hep3333
SMM Efficiency Guru
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Today we are going to solve another boot2root challenge called “CyberSploit: 1”. It’s available at Vulnhub for penetration testing. This is an easy level lab. The credit for making this lab goes to cybersploit1. Let’s get started and learn how to successfully break it down. Level: Easy
Since these labs are available on the Vulnhub website. Let’s download the lab file from here.
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
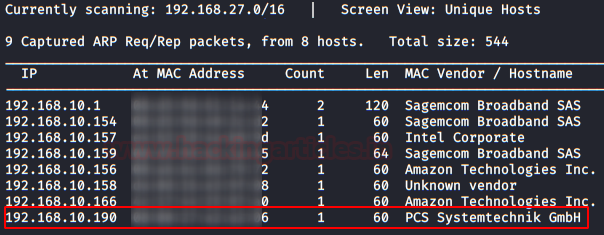
As always we identify the host’s IP with the “Netdiscover” tool:
So, let’s start by listing all the TCP ports with nmap.

To work more comfortably, I’ll put the IP address in /etc/hosts.

Enumeration
We access the web service and review the source code. We find the SSH user name.

It’s time to fuzzing! We used Gobuster and found several files. We examined the robots.txt and found a base64 text.

Exploiting
We use curl and add “base64 -d” to the command to decode the message in plain text. We get the first flag, the flag is the user’s password “itsskv“.

We access with the obtained credentials and read the file “flag2.txt“. Inside, we find a new code, this time it’s “binary code“.

We use the online tool “Cyberchef” and we get the second flag.

Privilege Escalation (root)
The root is quite simple (as the creator of the machine said it was easy level). The machine has a kernel vulnerable to “overlayfs: Local Privilege Escalation“.We download the exploit, compile it on the victim machine and run it. We get a root prompt and read our flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networksContacted on LinkedIn and Twitter.
Since these labs are available on the Vulnhub website. Let’s download the lab file from here.
Penetration Testing Methodology
Reconnaissance
- Netdiscover
- Nmap
Enumeration
- Gobuster
Exploiting
- Basic Cryptography
- CyberChef
Privilege Escalation
- Local Privilege Escalation ‘Overlays’
- Capture the flag
Walkthrough
Reconnaissance
As always we identify the host’s IP with the “Netdiscover” tool:
Code:
netdiscover
So, let’s start by listing all the TCP ports with nmap.
Code:
nmap –sV -sC -p- 192.168.10.190
To work more comfortably, I’ll put the IP address in /etc/hosts.

Enumeration
We access the web service and review the source code. We find the SSH user name.

It’s time to fuzzing! We used Gobuster and found several files. We examined the robots.txt and found a base64 text.

Exploiting
We use curl and add “base64 -d” to the command to decode the message in plain text. We get the first flag, the flag is the user’s password “itsskv“.

We access with the obtained credentials and read the file “flag2.txt“. Inside, we find a new code, this time it’s “binary code“.

We use the online tool “Cyberchef” and we get the second flag.

Privilege Escalation (root)
The root is quite simple (as the creator of the machine said it was easy level). The machine has a kernel vulnerable to “overlayfs: Local Privilege Escalation“.We download the exploit, compile it on the victim machine and run it. We get a root prompt and read our flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networksContacted on LinkedIn and Twitter.