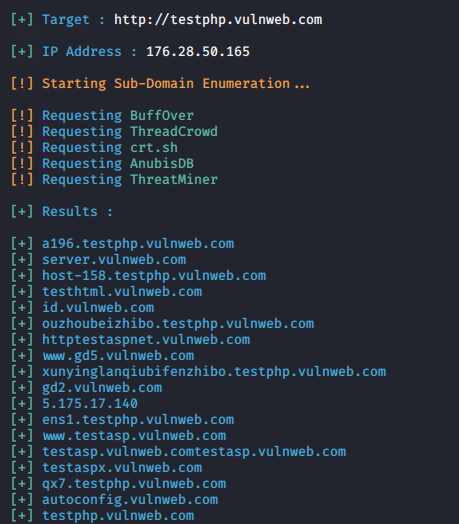
Subdomain
The subdomain is part of another domain and if you want to grab all the subdomains of the website so you can use this feature.
python3 finalrecon.py --sub http://testphp.vulnweb.com/1python3 finalrecon.py--sub http://testphp.vulnweb.com/
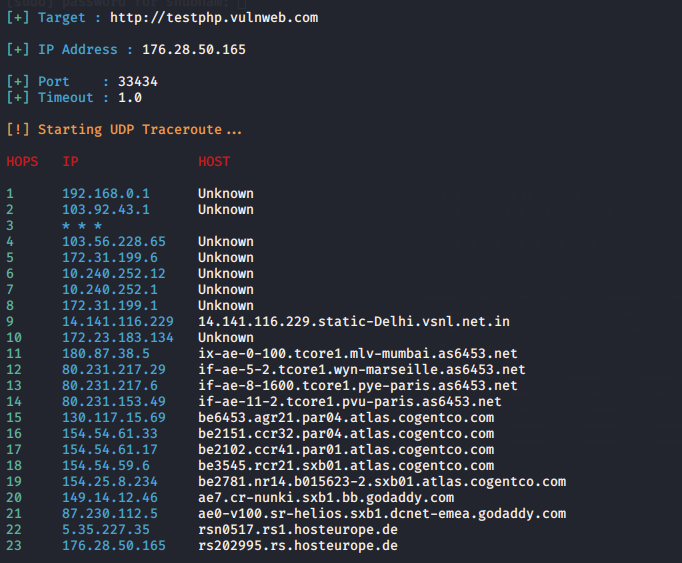
Trace
Trace method can be used in order to debugging purposes and cause of this features attacker can trace the activity of that website.
UDP Port
python3 finalrecon.py --trace http://testphp.vulnweb.com1python3 finalrecon.py--trace http://testphp.vulnweb.com
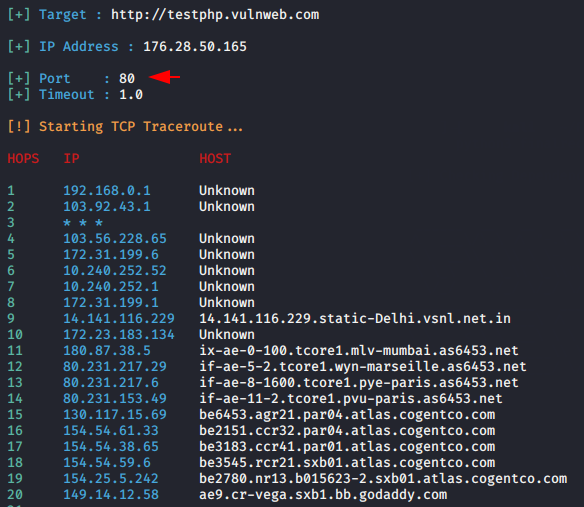
TCP Port Tracing
python3 finalrecon.py --trace http://testphp.vulnweb.com/ -m TCP1python3 finalrecon.py--trace http://testphp.vulnweb.com/ -m TCP
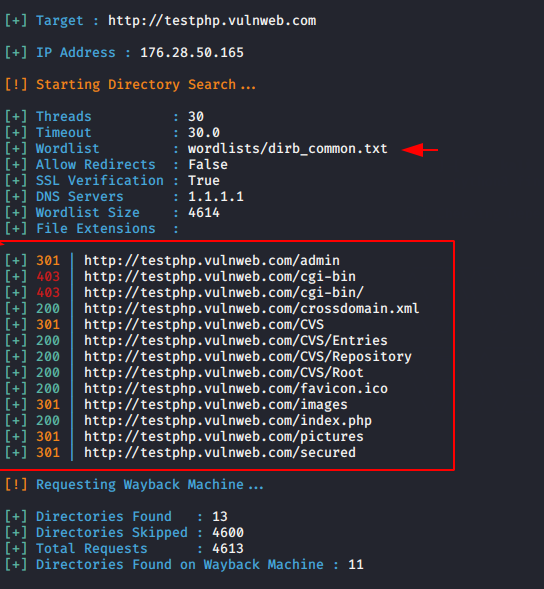
Enumerate Directory
With the help of this features you can easily find the directory which is available on that server. If you are a CTF player then this feature can help you.
python3 finalrecon.py --dir http://testphp.vulnweb.com1python3 finalrecon.py--dir http://testphp.vulnweb.com
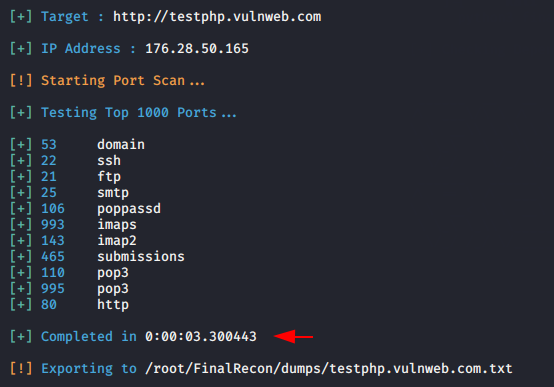
PS ( Port Scan )
It has port scanning features that will automatically scan open ports and produce results without any effort.
python3 finalrecon.py --ps http://testphp.vulnweb.com1python3 finalrecon.py--ps http://testphp.vulnweb.com
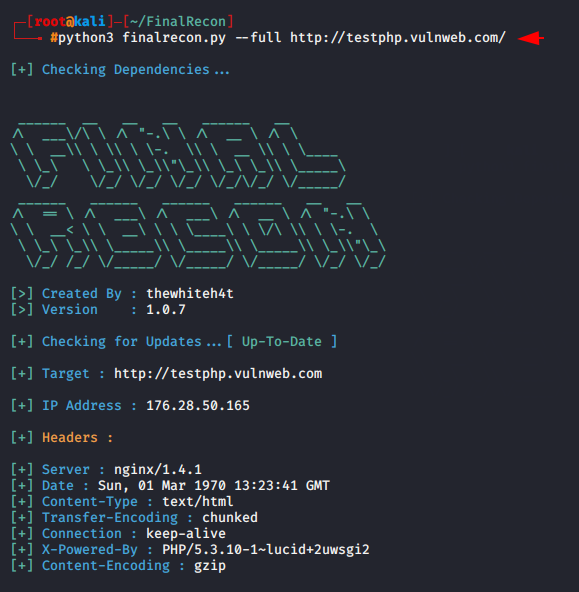
Full Reconnaissance
If you work for any organization or company and you have to enumerate the website and extract the vulnerability and give it the result as a file format then you can choose the full scan option because it perform all above scan and produce the result as file format.
python3 finalrecon.py --full http://testphp.vulnweb.com1python3 finalrecon.py--full http://testphp.vulnweb.com
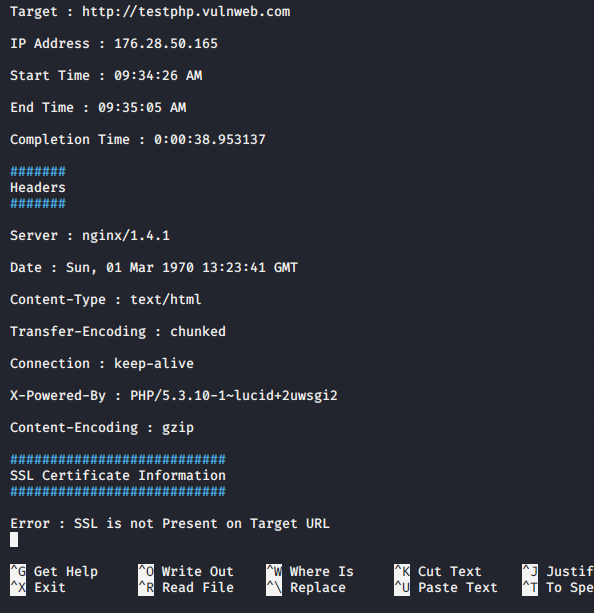
After visiting on that directory you can see the results of all scans in file.
nano /root/FinalRecon/dumps/testphp.vulnweb.com.txt1nano/root/FinalRecon/dumps/testphp.vulnweb.com.txt
Happy Security and Hacking
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.