DARKTIGERZZZ
Programming Mentor
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Hey Folks, as we all know about fuzzing how important it is during bug hunting and CTF challenges but fuzzing is always the first step used to get some sensitive information like: password files, directory, vulnerable location etc. Sometimes we take help of other tool and they take more time to fuzzing against web applications and even we should have our own word list and it can time taking to do all this, hecne this tool is really amazing which will perform deep fuzzing against the web application without giving any custom word list and also in this have some unique features such as : recursive, juicy info, js-info etc from which we can enhance our results.
Lets take tool
Installation
Lets install this tool and first of all we will use git tool which will download it from github and after complete the downloading we go to the directory. We should have require dependencies on which we can start this tool, we will configure it by executing the pipe command.
git clone https://github.com/D4Vinci/CWFF.git
cd CWFF/
python3 -m pip install -r requirements.txt123git clone
https://github.com/D4Vinci/CWFF.gitcd CWFF/python3-mpip install-rrequirements.txt
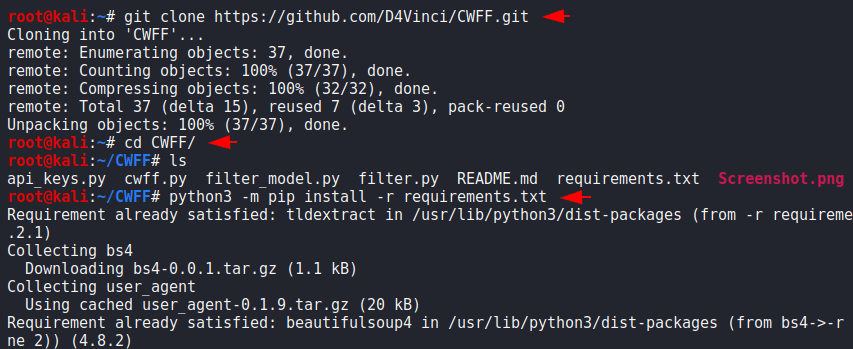
We have done the all installation and now from the given help command we can see the features of this tool.
python3 cwff.py --help1python3 cwff.py--help
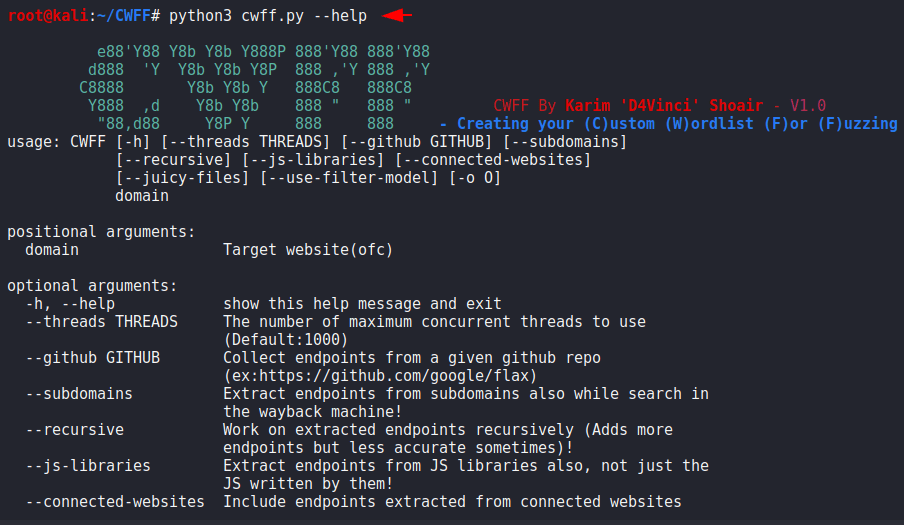
Recursive Info
In our first attempt we will try to get more information through adding the recursive feature of this tool and as you can see we have not added any wordlists below. Lets move on results.
python3 cwff.py --recursive http://testphp.vulnweb.com/1python3 cwff.py--recursive http://testphp.vulnweb.com/
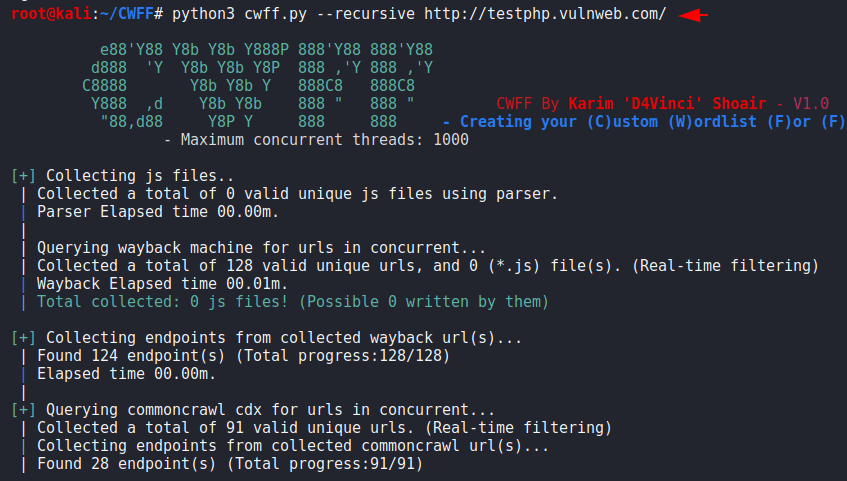
After the process is complete, the result will be saved in the directory which we gave the URL. We go to the results directory.
cd configured1cd configured
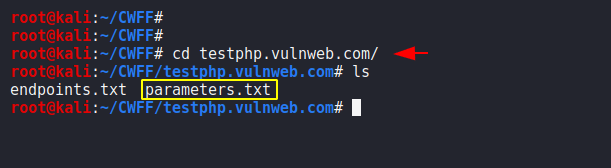
Nice
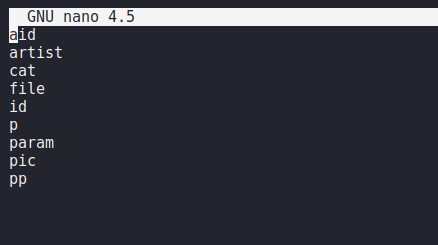
Juicy Files
With this feature we can get some juicy stuff from the endpoint and we have to execute the below command.
python3 cwff.py --juicy-files http://testphp.vulnweb.com/1python3 cwff.py--juicy-files http://testphp.vulnweb.com/
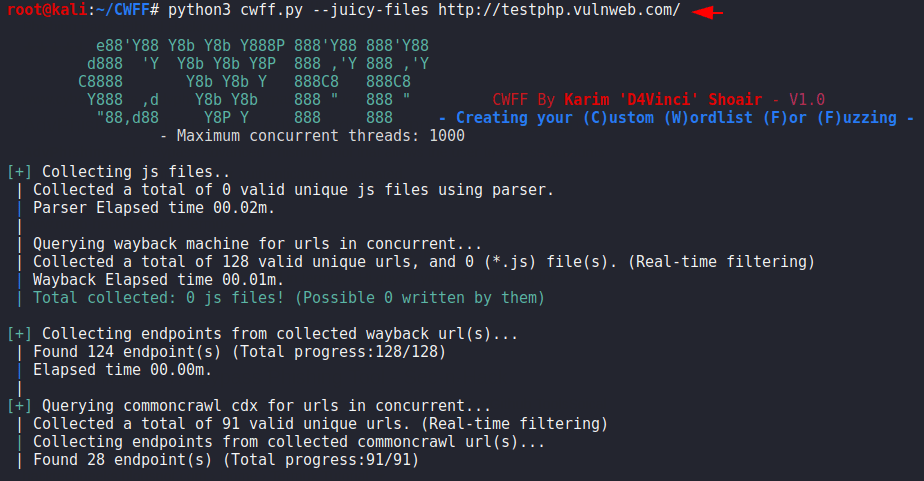
Complete Domain
The deep scan is here in which we can get almost all the hidden file, directory and location from web application. Just we will give the URL of the web application and it will get all the details and save it in the directory.
python3 cwff.py http://testphp.vulnweb.com/1python3 cwff.py http://testphp.vulnweb.com/
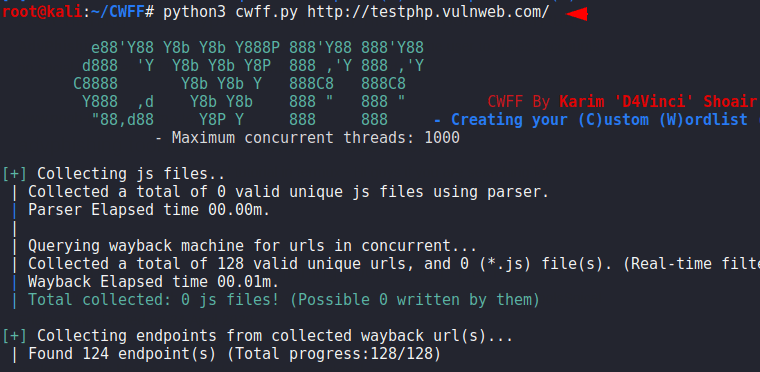
Nice
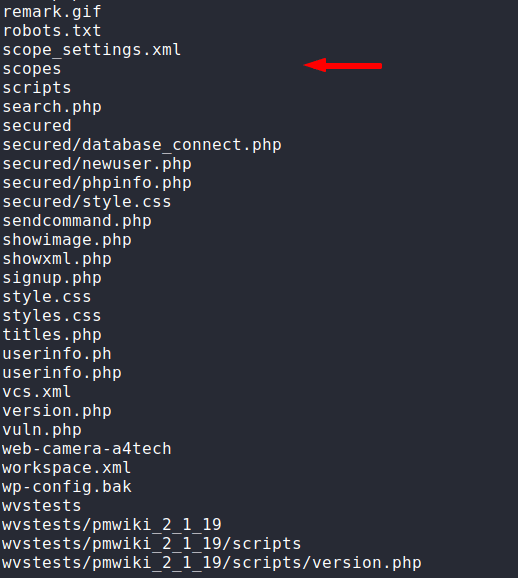
Similarly, it has some other features that you can use yourself and get more details.
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.