Christianagemoh
Cyber Evidence Collector
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

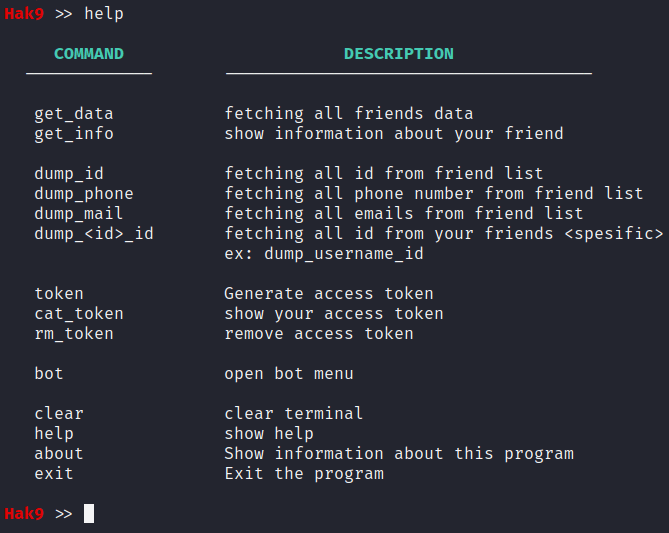
Hey Folks, in this tutorial we are going to talk about an information gathering tool called “fbi“. FBI is an accurate facebook account information gathering, all sensitive information can be easily gathered even though the target converts all of its privacy to (only me), Sensitive information about residence, date of birth, occupation, phone number and email address.
Credit : github.com
Let’s take a look
Install Dependencies
Some dependencies have to be installed before move towards installation of this tool. Just execute the following command.
apt install git python21apt install git python2
Installation
The configuration of this tool is very simple as we can easily configure it by following the given three steps. The first step is to download it using the git command, then in the second step we have to go to the directory and in the last step we can boot this tool. Very Simple
git clone https://github.com/xHak9x/fbi.git
cd fbi
python2 fbi.py123git clone
https://github.com/xHak9x/fbi.gitcd fbipython2 fbi.py
Done
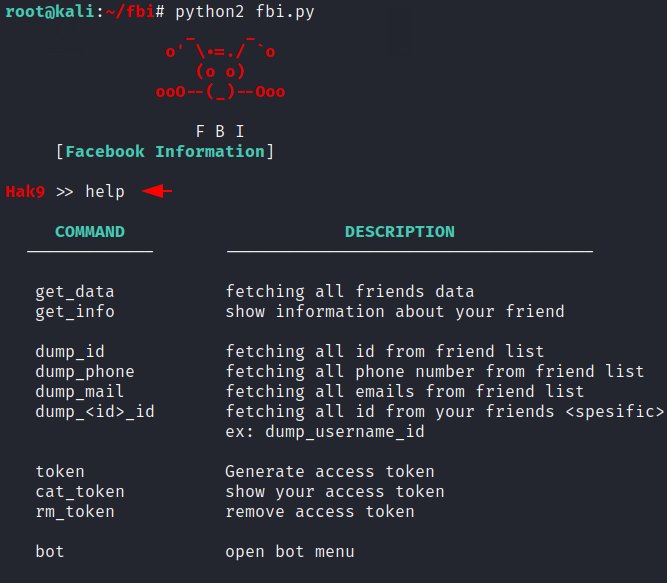
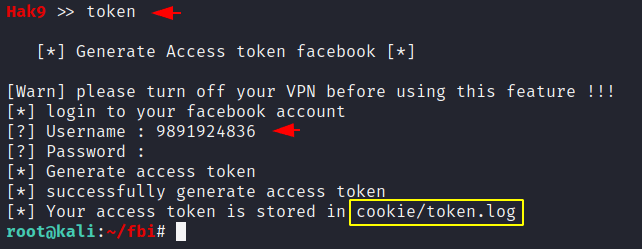
Generate Token
Basically it scraps the data of the user which is available in your friends list for which it will generate a token after entering the credentials of your facebook account.
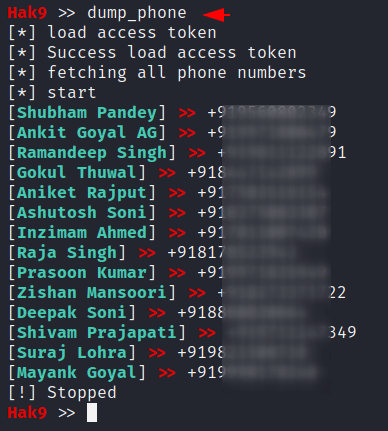
Dump Phone
After successfully authenticating with our account we can dump the phone number of all friends available on facebook at once.
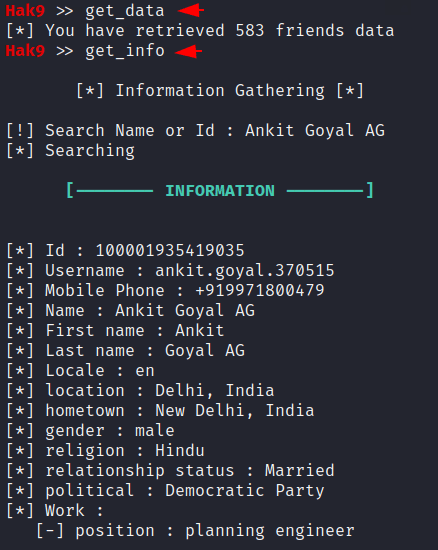
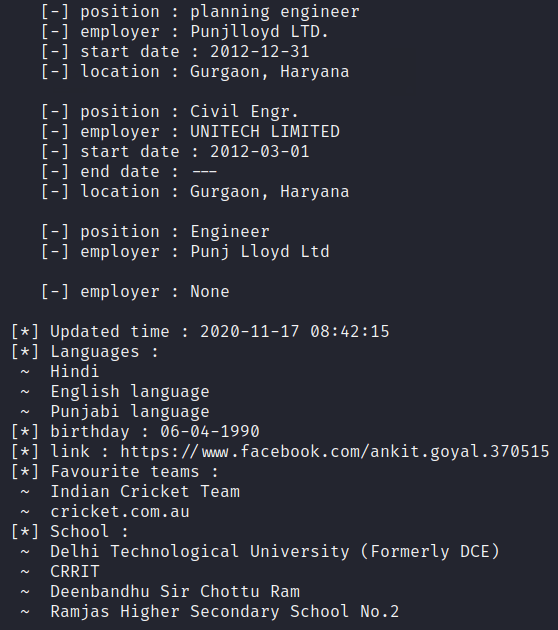
Get Data and Get Info
The “get_data” command helps the tool to get all the available information and then we can see the information about each profile using the “get_info” command. As you can see in the image below.
Impressive
Dump ID
We can easily dump the IDs of the users available in our friends list.
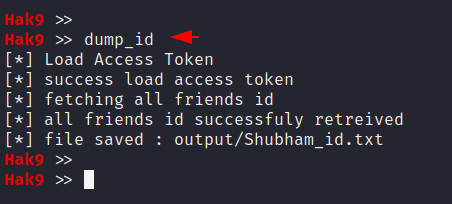
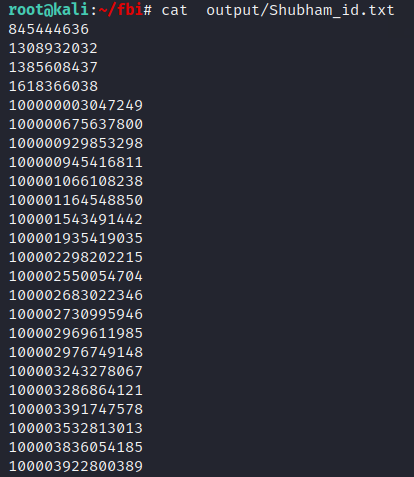
Output
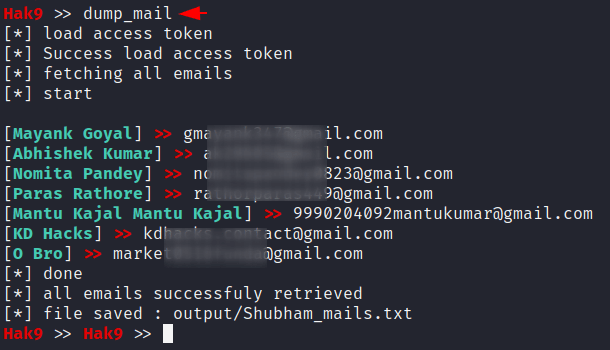
Dump Mail
As you can see, we are also able to dump the mail IDs of the users which can be a useful feature for all.
Done