yicoxiw
Communication Encryption Auditor
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
200 XP
In this post, you will learn how to test security loopholes in Drupal CMS for any critical vulnerability which can cause great damage to any website if found on any webserver. In this article, you will learn how a misconfigured web application can be easily exploited.
Remote Code Execution: Remote Code Evaluation is a vulnerability that occurs because of the unsafe handling of inputs by the server application or that can be exploited if user input is injected into a File or a String and executed by the programming language’s parser or the user input is not sanitised properly in POST request and also when accepting query string param during GET requests.
Therefore a Remote Code Evaluation can lead to a full compromise of the vulnerable web application and also a web server.
Let’s Begin!!
So the drupal is accessible through a web browser by exploring the following URL:
And this opens the default home page, to access the dashboard you must-have credential for login.

So, to access the user console, I used following creds.

After accessing the admin console, it was time to exploit web application by injecting malicious content inside it. Directly writing malicious scripts as web content will not give us the reverse shell of the application but after spending some time, we concluded that it requires PHP module. We, therefore, move to install new module through
You can download the PHP package for Drupal from the URL below and upload the tar file to install the new module.
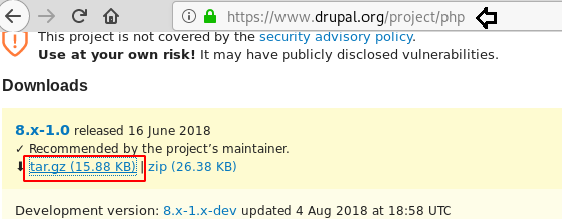
To install php module upload the tar file that was downloaded.

So, when the installation is completed, we need to enable to the added module.

Again, move to Manage > Extend >filters and enable the checkbox for PHP filters.
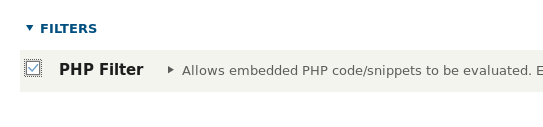
Now use the Pentest monkey PHP script, i.e. “reverse shell backdoor.php” to be injected as basic content. Don’t forget to add a “listening IP & port” to get a reversed connection. Continue to change the “text format to PHP” and enable the publishing checkbox. Keep the netcat listener ON in order to receive the incoming shell.
When everything is set accordingly, click the preview button and you’ll get the reverse connection over the netcat.

Hence, we got the reverse connection of the host machine.

Author: Komal Singh is a Cyber Security Researcher and Technical Content Writer, she is completely enthusiastic pentester and Security Analyst at Ignite Technologies. Contact Here
Remote Code Execution: Remote Code Evaluation is a vulnerability that occurs because of the unsafe handling of inputs by the server application or that can be exploited if user input is injected into a File or a String and executed by the programming language’s parser or the user input is not sanitised properly in POST request and also when accepting query string param during GET requests.
Therefore a Remote Code Evaluation can lead to a full compromise of the vulnerable web application and also a web server.
Let’s Begin!!
So the drupal is accessible through a web browser by exploring the following URL:
Code:
http://192.168.10.117/drupalAnd this opens the default home page, to access the dashboard you must-have credential for login.

So, to access the user console, I used following creds.
Code:
Username:raj
Password:123
After accessing the admin console, it was time to exploit web application by injecting malicious content inside it. Directly writing malicious scripts as web content will not give us the reverse shell of the application but after spending some time, we concluded that it requires PHP module. We, therefore, move to install new module through
.Manage>Extend>List>Install new module
You can download the PHP package for Drupal from the URL below and upload the tar file to install the new module.
Loading…
www.drupal.org

To install php module upload the tar file that was downloaded.

So, when the installation is completed, we need to enable to the added module.

Again, move to Manage > Extend >filters and enable the checkbox for PHP filters.

Now use the Pentest monkey PHP script, i.e. “reverse shell backdoor.php” to be injected as basic content. Don’t forget to add a “listening IP & port” to get a reversed connection. Continue to change the “text format to PHP” and enable the publishing checkbox. Keep the netcat listener ON in order to receive the incoming shell.
When everything is set accordingly, click the preview button and you’ll get the reverse connection over the netcat.

Hence, we got the reverse connection of the host machine.

Author: Komal Singh is a Cyber Security Researcher and Technical Content Writer, she is completely enthusiastic pentester and Security Analyst at Ignite Technologies. Contact Here