wachcatman
Predictive Model Coder
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

Reconnaissance also known as Recon is the first step in any penetration testing , Bug hunting phase which means gathering information before any real attacks are planned. The Basic idea is to collect as much interesting information as possible about the target. Most of the time Recon phase can helps to the pen-testers to gather some sensitive data about target.Where on other hand OSINT known as Open Source Intelligence according to wikipedia is : Open-source intelligence is data collected from publicly available sources to be used in an intelligence context. In the intelligence community, the term “open” refers to overt, publicly available sources.
Table Of Content :
- Introduction To Ashok
- Installation Of Ashok
- How To Use Ashok ?
- Ashok Recon Examples
- Contributions And Conclusion
Introduction To Ashok
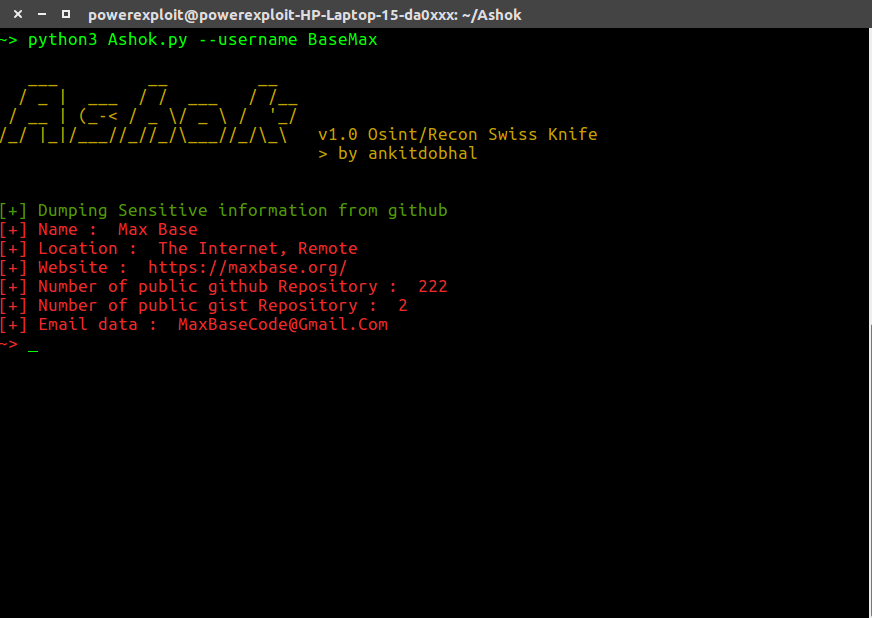
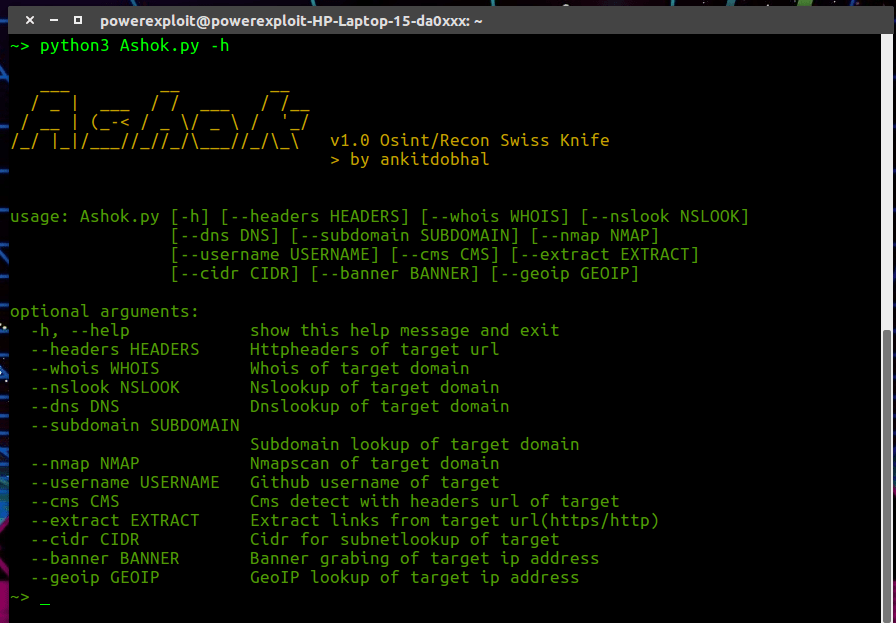
Ashok is a Osint Reconnaissance Tool Designed by Ankitdobhal in python, a.k.a swiss knife for Reconnaissance , A tool for every beginner/pentester in their penetration testing tasks.It contains several features like : http-headers extractor, dns-lookup, whois-lookup, nslookup, subdomain-finder, nmap scanning, github,githubrecon, cms-detecter, linkextractor, banner-grabbing, subnet-lookup, geoip-lookup.
Installation Of Ashok
Reference : https://github.com/ankitdobhal/Ashok
Fire up on kali linux and navigate terminal on desktop. Ashok is very simple to install with the following steps ;
git clone https://github.com/ankitdobhal/Ashok
cd Ashok
pip3 install -r requirements.txt123git clone
https://github.com/ankitdobhal/Ashokcd Ashokpip3 install-rrequirements.txt
How To Use Ashok?
After the installation you can use this tool by using following command.
python3 Ashok.py -h1python3 Ashok.py-h
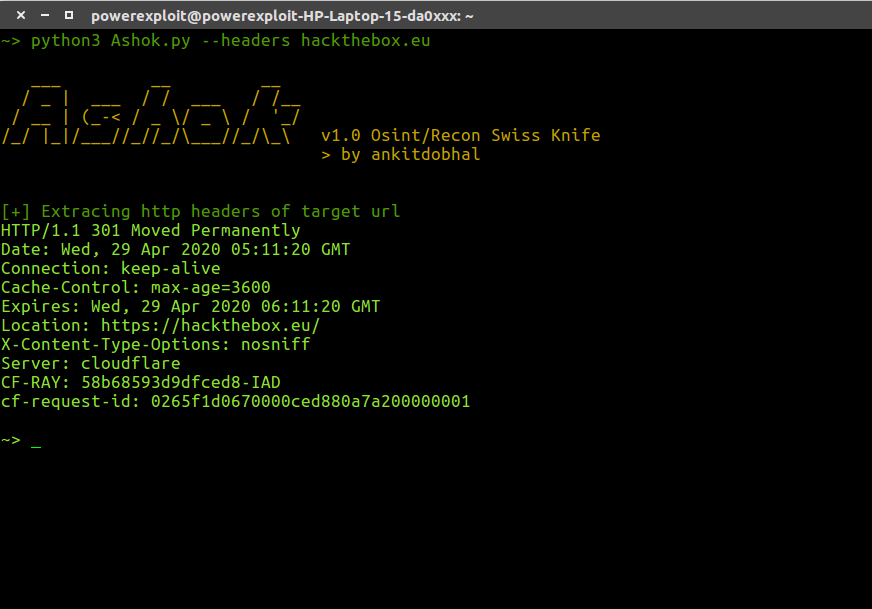
Http Headers Extractor
python3 Ashok.py --headers https://hackthebox.eu1python3 Ashok.py--headers https://hackthebox.eu
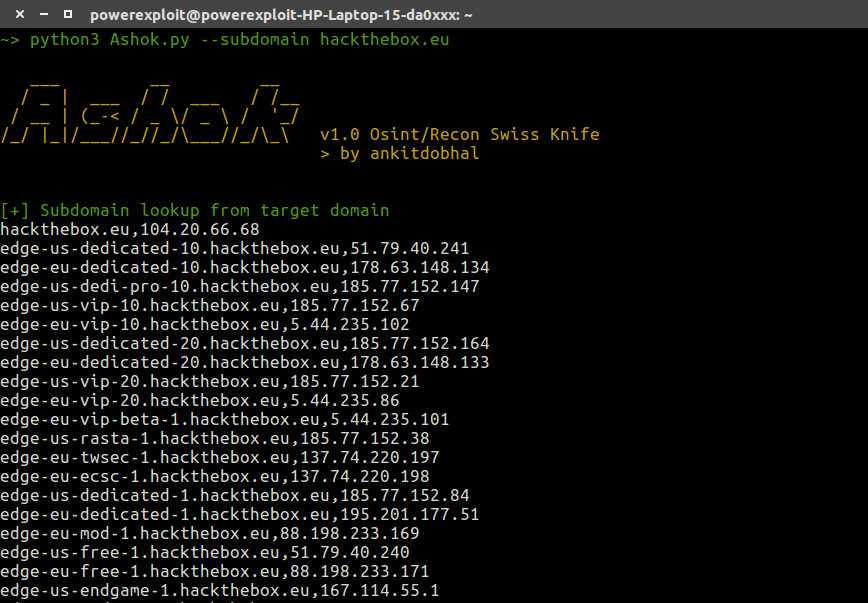
Subdomain Finder
python3 Ashok.py --subdomain hackthebox.eu1python3 Ashok.py--subdomain hackthebox.eu
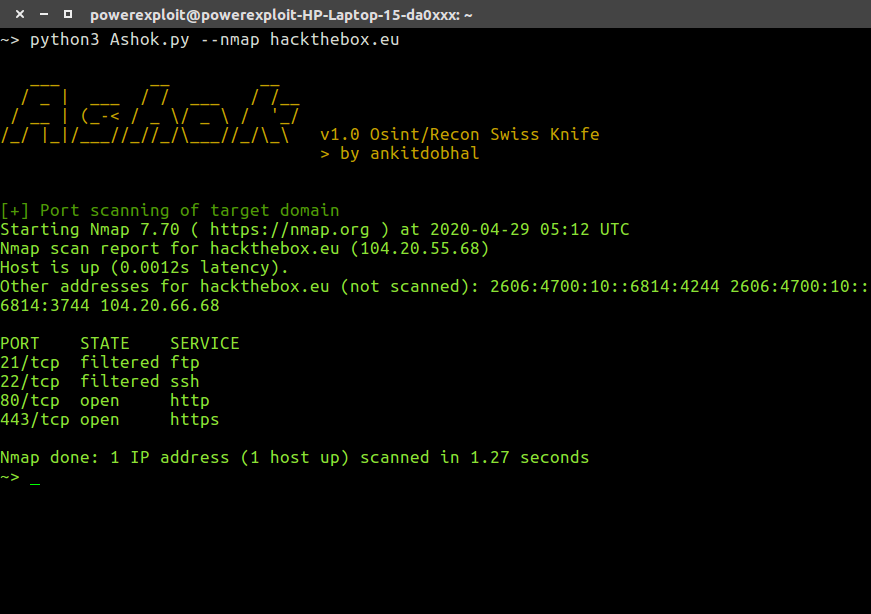
Nmap Scan
python3 Ashok.py --nmap hackthebox.eu1python3 Ashok.py--nmap hackthebox.eu
Github Recon
python3 Ashok.py --username BaseMax1python3 Ashok.py--username BaseMax