Meocon354
Social Persona Designer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
While testing Tenda AC5 AC1200 over at the Hacking Articles Research Lab, we uncovered several vulnerabilities in its latest firmware version V15.03.06.47_multi.
Thereby in a heap of basic vulnerabilities, there was a one with the highest severity i.e. Stored Cross-Site Scripting.
So, let’s take a look at how we detected that.
Detecting & Exploiting the Vulnerability
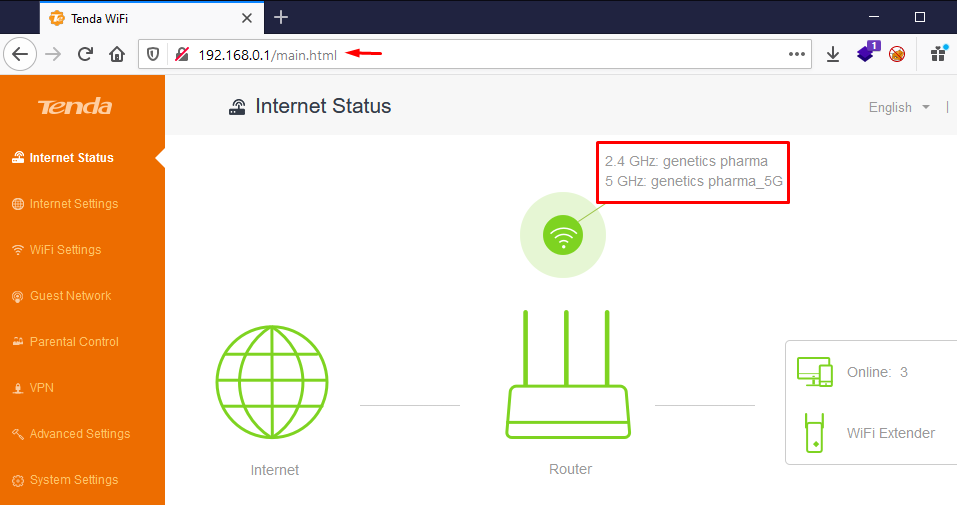
Navigating the Tenda AC1200 gateway IP i.e. 192.168.0.1 over at our browser, we got landed on the router’s main.html webpage. There we discovered that the Wi-Fi Names are displayed on the screen.
This made us scratch our head and we just switched to the Wifi Settings and hit the Wifi Name and the Password option.
And with that, we tried to manipulate the Wifi name with a Javascript code in order to hit a potential cross-site scripting attack.
Now as soon as the victim navigate back to the dashboard with the gateway IP, the browser executes up the payload dumping “1” as an alert over there.

Author: Chiragh Arora is a passionate Researcher and Technical Writer at Hacking Articles. He is a hacking enthusiast. Contact here
Thereby in a heap of basic vulnerabilities, there was a one with the highest severity i.e. Stored Cross-Site Scripting.
So, let’s take a look at how we detected that.
Detecting & Exploiting the Vulnerability
Navigating the Tenda AC1200 gateway IP i.e. 192.168.0.1 over at our browser, we got landed on the router’s main.html webpage. There we discovered that the Wi-Fi Names are displayed on the screen.

This made us scratch our head and we just switched to the Wifi Settings and hit the Wifi Name and the Password option.
And with that, we tried to manipulate the Wifi name with a Javascript code in order to hit a potential cross-site scripting attack.
Code:
<script>alert(1)</script>Now as soon as the victim navigate back to the dashboard with the gateway IP, the browser executes up the payload dumping “1” as an alert over there.

Author: Chiragh Arora is a passionate Researcher and Technical Writer at Hacking Articles. He is a hacking enthusiast. Contact here