johncenamodz
User Retention Expert
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today, we are going to solve another boot2root challenge called “Cewlkid: 1“. It is available at VulnHub for penetration testing practices and you can download it from here.The commendation of making this lab goes to @iamv1nc3nt. Let’s start and learn how to boot it successfully.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
We are looking for the IP address of the target machine with netdiscover:
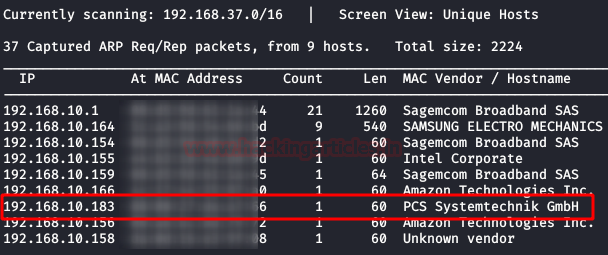
Once we have the IP address, the next step is to perform a network scan and so we will use nmap for it as shown in the following image:

Enumeration
We ignore the port 80 web service as it is useless to the aforementioned Boot2Root challenge and hop to list a Sitemagic CMS on port 8080.

We review the content and sections, we will find the link to the administration panel of the web application.
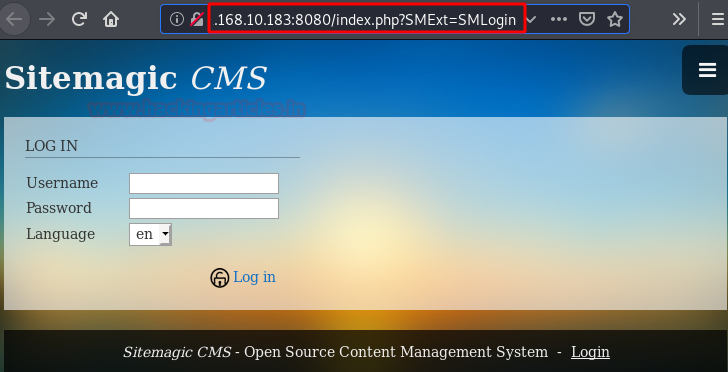
With all this information and given that the machine is called “Cewlkid“, it is very clear that we will need to create a dictionary with the tool “Cewl” using the different sections of the web to obtain the possible password.

With the help of Burp suite and using the dictionary we just created, we will perform brute force on the user “admin” (official information default user).

We access the control panel and verify that the credentials are valid.

Exploiting
Inside we can list the exact version of the application and check that there is an exploit to upload arbitrary files.
Exploit: https://www.exploit-db.com/exploits/48788
As always, we will do a proof of concept to verify that the site is vulnerable. And for that, we have captured the following request.
Request:

The response for the bove request is the follwoing:

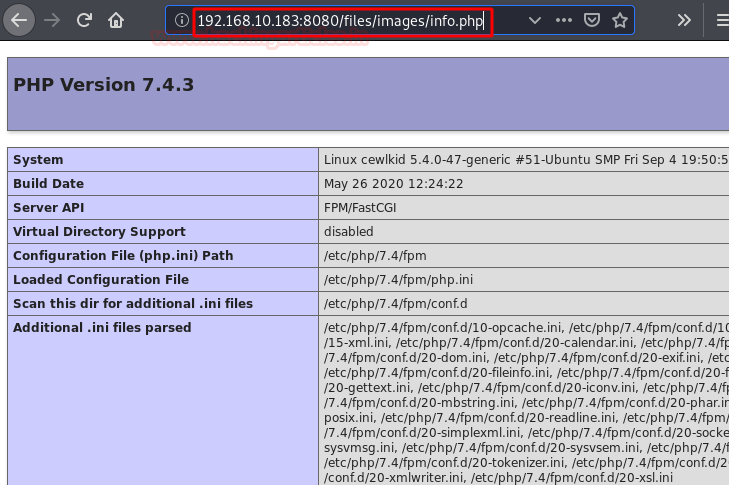
Perfect! We upload the file and see that we have indeed been able to upload the “info.php” file.
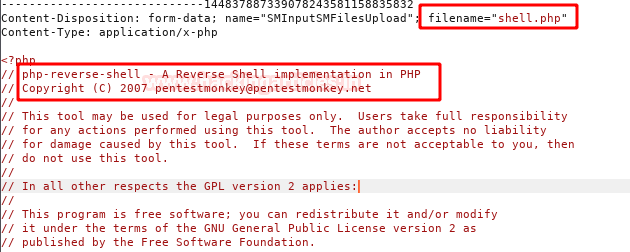
We repeat the same steps, but this time we will upload a web shell. (I used pentestmonkey’s)
We put a netcat on the wire and load our “shell.php” file. We will get access to the inside of the machine

Privilege Escalation (Cewlbeans)
There are several users in the system, but using the tool “pspy64” we enumerate that a remote connection is executed from time to time with the user “cewlbeans” where the password appears in plain text.

Privilege Escalation (root)
We authenticate with the user “cewlbeans“, execute the command “sudo -l” and we find the pleasant surprise that we can execute any binary as any user.

Let’s not waste time, we execute a /bin/sh as “root” and read the flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedInand Twitter.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
- Netdiscover
- Nmap
Enumeration
- Cewl
- Brute force login Sitemagic CMS with Burp
- Pyps64
Exploiting
- Sitemagic Arbitrary File Upload
Privilege Escalation
- Abuse crontab with plain passwords
- Abuse of sudo
- Capture the flag
Walkthrough
Reconnaissance
We are looking for the IP address of the target machine with netdiscover:
Code:
netdiscover -i ethX
Once we have the IP address, the next step is to perform a network scan and so we will use nmap for it as shown in the following image:
Code:
nmap -A –p- 192.168.10.183
Enumeration
We ignore the port 80 web service as it is useless to the aforementioned Boot2Root challenge and hop to list a Sitemagic CMS on port 8080.

We review the content and sections, we will find the link to the administration panel of the web application.

With all this information and given that the machine is called “Cewlkid“, it is very clear that we will need to create a dictionary with the tool “Cewl” using the different sections of the web to obtain the possible password.

With the help of Burp suite and using the dictionary we just created, we will perform brute force on the user “admin” (official information default user).

We access the control panel and verify that the credentials are valid.

Exploiting
Inside we can list the exact version of the application and check that there is an exploit to upload arbitrary files.
Exploit: https://www.exploit-db.com/exploits/48788
As always, we will do a proof of concept to verify that the site is vulnerable. And for that, we have captured the following request.
Request:

The response for the bove request is the follwoing:

Perfect! We upload the file and see that we have indeed been able to upload the “info.php” file.

We repeat the same steps, but this time we will upload a web shell. (I used pentestmonkey’s)

We put a netcat on the wire and load our “shell.php” file. We will get access to the inside of the machine

Privilege Escalation (Cewlbeans)
There are several users in the system, but using the tool “pspy64” we enumerate that a remote connection is executed from time to time with the user “cewlbeans” where the password appears in plain text.

Privilege Escalation (root)
We authenticate with the user “cewlbeans“, execute the command “sudo -l” and we find the pleasant surprise that we can execute any binary as any user.

Let’s not waste time, we execute a /bin/sh as “root” and read the flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedInand Twitter.