Vielys
Crypto Portfolio Manager
LEVEL 1
300 XP
In this article, we are going to take a new challenge CLAMP 1.0.1. The credit for making this VM machine goes to “Mehmet Kelepçe” and it’s another boot2root challenge where we have to root the server and capture the flag to complete the challenge. You can download this VM here.
Security Level: Intermediate
Penetrating Methodology:
Walkthrough:
Scanning:
Let’s start with the scanning process. This target VM took the IP address of 192.168.1.101 automatically from our local Wi-Fi network.
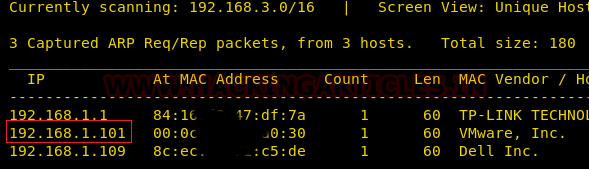
We have used Nmap for port scanning. Here, you can see that port 22 and 80 are open and both are important to us.
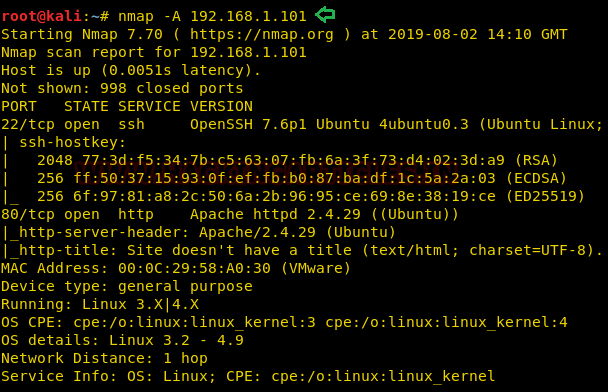
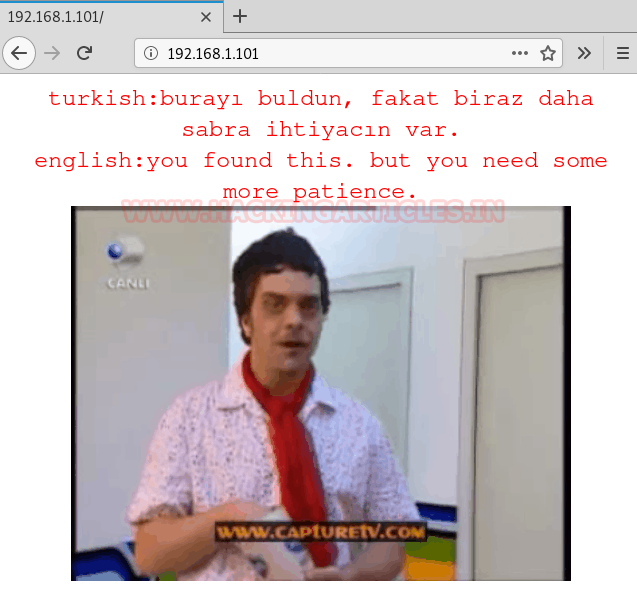
As port 80 is open, we will open the IP in our browser as shown below:
Enumeration:
Upon opening the IP in the browser, it says “you have found this. But you need more patience” both in English and in Turkish which means we need to find more things. Therefore, further we used DirBuster and we had the following results:

From the result of OWASP DirBuster, the one directory which I found useful is /nt4stopc/. And when you open this directory in the browser you will see the following page:
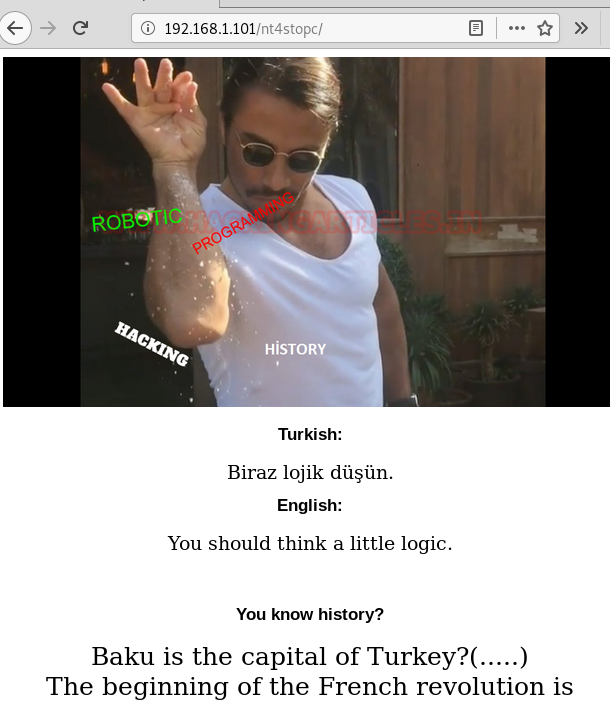
On this page, it asks you questions in the form of true and false, which here is equivalent of 0 and 1 of binary.
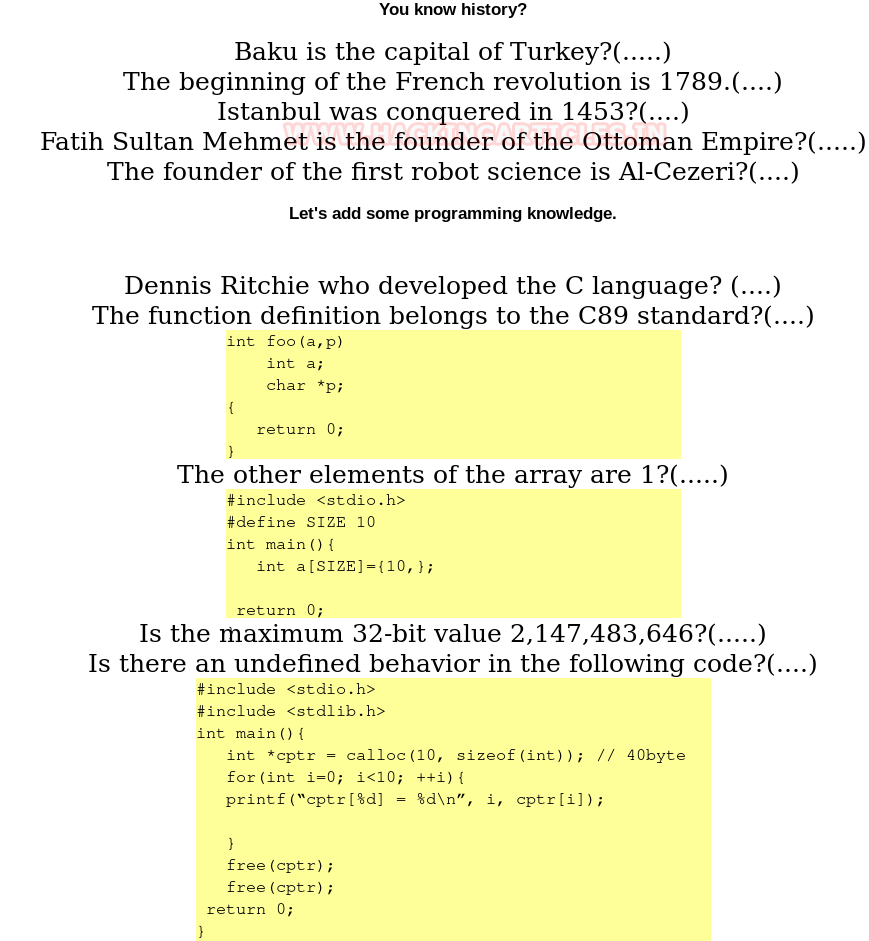
Question
True/False Bit
Baku is the capital of Turkey?
False
0
The beginning of the French revolution is 1798.
True
1
Istanbul was conquered in 1435?
True 1
Fatih Sultan Mehmet is the founder of the Ottoman Empire? False
0
The founder of robot science is Al-Cezeri?
True 1
Dennis Ritchie, who developed the C language? True
1
The function definition belongs to the C89 standard?
True 1
The other element of the array is 1?
False
0
Is the maximum 32-but value 2,147,482646? False
0
Is there an undefined behaviour in the following code? True
1
So, if you keep answering these questions you will have ‘0110111001’ binary string. Now add that binary string after the name of the directory as shown below:
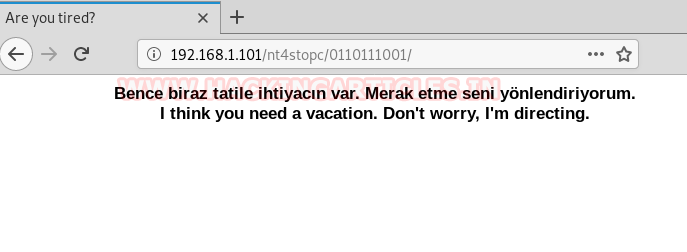
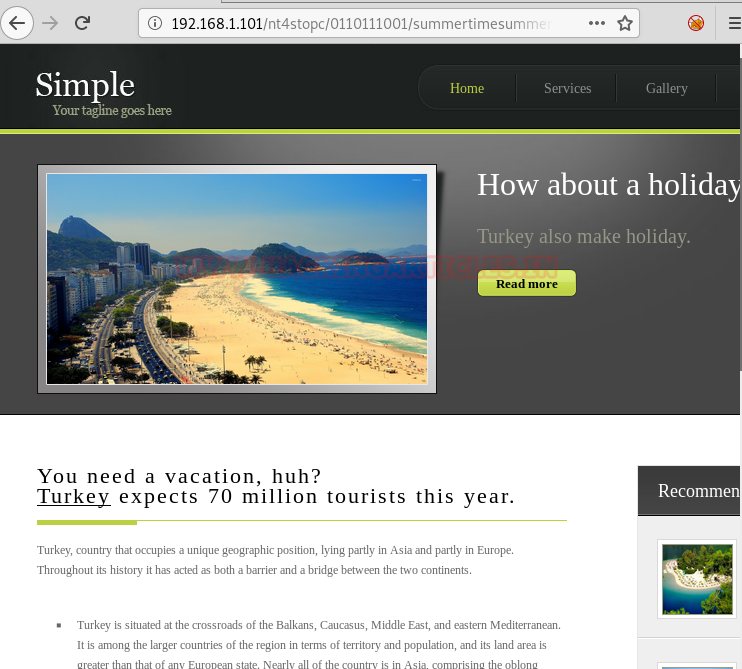
Once the above step is done, the page that opens will show a message saying “I think you need a vacation. Don’t worry, I’m directing” again both in English and Turkish. This page then redirects to a webpage showing turkey as a holiday spot as shown in the image below:
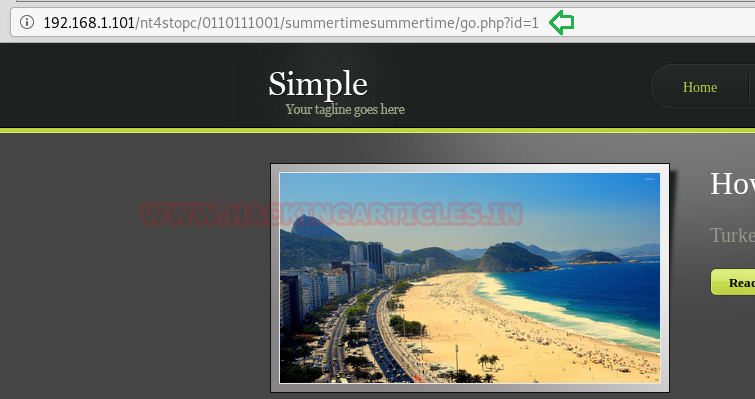
This link is vulnerable to SQL injection. We found this by simply adding ‘after id=1. And our doubt was confirmed when an error was returned.
So, to exploit SQL’s vulnerability we will use sqlmap and following will be the command:
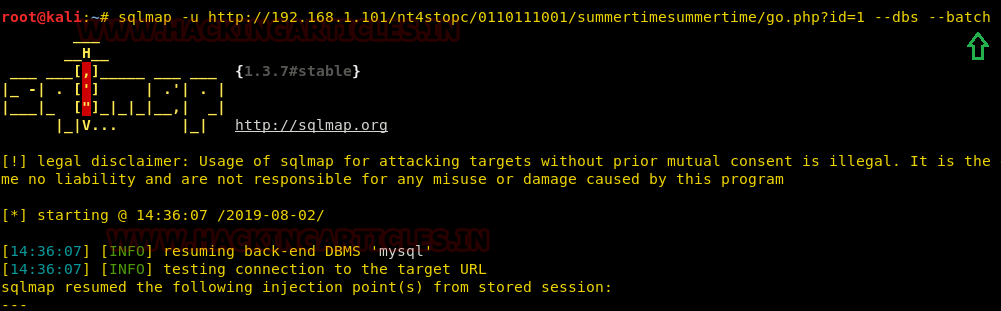
Executing the above command will provide the following result. And that’s how we got the database name i.e. tatil as shown in the image below:

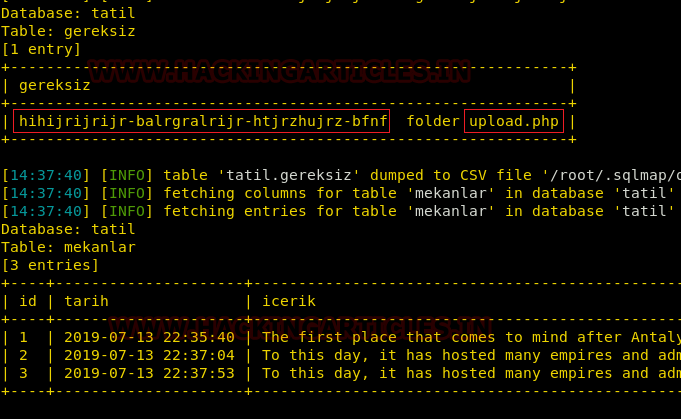
In the database, we found a string of Caesar Encryption which will lead us to upload our malware.
We decrypted the encrypted string online and it was the 13th formula of the encryption as shown in the image below:

When we add this decrypted string to the URL we are redirected to the following page:
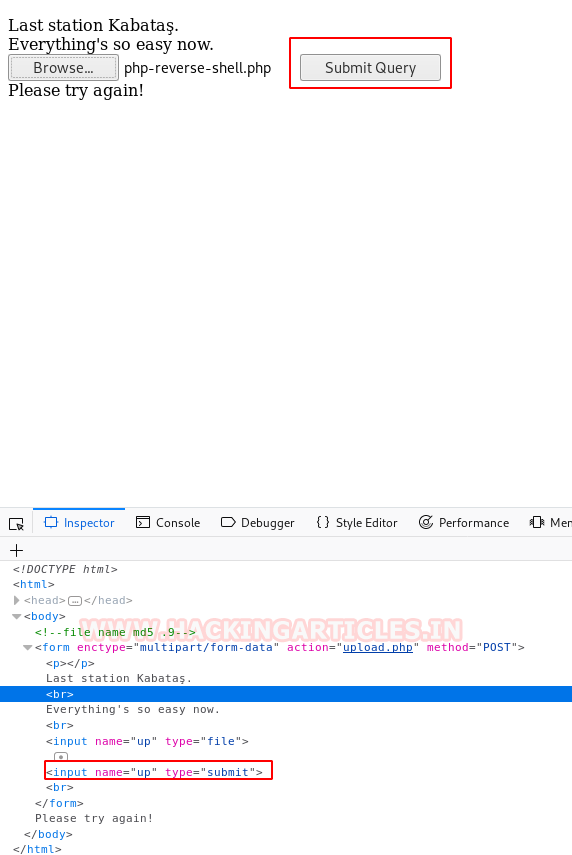
Then we opened the upload.php page to upload our malware where we found an option to browse our malware but the problem is that there is no submit button as you can see in the following image:

So firstly, we will make changes of IP and port in the php shell so that we can have the session. The changes that we made can be seen in the following image:

Now, you can browse the shell and select it.

Once the previous step is completed, it will pop a message for you telling you to try again. Now that we don’t have a submit button, it will seem like one is stuck in a pickle. But there is a simple solution to it. Right-click on the page and select ‘Inspect Element’ a window will open, from this window click on the form tag. Here, add the following line:

Doing the above changes will provide you with a ‘submit query’ button and it this button that will let us upload your shell.
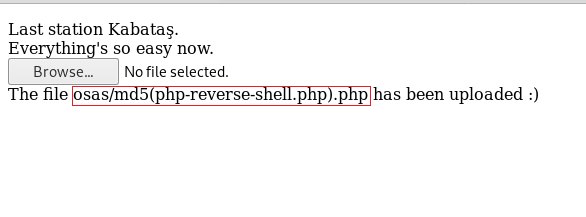
Now, once the file is upload, it will show you the message that ‘The file osas/md5(php-reverse-shell.php.php has been uploaded’. Here, please observe that the shell is being uploaded in md5 hash.
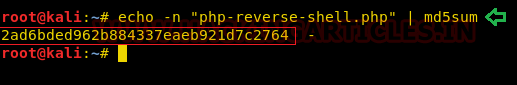
So, we calculated the md5 hash of the name of the file with the following command:
Then turn on the netcat using the following command:
And once the is executed, you will have your session. Now with the help of further enumeration, we found important.pcapng.

Now let us download the file to inspect it. To download the file simply add its name to URL and press Enter
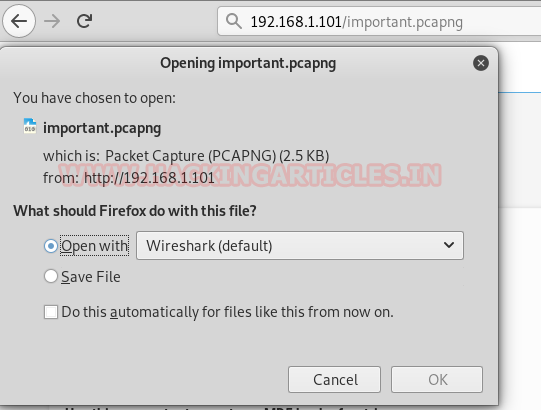
As this file is in pcapng format, open the file in Wireshark. Now if you follow the TCP Stream of the HTTP request packet, you will find password there. That too in cleartext.

Privilege Escalation
Now that we have the password, we can directly login using SSH with the following command:
Once you are logged on, go into the root directory, there you will find a flag. When you read the flag, it says that the challenges are done.

Hurray! Another CTF solved. This is a great lab with a strong focus on enumeration.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester Contact here
Security Level: Intermediate
Penetrating Methodology:
- Scanning
- Netdiscover
- NMAP
- Enumeration
- OWASP-Dirbuster
- Exploitation
- SQL Injection
- Encryption
- Modifying Webpages
- Privilege Escalation
- Exploiting Sudo rights
Walkthrough:
Scanning:
Let’s start with the scanning process. This target VM took the IP address of 192.168.1.101 automatically from our local Wi-Fi network.
Code:
netdiscover
We have used Nmap for port scanning. Here, you can see that port 22 and 80 are open and both are important to us.
Code:
nmap -A 192.168.1.101
As port 80 is open, we will open the IP in our browser as shown below:

Enumeration:
Upon opening the IP in the browser, it says “you have found this. But you need more patience” both in English and in Turkish which means we need to find more things. Therefore, further we used DirBuster and we had the following results:

From the result of OWASP DirBuster, the one directory which I found useful is /nt4stopc/. And when you open this directory in the browser you will see the following page:

On this page, it asks you questions in the form of true and false, which here is equivalent of 0 and 1 of binary.

Question
Baku is the capital of Turkey?
0
The beginning of the French revolution is 1798.
1
Istanbul was conquered in 1435?
Fatih Sultan Mehmet is the founder of the Ottoman Empire? False
0
The founder of robot science is Al-Cezeri?
Dennis Ritchie, who developed the C language? True
1
The function definition belongs to the C89 standard?
The other element of the array is 1?
0
Is the maximum 32-but value 2,147,482646? False
0
Is there an undefined behaviour in the following code? True
1
So, if you keep answering these questions you will have ‘0110111001’ binary string. Now add that binary string after the name of the directory as shown below:

Once the above step is done, the page that opens will show a message saying “I think you need a vacation. Don’t worry, I’m directing” again both in English and Turkish. This page then redirects to a webpage showing turkey as a holiday spot as shown in the image below:

This link is vulnerable to SQL injection. We found this by simply adding ‘after id=1. And our doubt was confirmed when an error was returned.

So, to exploit SQL’s vulnerability we will use sqlmap and following will be the command:
Code:
sqlmap -u http://192.168.1.101/nt4stopc/011011101/sumertimesummertime/go.php?id=1 --dbs --batch
Executing the above command will provide the following result. And that’s how we got the database name i.e. tatil as shown in the image below:

In the database, we found a string of Caesar Encryption which will lead us to upload our malware.

We decrypted the encrypted string online and it was the 13th formula of the encryption as shown in the image below:

When we add this decrypted string to the URL we are redirected to the following page:

Then we opened the upload.php page to upload our malware where we found an option to browse our malware but the problem is that there is no submit button as you can see in the following image:

So firstly, we will make changes of IP and port in the php shell so that we can have the session. The changes that we made can be seen in the following image:

Now, you can browse the shell and select it.

Once the previous step is completed, it will pop a message for you telling you to try again. Now that we don’t have a submit button, it will seem like one is stuck in a pickle. But there is a simple solution to it. Right-click on the page and select ‘Inspect Element’ a window will open, from this window click on the form tag. Here, add the following line:

Doing the above changes will provide you with a ‘submit query’ button and it this button that will let us upload your shell.

Now, once the file is upload, it will show you the message that ‘The file osas/md5(php-reverse-shell.php.php has been uploaded’. Here, please observe that the shell is being uploaded in md5 hash.

So, we calculated the md5 hash of the name of the file with the following command:
Code:
echo -n "php-reverse-shell.php" | md5sum
Then turn on the netcat using the following command:
Code:
nc -lvp 1234And once the is executed, you will have your session. Now with the help of further enumeration, we found important.pcapng.

Now let us download the file to inspect it. To download the file simply add its name to URL and press Enter

As this file is in pcapng format, open the file in Wireshark. Now if you follow the TCP Stream of the HTTP request packet, you will find password there. That too in cleartext.

Privilege Escalation
Now that we have the password, we can directly login using SSH with the following command:
Code:
Once you are logged on, go into the root directory, there you will find a flag. When you read the flag, it says that the challenges are done.

Hurray! Another CTF solved. This is a great lab with a strong focus on enumeration.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester Contact here