TRAPPIN
Cloud Misconfiguration Auditor
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Hey Folks, in this tutorial we will discuss an another ZIP file password cracking tool called ” Zydra”. Zydra is a file password recovery tool and Linux shadow file cracker. It uses the dictionary search or Brute force method for cracking passwords. We have simplified the features of this tool which you can read below.
Features
- In the brute force method, you can specify the type of characters that may be used in the password.
- In the brute force method, you can specify the min length and max length of the passwords.
- Cracking files password using two methods: 1. dictionary method 2. brute force method
- There is a percent progress bar showing how much of the process has been performed.
- Error handling.
Let’s take a look
Installation
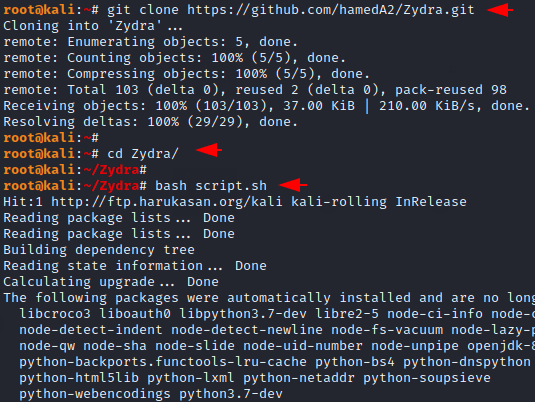
Now first we have to download this entire tool using git command from gitub. After downloading is done we will go to the directory of this tool and execute the “bash” command to establish the dependency of this tool.
git clone https://github.com/hamedA2/Zydra.git
cd Zydra/
bash script.sh123git clone
https://github.com/hamedA2/Zydra.gitcd Zydra/bash script.sh
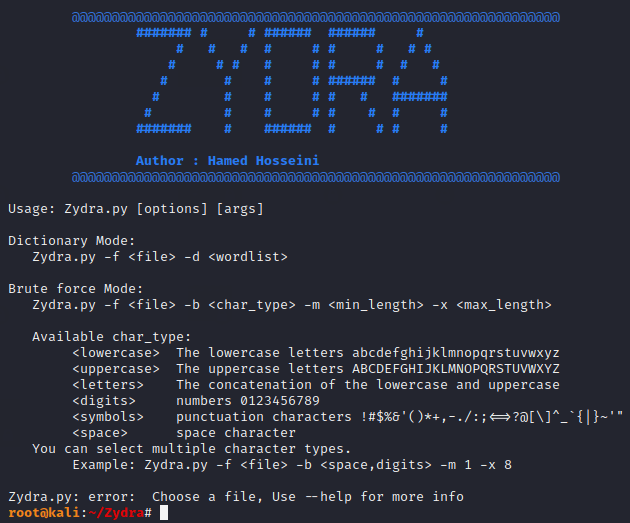
After completing the installation we can boot this tool with the help of “python” command. No need to execute help command as it will automatically show all its attributes after executing the following command.
python3 Zydra.py1python3 Zydra.py
Create ZIP file
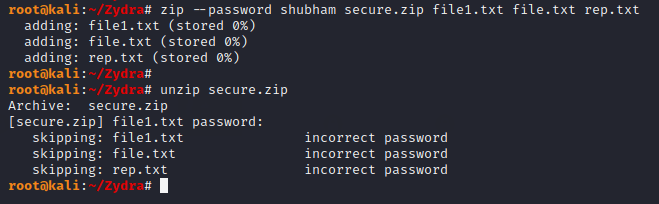
We have to make a password protected zip file in front of you to maintain transparency between us. Do not think so, just use the following command to create a zip file.
Usage
zip --password shubham secure.zip file1.txt file.txt rep.txt1zip--password shubham secure.zip file1.txt file.txt rep.txt
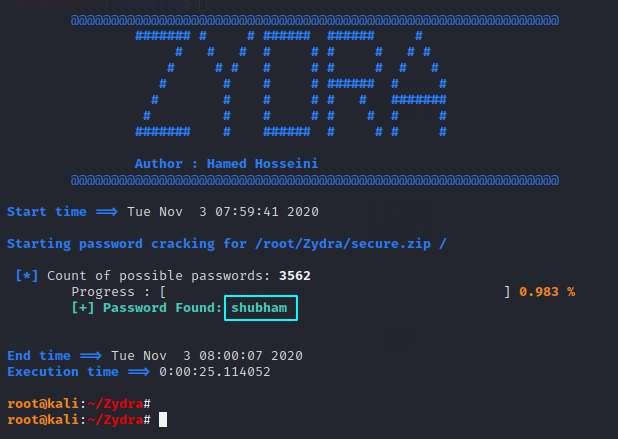
Password Cracking via Dictionary Attack
This gives us two options, dictionary and brute force. First we select the dictatorial attack and as you can see we have our own wordlist to crack the zip file password that we mentioned in the command. After giving the location of zip file and wordlist, it successfully finds a valid password for the zip file.
Usage
python3 Zydra.py -f secure.zip -d password.lst1python3 Zydra.py-fsecure.zip-dpassword.lst
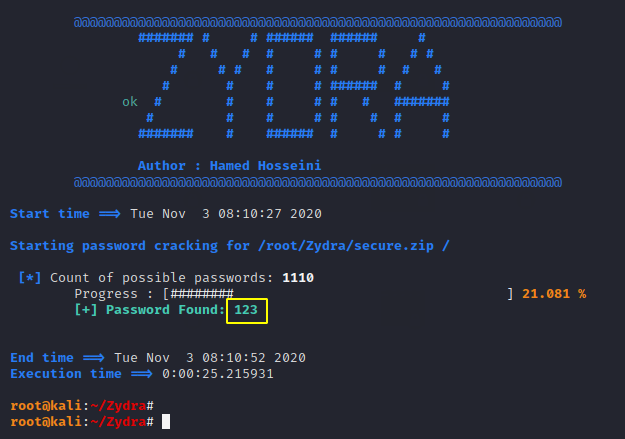
Password Cracking via Bruteforce Attack
We have created a numeric password protected zip file with the help of the previous command and now we have to crack the password of this zip file. You need to understand to use the below command. In this case we will take help of brute forcing and use the following command to crack the password.
Usage
python3 Zydra.py -f secure.zip -b digits -m 1 -x 31python3 Zydra.py-fsecure.zip-bdigits-m1-x3
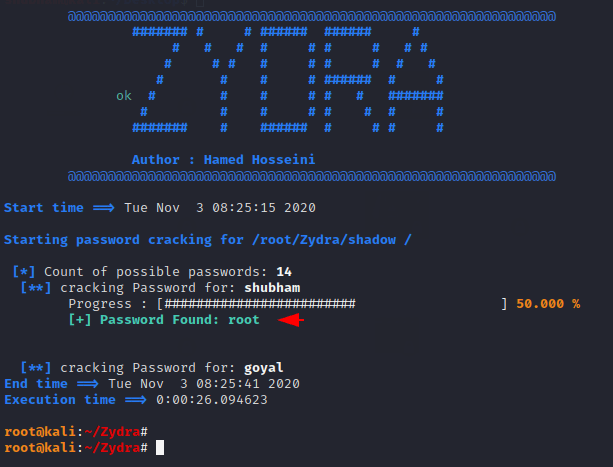
Cracking Shadow Files
Zydra can automatically crack the password or hashes of users found in Linux shadow files but it will totally depends on your dictionary.
python3 Zydra.py -f shadow -d wordlist.txt1python3 Zydra.py-fshadow-dwordlist.txt