asdfasgb
Internet Pioneer
LEVEL 1
400 XP
Hey Folks, in this tutorial we are going to discuss on another wordlist generator called “BEWGor“. BEWGor is designed help with ensuring password security. BEWGor takes the simplest features of CUPP and does a very deep dive. It prompts the user for a lot more specific information, but not have all of CUPP’s capabilities. Let’s us show you some modern feature of this tool.
Features
- Vastly Increased Information Detail on Main SubjectCreate.
- Upper/Lower/Reverse variations of inputted values.
- Set upper and lower limits on output line length.
- Check that an inputted Birthday is valid.
Lets take a look
Installation
The installation of this tool is quite simple, just we need to execute the following command sequentially and it will be configured automatically without any errors. But make sure python tools is already installed on your system.
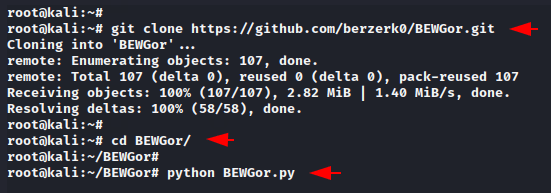
git clone https://github.com/berzerk0/BEWGor.git
cd BEWGor
python BEWGor.py123git clone
https://github.com/berzerk0/BEWGor.gitcd BEWGorpython BEWGor.py
Now it’s time to boot this tool using the last command mentioned above. After starting this tool just hit enter button to go ahead.
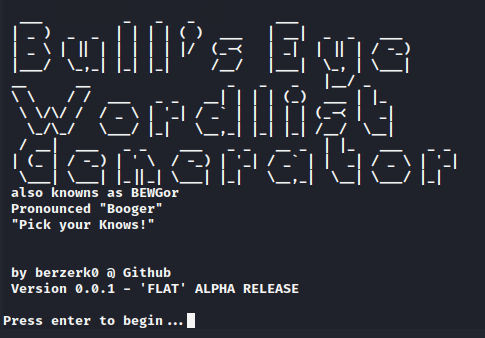
Now again we have to hit enter to jump to the main feature of this tool.
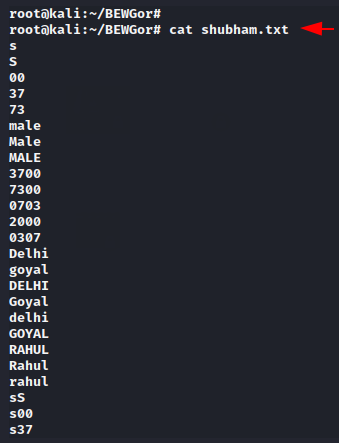
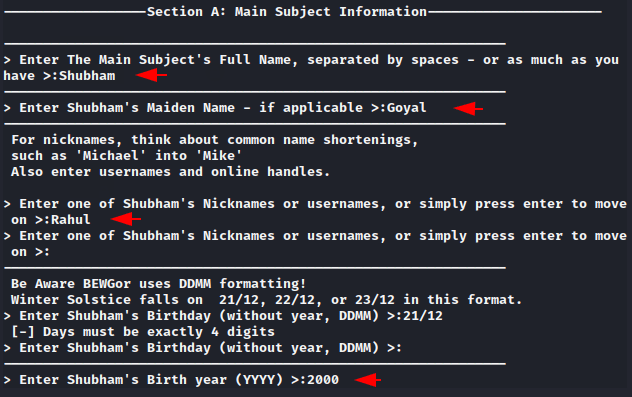
Sometimes people keep the passwords of their accounts related to their relatives, favorite pets, actors, that’s why it will ask you all the necessary FAQs and you have to enter the information that you know about him.
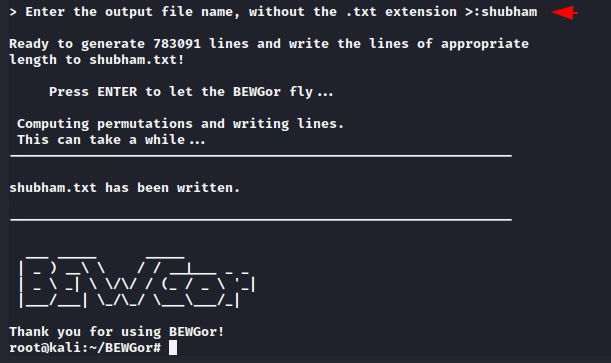
After meeting the requirements it will create a directory which we can use to perform bruteforce attack.
Great